@Subramanyam k
Thank you for your post! I'm glad to hear that everything is working as expected when you're using the "/tenant" endpoint within your Authorization URL. When it comes to the "/common" endpoint, it's working as expected. You aren't receiving your TOU because, it's not a tenant and is not an issuer, it’s just a multiplexer.
For example:
With a multi-tenant application, the application doesn’t know up front what tenant the user is from, so you can’t send requests to a tenant’s endpoint. Instead, requests are sent to an endpoint that multiplexes across all Azure AD tenants, i.e. "https://login.microsoftonline.com/common". When Microsoft identity platform receives a request on the /common endpoint, it signs the user in and, as a consequence, discovers which tenant the user is from. For more info.
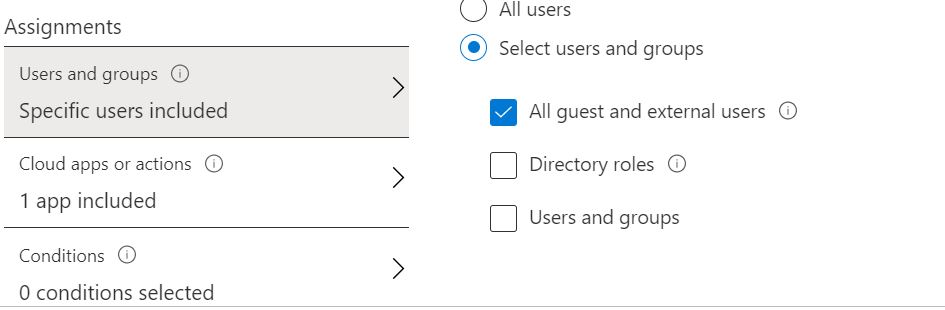
For All guest and external users, this selection includes any B2B guests and external users including any user with the user type attribute set to guest. This selection also applies to any external user signed-in from a different organization like a Cloud Solution Provider (CSP). For more info.
For a complete breakdown of Conditional Access Policies.
I hope this helps!
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.