
Hello Jake Cooper1,
Thank you for posting in Microsoft Community forum.
In my test, if I delegate domain user (t2) to change password for other domain users.
1.I set it through "Delegation of Control Wizard" and check "Reset user passwords and force password change at next logon".
2.I cannot check the option "User must change password at next logon" (the option is greyed out) when resetting password for domain users using t2 account.
3.However, I can reset the password for domain users in the specific OU successfully using t2 via GUI (not CMD command).
4.But when I reset password for domain users in specific OU using t2 via CMD command, it seems I get similar error message as you (below), am I right?
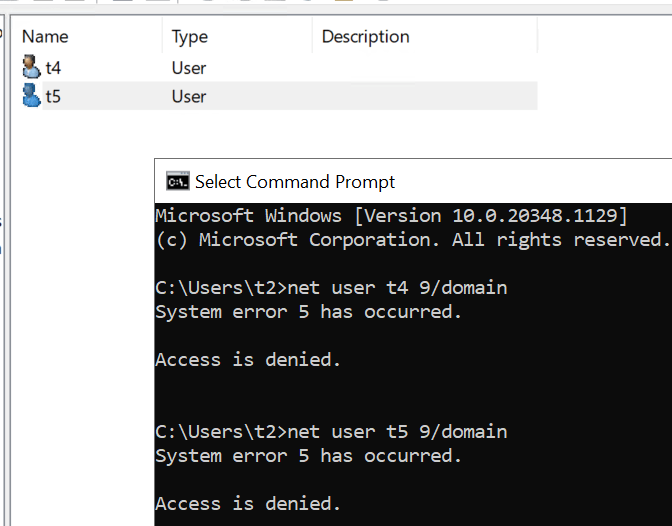
It seems resetting password via CMD needs more permissions, currently, I cannot find what specific permissions for CMD (I have done test more than two hours).
I hope the information above is helpful.
If you have any question or concern, please feel free to let us know.
Best Regards,
Daisy Zhou


