Hello,
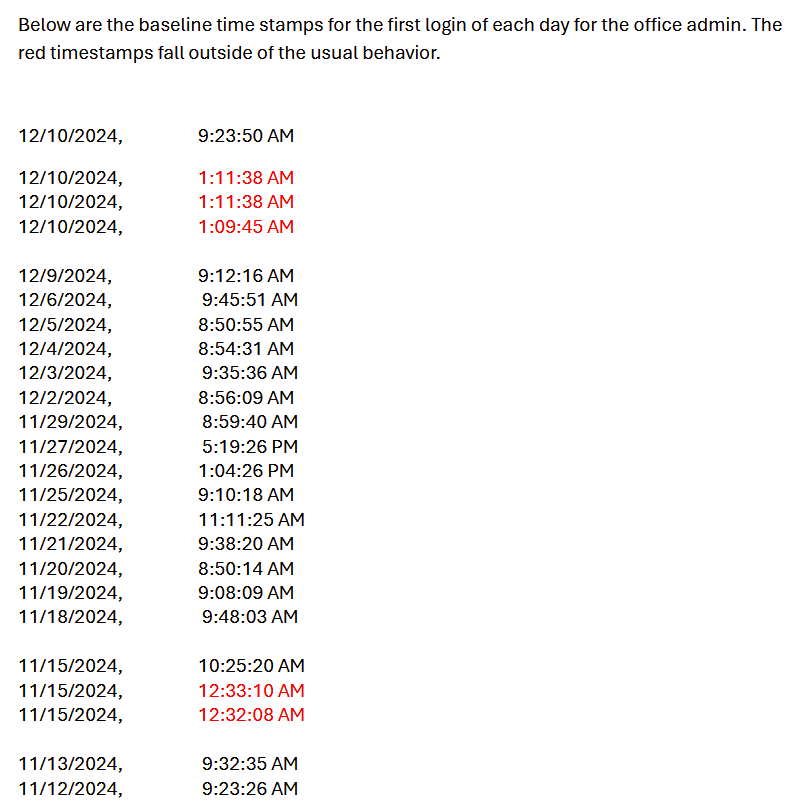
We have detected abnormal sign-in activity that raises some concerns. One of our admins successfully logged in at 1:10 AM, but she stated in an email that it was not her. Although we have Multi-Factor Authentication (MFA) enabled for all users, the authentication method was marked as "previously satisfied" for both the first-factor requirement and the MFA requirement. This indicates that the authentication was completed in a prior session or within the token's validity period.
Upon further investigation, I found that the admin's session ID has remained unchanged for the past 30 days. This suggests that she does not log out at the end of the day or log in each morning. I confirmed this with her and other office admins, who typically work on Microsoft 365 desktop applications without logging in and out daily. When I look at remote users, they have a new session ID every day they log in.
Microsoft does not recommend signing out of Office applications. According to their guidelines:
"As a Microsoft 365 subscriber, your Office apps are activated when you sign in. We recommend that you stay signed in so you can continue to create and edit files, view your recent files, and save new and updated files to OneDrive. Signing out is not recommended unless another person wants to use this installation of Office."
However, Microsoft also advises implementing an idle session timeout for Microsoft 365. This feature automatically logs users out after a set period of inactivity, which helps protect sensitive company data and adds an extra layer of security for end users who work on non-company or shared devices. When a user reaches the idle timeout you’ve set, they receive a notification indicating that they are about to be signed out. They must select an option to stay signed in; otherwise, they will be automatically signed out of all Microsoft 365 web apps.
Here are my questions:
- If our office admins are using desktop applications within our brick-and-mortar office network, do they need to sign in and out of office.com every day?
- If our office admins access Microsoft 365 SaaS via the browser while inside our office network, do they need to sign in and out of office.com every day?
- Why do I see sign-in logs each day for users with applications such as "Office 365 Shell WCSS-Client," "Office Online Core SSO," "Office SharePoint Online," "SharePoint Online Web Client," and "Office Delve"? All these applications are showing as "browser" in the client app column of the Entra ID sign-in logs.
I am trying to determine if our admin account is compromised or if the refresh tokens automatically logged her in at 1 AM under the interactive sign-in logs without her knowledge.
Please note the blue highlight successful sign-ins were not initiated by the user and she states this was not her. No other logs for the past month show her signing in at 1 AM in the morning.

Thank you for your assistance.

