Hello Matthew Nakama,
Greetings! Welcome to Microsoft Q&A Forum.
Yes, you can store and manage the encryption keys via Azure Key Vault. The article one describes in depth how customer managed keys work, whereas the article second does the same for customer provided keys.
When you use a customer manager key you are indicating a key stored in Azure Key Vault that you want to use to encrypt/decrypt data in a storage account.
Under the hood, this key will be used to encrypt/decrypt the key that in turn will be used to actually encrypt/decrypt the data in your storage account.
This process will be performed transparently every time you interact with your storage account.
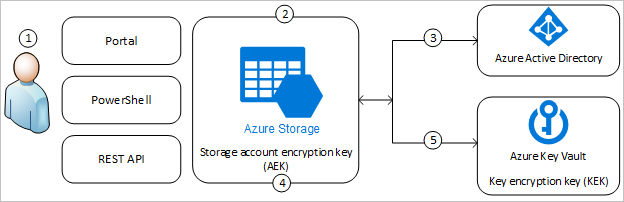
The following list explains the numbered steps in the diagram:
- An Azure Key Vault admin grants permissions to encryption keys to a managed identity. The managed identity may be either a user-assigned managed identity that you create and manage, or a system-assigned managed identity that is associated with the storage account.
- An Azure Storage admin configures encryption with a customer-managed key for the storage account.
- Azure Storage uses the managed identity to which the Azure Key Vault admin granted permissions in step 1 to authenticate access to Azure Key Vault via Azure AD.
- Azure Storage wraps the account encryption key with the customer-managed key in Azure Key Vault.
- For read/write operations, Azure Storage sends requests to Azure Key Vault to unwrap the account encryption key to perform encryption and decryption operations.
When using customer provided keys, you need to provide the encryption key itself among certain metadata you want to use for encrypting/decrypting data when reading or writing your blob data, when performing your requests:
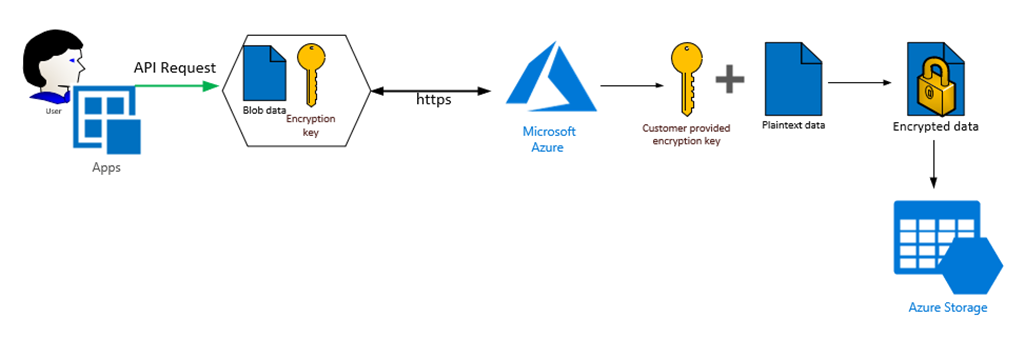
Hope this will help. Please let us know if any further queries.


