Hi,
This is happening because of the Lateral movement path calculation.
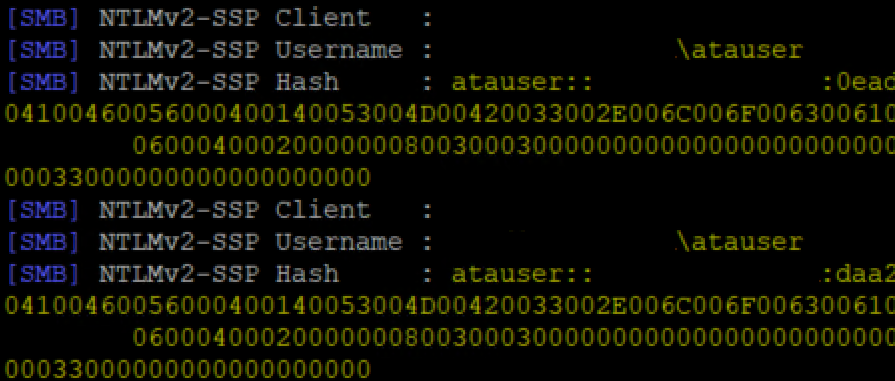
The logic in ATA uses a SAMR call to port 445 on the endpoints, while impersonated to the configured user.
While the authentication is negotiate , due to connection directly to the IP address and not the machine name, it will fallback to NTLM.
For MDI, the logic is different, and while we still use negotiate (no real other choice) we do a best effort to use the resolved DNS name for the connection.
Still, In some environments, this will still fallback to NTLM, depending on their configuration and which endpoint we are trying to connect to...
Since ATA is in extended support, porting of the MDI logic to ATA is not possible.
I would suggest to make sure (as documentation states) that the configured user is a low privileged /read only account, to minimize the risk in case of a NTLM hash leak.
Another possibility is to disable this feature completely, (requires assistance from support) , but it means you lose the lateral movement path functionality.
The best advise is to move to MDI if possible, to get the latest detections and features.
Eli.