Hello Steve March1,
Thank you for your reply.
The issue you mentioned one problem that are difficult to troubleshoot or solve. However, you can try to check information below.
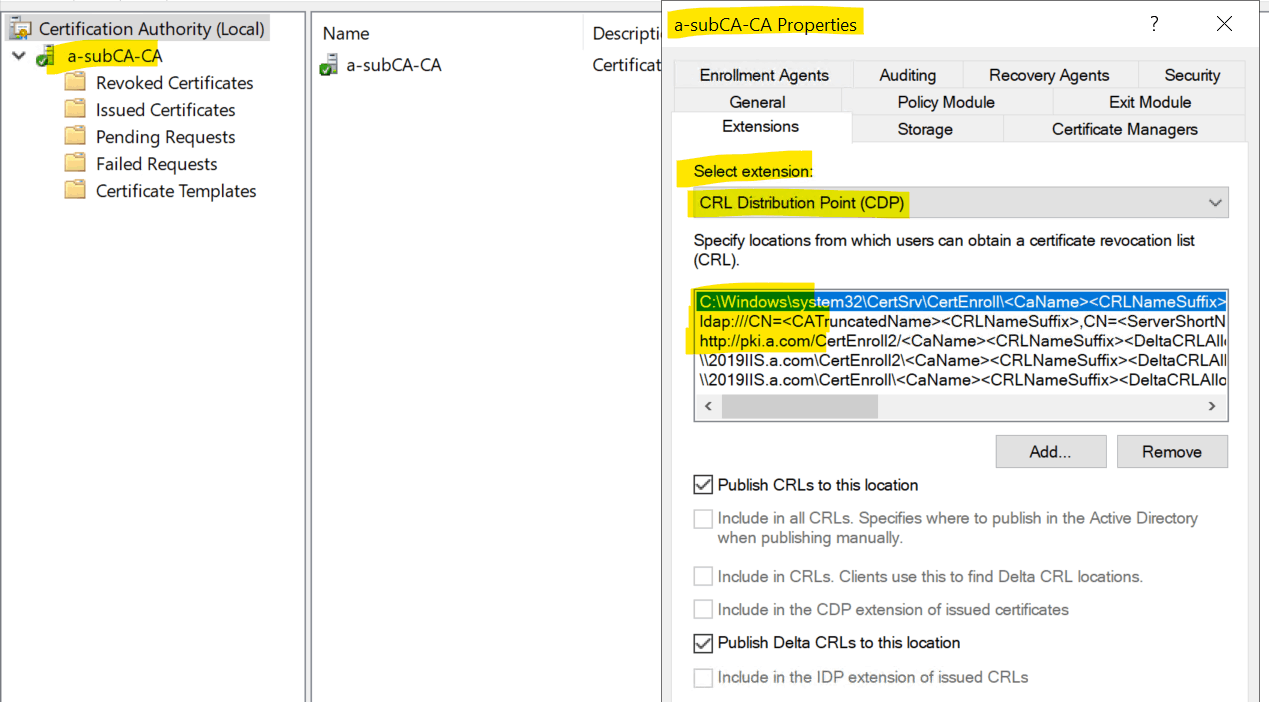
1.What locations did you configure for AIA and CDP?
For example:
local disk location (C:\Windows\system32\CertSrv\CertEnroll)
LDAP location
http location
2.Which entry displayed error "unable to download" via PKIview.msc.? You should check it.
On the root CA or issuing CA?
LDAP entry or Http entry on PKIview.msc?
2.Usually, the issue may be caused by wrong configurations on CA properties (if its CRL on root CA, you can check the CRL setting on root CA, if its CRL on issuing CA, you can check CRL setting on issuing CA).
- Or you need to check shared permissions and NTFS permissions on shared folder on IIS server that hosted http location.
4.Have you put all the .crt files and .crl files about root CA and issuing CA to http location on IIS server?
You can check them based on the link below.
AD CS Step by Step Guide: Two Tier PKI Hierarchy Deployment - TechNet Articles - United States (English) - TechNet Wiki (microsoft.com)
Best Regards,
Daisy Zhou

