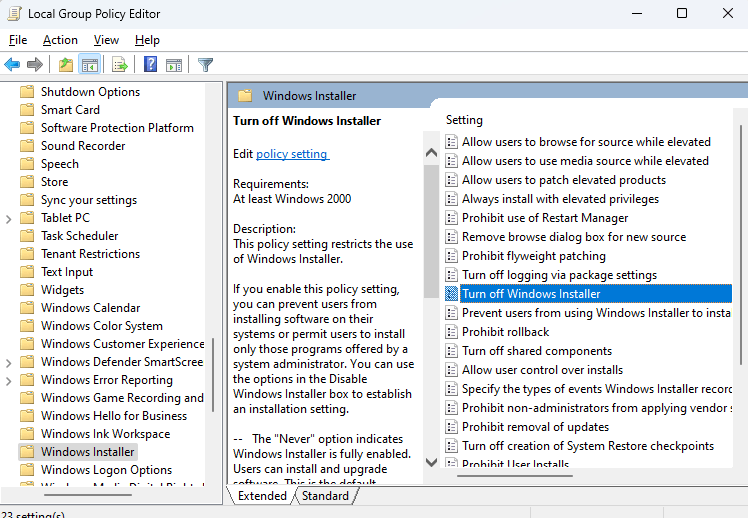
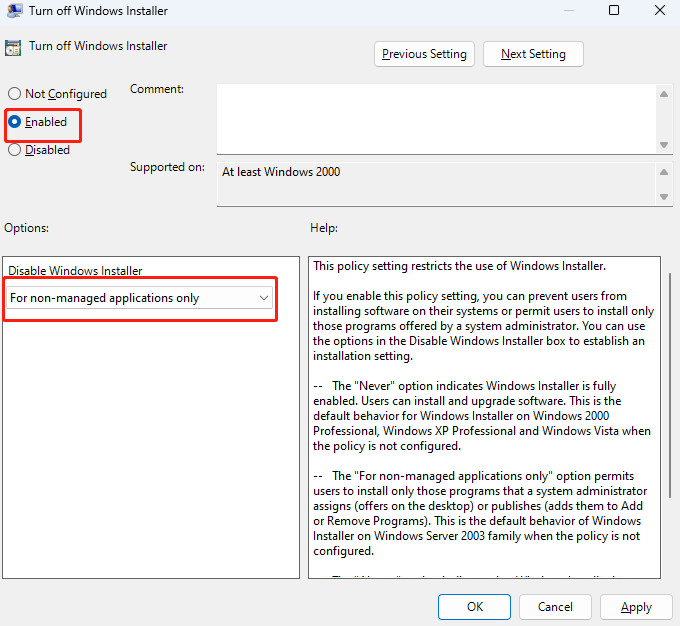
How is this a security issue? Users have always been able to install applications on their own accounts unless you block them from installing apps via GP. For years a user has been able to install per-user applications without admin privileges.
A per-user app runs in the context of the user and therefore has no more privileges to the system then the user normally would have. For example any user can install the per-user instance of Chrome or per-user instance of Azure Data Studio. This is no different than the user downloading a ZIP file with an EXE inside it and then running the EXE. The EXE has no rights that the user couldn't already do and therefore is not a security vulnerability.
Apps downloaded from the MS Store are even more locked down. In general they run in a sandbox and only have the rights that are granted to them by the user, who themselves are limited by their user account rights. Again, not a security vulnerability at all.
From a vulnerability point of view, a user doing something manually, such as creating a file or replacing something on their desktop, or a program doing it for them has the same security risks.
As Zunhui Han mentioned, if you don't want user to be able to install anything and/or only run apps that you approve then there are GP policies for that. Additionally you can configure Windows to only allow apps to be installed via the MS Store using the Apps \ Advanced app settings UI.