After several tries of copy/paste the Workspace ID/Key, I was finally ableto connect to my Workspace.
Solved it myself.
david
This browser is no longer supported.
Upgrade to Microsoft Edge to take advantage of the latest features, security updates, and technical support.
Hi,
I have a member server in a DMZ zone. MMA is installed. I would like to pass the data collected from the OMS agent to an OMS Gateway server and then to the Log Analytics Workspace.
On the DMZ zone member server:
OMS Gateway:
When I go to the Log Analytics Workspace, I do not see the agent from the DMZ server.
Question: Does my DMZ server first have to be able to reach the Log analytic Workspace before it can be able to pass its data collection to the OMS Gateway? This would require I open port 443.
Why isn't the DMZ server visible in the Analytics Workspace?
Any ideas or suggestions would be greatly appreciated.
David
After several tries of copy/paste the Workspace ID/Key, I was finally ableto connect to my Workspace.
Solved it myself.
david
Hi Swathi,
The DMZ server is running Windows Server 2012 R2 DataCenter.
.Net Framework verison = 4.5.51641
Since the server is in our DMZ zomne, it has no connection to the Internet. Therefore, it cannot reach the Log Analytics Workspace.
As mentioned, when selecting the Microsoft Monitoring Agent | Azure Log analytics (OMS) tab, the Status Displays:
"The agent could not authenticate with the Microsoft Operations Management Suit service. Please check that the Workspace Key is correct".
On the Proxy Settings tab, I added the Use a proxy server: <OMS Gateway IP address>:8080
I ask again: Does my DMZ server first have to be able to reach the Log analytic Workspace before it can be able to pass its data collection to the OMS Gateway?
When I restart the Microsoft Monitoring Agent on the DMZ server, on the OMS Gateway, I see the following event in the OMS Gateway event log:
Client: <DMZ Server IP>
ClientID: 52fcd878-8398-47de-b16e-a101a0830622
Gateway: <OMS Gateway IP>
My Log analytics Workspace does not show the DMZ server.
david
@David Werner Regarding your question, you needn't connect your DMZ server directly to Log Analytics workspace before sending data to Log analytics Gateway. Also kindly note, after successful connection to Log Analytics workspace via Log analytics Gateway, the DMZ server will be shown as connected in Azure Portal.
I would recommend you to check below steps and if you are still facing issue, I would suggest you to raise Support Ticket with Azure Technical team by the following these steps for deeper analysis of the issue.
Hi Swathi,
I ran TestCloudconnection.exe. Results are:
Starting Azure Log Analytics connectivity test.
Proxy Configuration: 10.139.40.24:8080
Starting connectivity test for workspace id "710ebefe-d4d1-4d56-8654-0ff28f78b5ce".
This test may take several minutes to complete if a firewall is blocking access.
Making initial connection to 710ebefe-d4d1-4d56-8654-0ff28f78b5c.oms.opinsights.azure.com.
This is to download the list of Azure resources neccesary for communication with this specific workspace.
Connection was made to Azure for host list download. However, the Log Analytics service reported the error: "The workspace key was invalid."
If I run TestCloudConnection.exe on a server which is NOT in the DMZ, it returns almost the same results. In addition, it returns:
Successful Connections
Firewall Rule: *.blob.core.windows.net
aoiweu201510151571.blob.core.windows.net
opinsightsweuomssa.blob.core.windows.net
scadvisorcontent.blob.core.windows.net
But, as you mentioned, when using an OMS Gateway, my DMZ server doesn't require direct access to the Log Analytics Workspace.
Interesting that my DMZ server and non-DMZ server both have results "The workspace key was invalid.". And the non-DMZ can be seen on the Log analytics Workspace.
My OMS Gateway does report in its event log the following:
Client: <DMZ Server IP>
ClientID: 52fcd878-8398-47de-b16e-a101a0830622
Gateway: <OMS Gateway IP>
Any other recommendations? Is there a way to turn on any additonal debugging to provide more information?
david
Hi Swathi,
the non-DMZ servers shows:
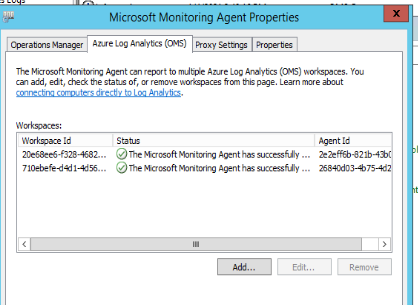
The DMZ MMA s erver shows:
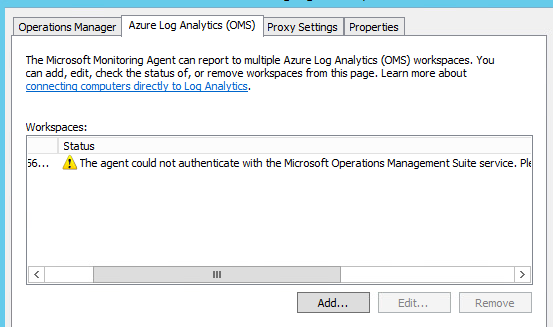
david