Thank you to lextm for providing the answer.
Sharing the context of the answer here in case it were ever to be removed from Stack Overflow.
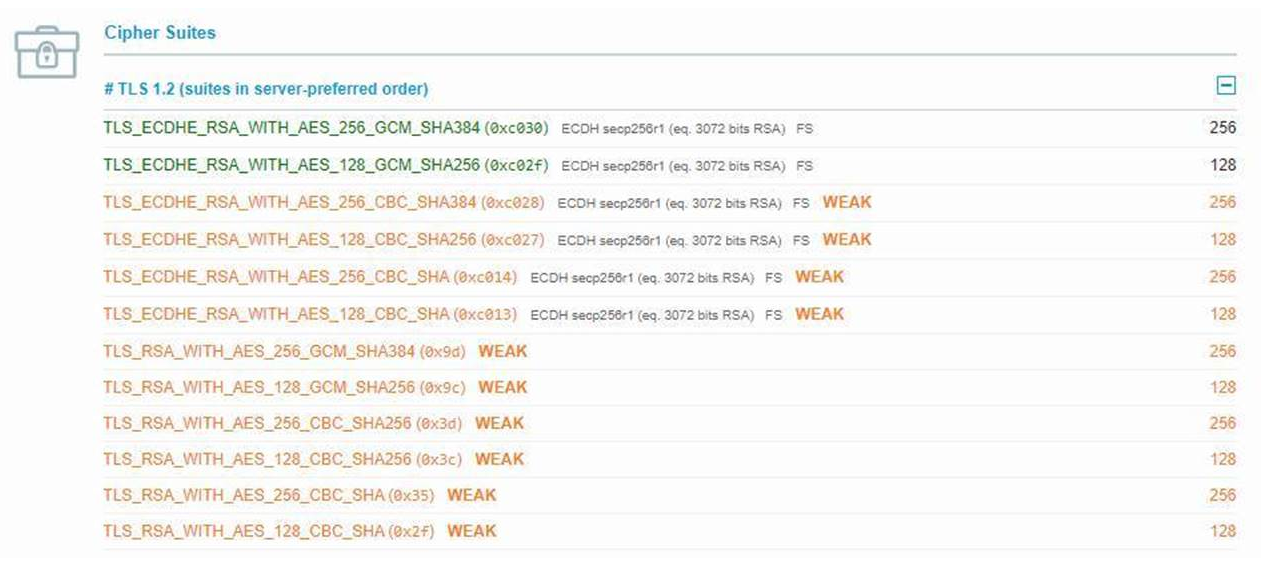
For now, there are 3 possible ways to remove weak ciphers:
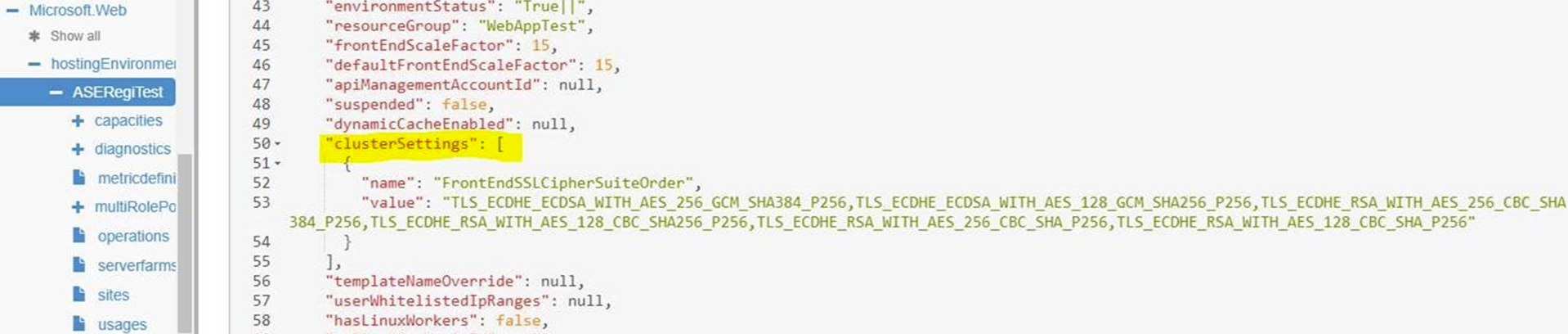
App Service Environment - This gives you access to set your own ciphers though Azure Resource Manager - Change TLS Cipher Suite Order. I reproduced this and found out that it is possible to set your own ciphers or change the cipher suite order by modifying the clusterSettings as shown below:
Using Azure FrontDoor – You can configure a minimum TLS version in Azure Front Door in the custom domain HTTPS settings via Azure portal. Once you configure TLS1.2, only the following strong cipher suites are supported:
TLS_ECDHE_RSA_WITH_AES_256_GCM_SHA384
TLS_ECDHE_RSA_WITH_AES_128_GCM_SHA256
TLS_DHE_RSA_WITH_AES_256_GCM_SHA384
TLS_DHE_RSA_WITH_AES_128_GCM_SHA256
You can find more information on this here - Front Door TLS Configuration.
Using Application Gateway – This lets you specify a central TLS policy that's suited to organizational security requirements and helps to meet compliance requirements. The TLS policy includes control of the TLS protocol version as well as the cipher suites and the order in which ciphers are used during a TLS handshake as seen here - Application Gateway SSL Policy Overview
Source: https://stackoverflow.com/questions/61927334/azure-app-service-how-to-disable-weak-ciphers
Credit to cobethur