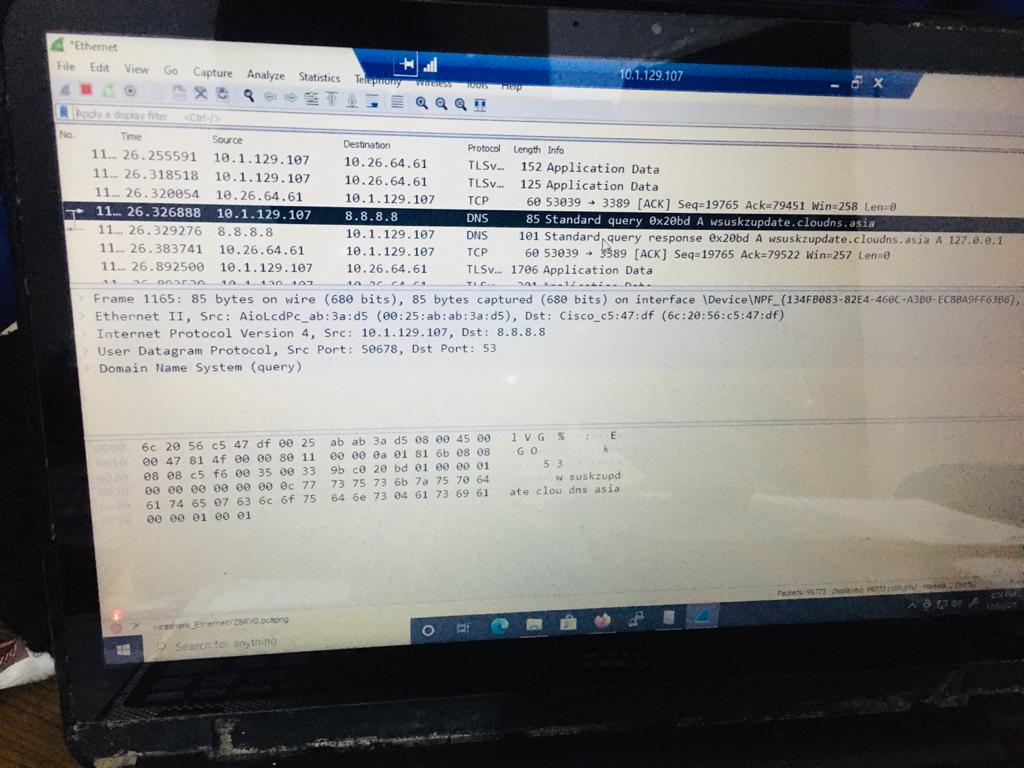
Hi ,
Please understand, Packetbeat is a third-party tool which we are not familiar with it. You can use Wireshark or network monitor to collect network traces and get more details about the source of those queries.
You can download network monitor via following link:
https://www.microsoft.com/en-sg/download/details.aspx?id=4865
For how to collect data using Network Monitor, you can refer to the following artilce:
https://learn.microsoft.com/en-us/windows/client-management/troubleshoot-tcpip-netmon
Best Regards,
Candy
--------------------------------------------------------------
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.