Hi @kumar · Thank you for reaching out.
When a member user of tenant X consents for multitenant App registered in tenant Y, the consent information is stored in user's tenant i.e., tenant X in this case. Once a user accepts the consent, a service principal gets created in his tenant and this information can be found under that service principal. To see the information you need to navigate to below location in tenant X:
Azure Active Directory > Enterprise Applications > Search with App ID or App Name under All Applications > Open the app > Click on Permissions blade
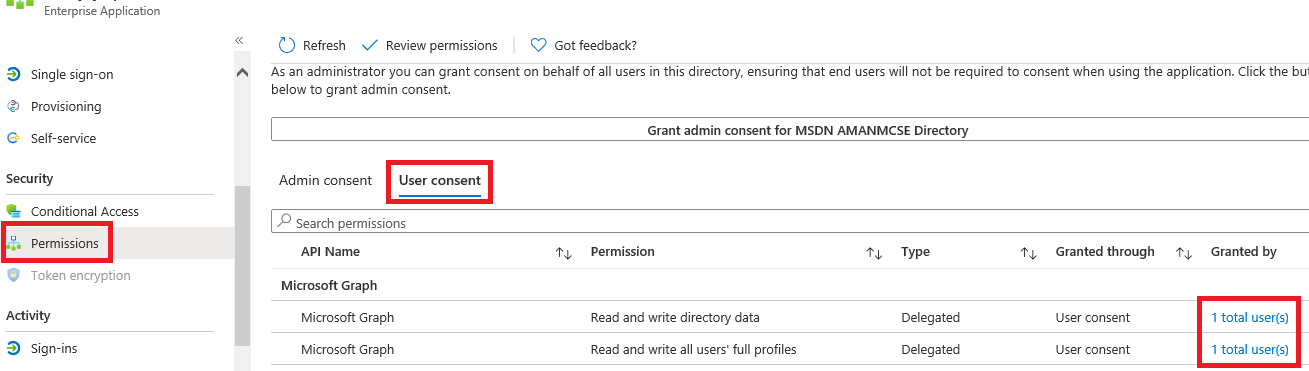
By clicking on the link under Granted by, you can see all the users who have consented for the given permission.
You can use Get-AzureADOAuth2PermissionGrant PowerShell cmdlet for this purpose as well.
Where can we see the consent logs of invited users incase of app registered as personal account?
We recommend not to use 'common' endpoint (https://login.microsoftonline.com/common), as personal accounts cannot provide admin consent except in the context of a tenant. To ensure best compatibility with personal accounts that manage tenants, use the tenant ID when possible. Permission will be saved in the tenant, whose tenant ID you specify in the request e.g. https://login.microsoftonline.com/tenantX.onmicrosoft.com.
This is documented in tenant parameter under Request the permissions from a directory admin.
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.
