Hello @Varun Mittal ,
Thank you for posting here.
Based on the description "While it was supporting both AES and RC4 just before demotion, for the same user", I understand the DC before demotion supports AES and RC4.
And the new created user all the new promoted DCs supports AES and RC4.
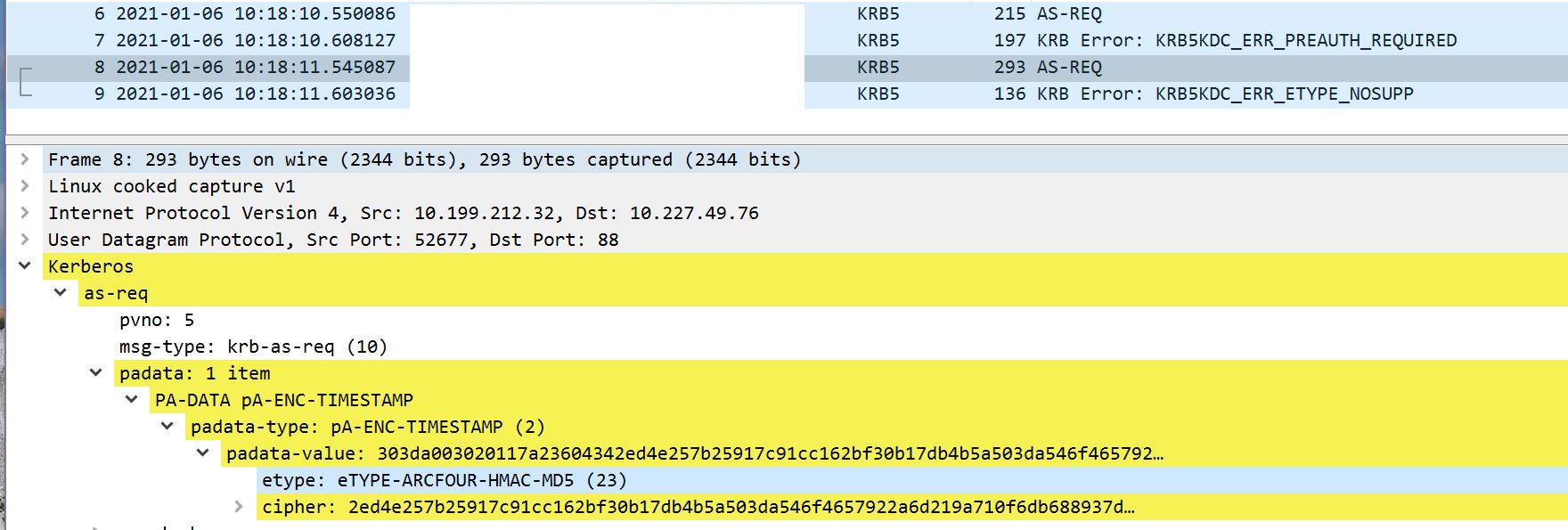
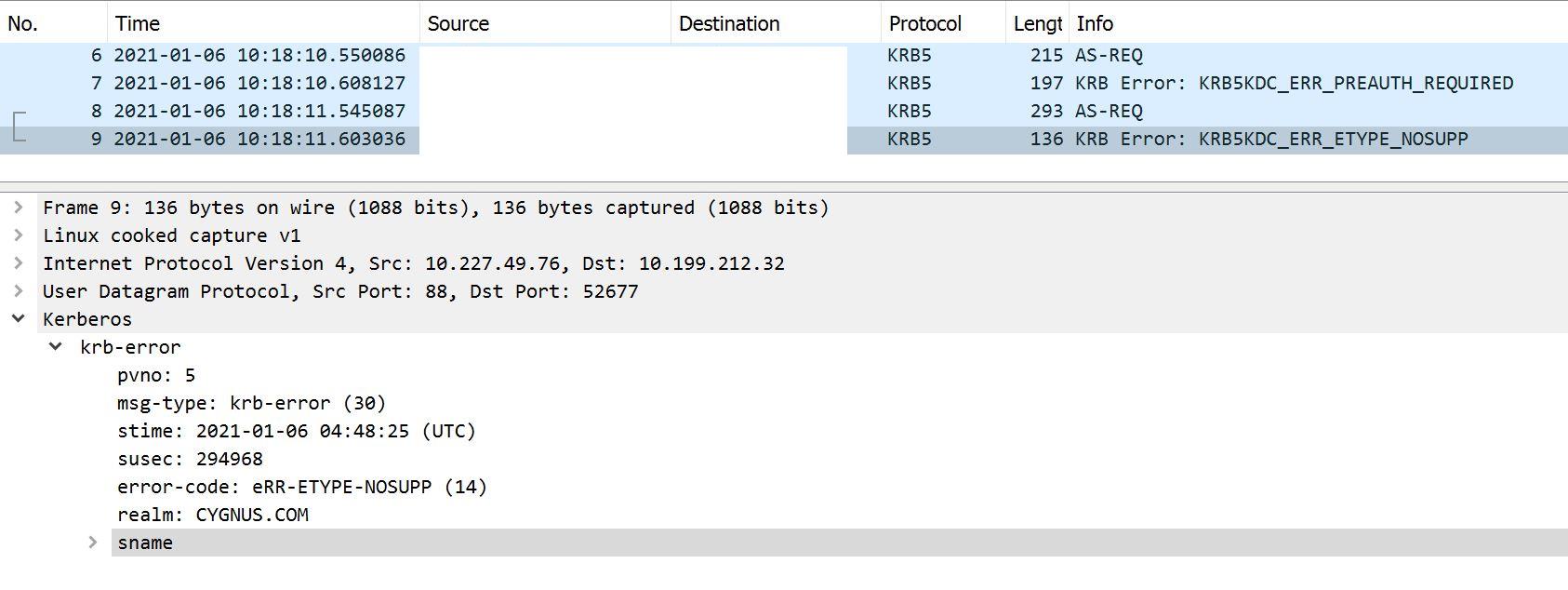
Based on the description "What I now observe is that the encryption types sent by AD for the KRB PRE-AUTH step specify only 1 enctype - RC4-HMAC", do you mean the re-promoted DC only supported RC4?
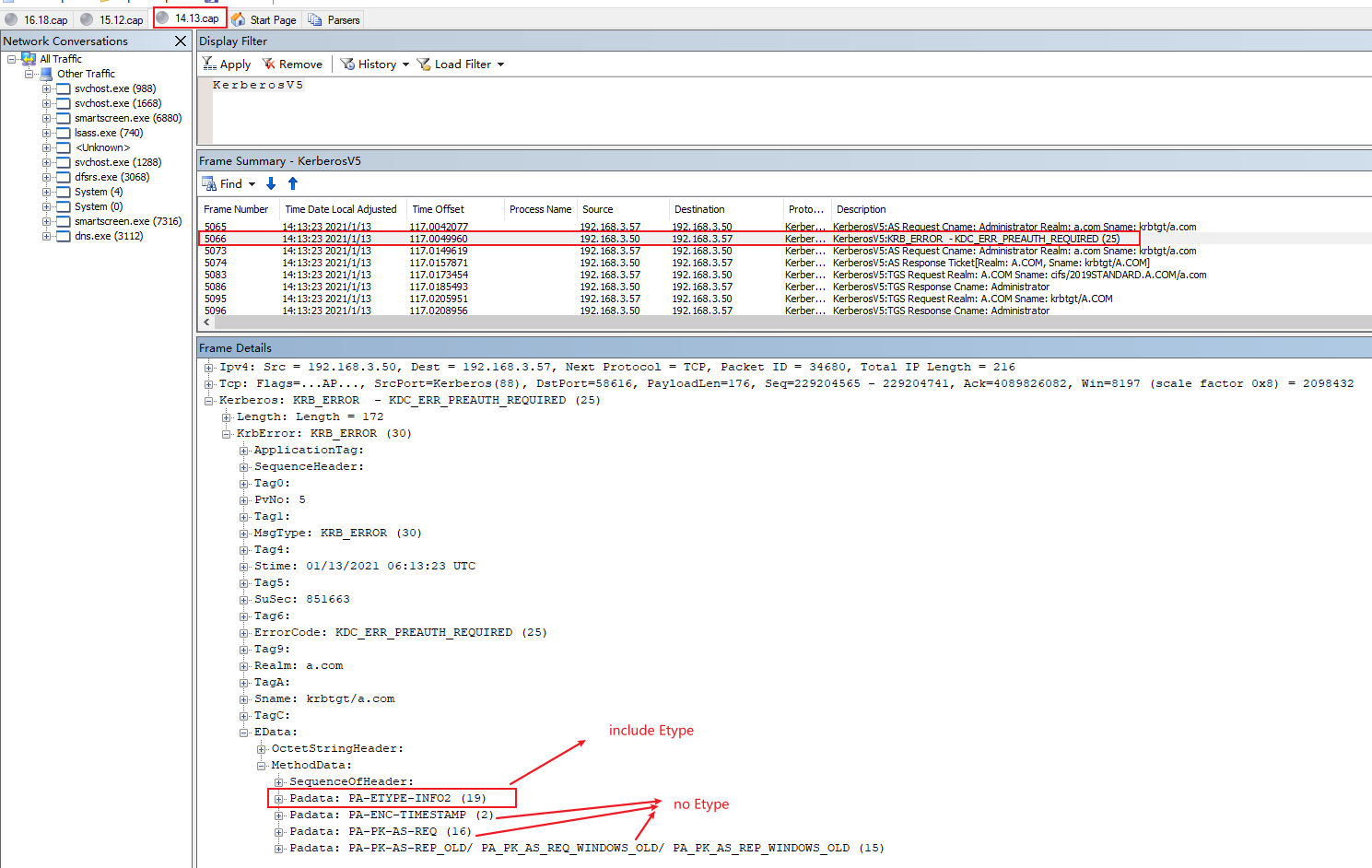
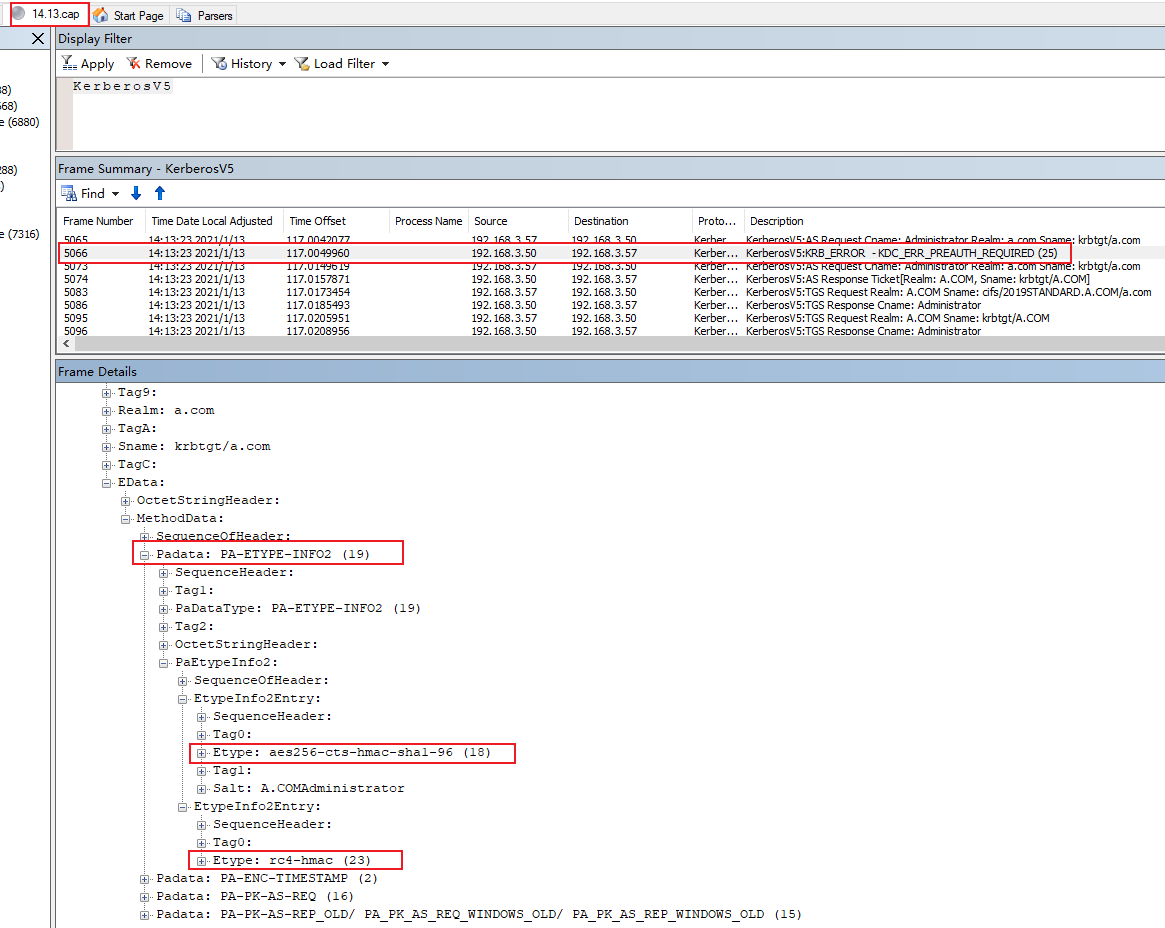
Here we can see encryption types configuration as below:
Attribute
msDS-SupportedEncryptionTypes
UserAccountControl
Group Policy
Network Security: Configure Encryption types allowed for Kerberos
Registry
SupportedEncryptionTypes
DefaultEncryptionType
KdcUseRequestedEtypesForTickets
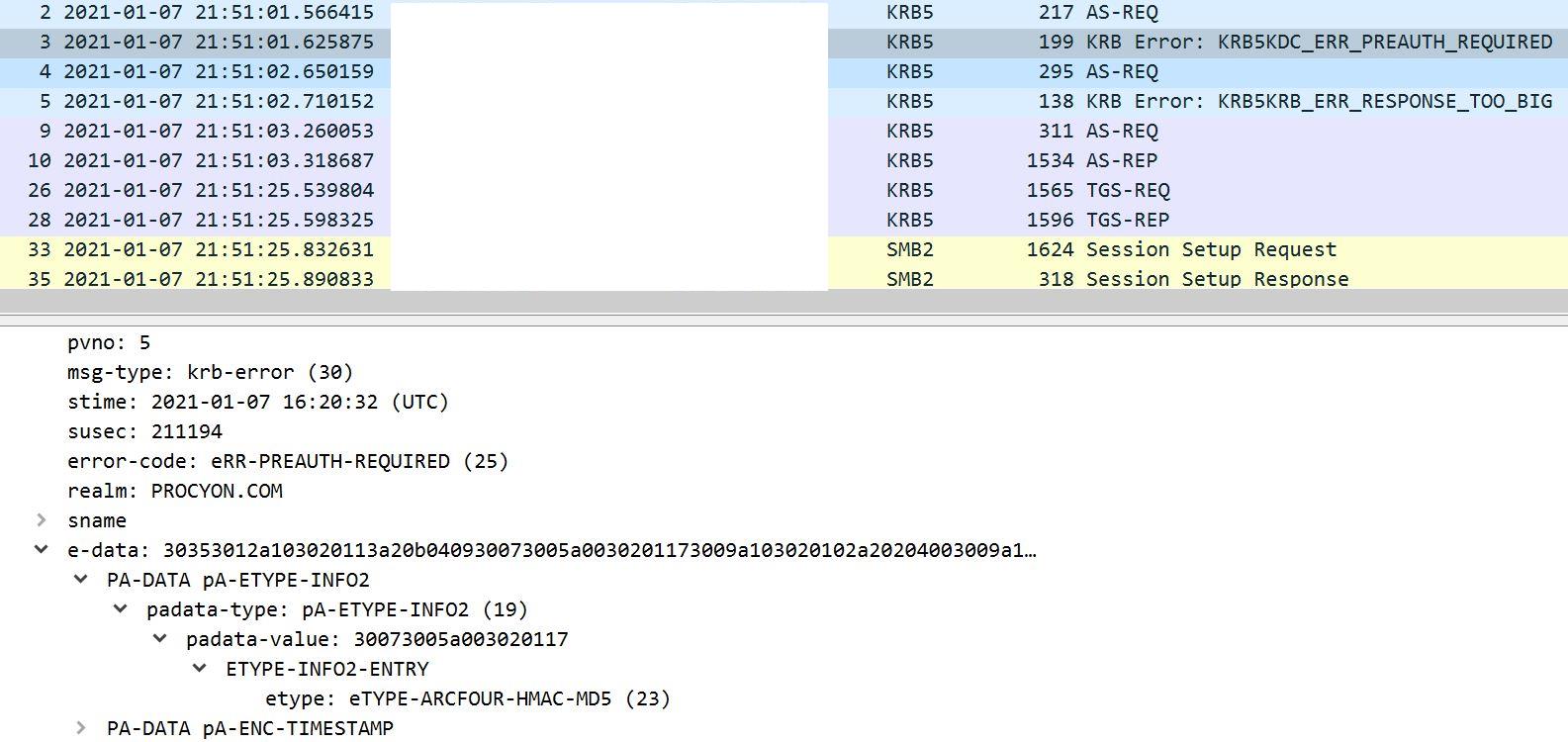
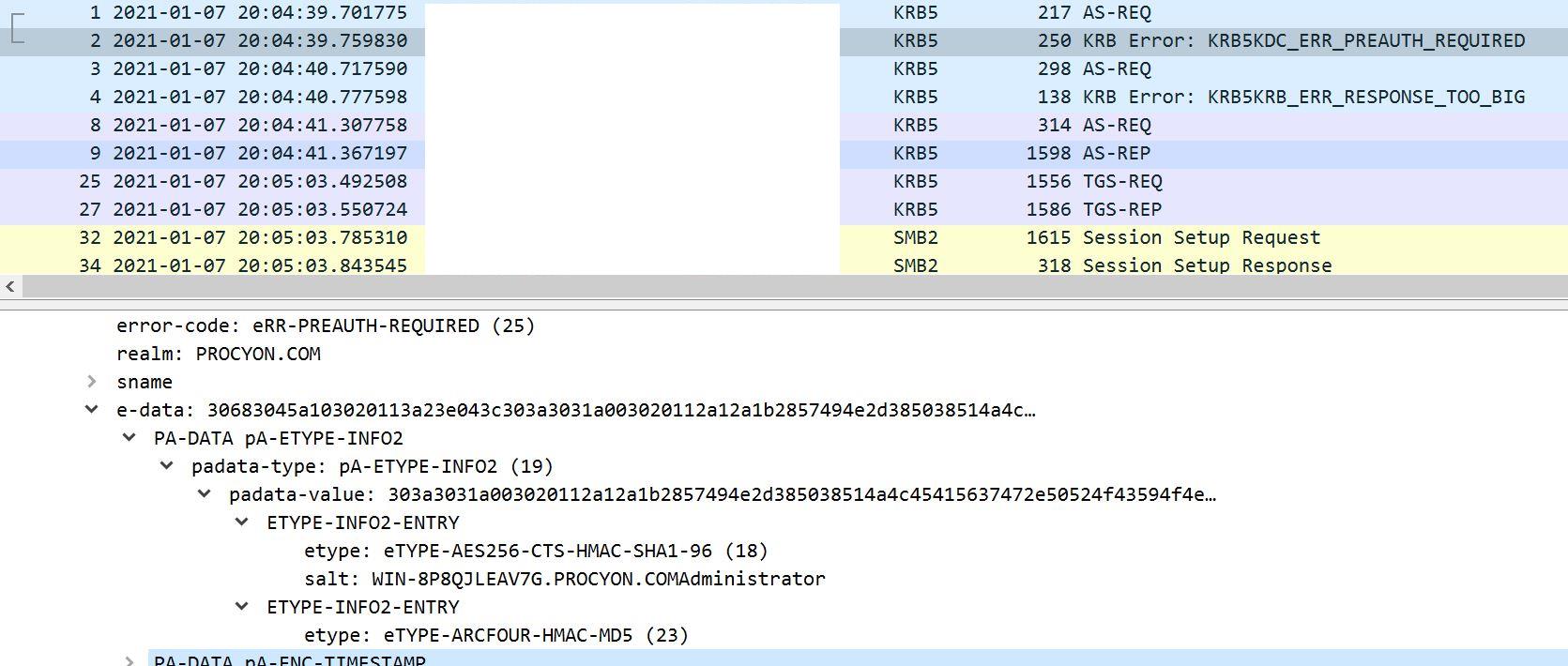
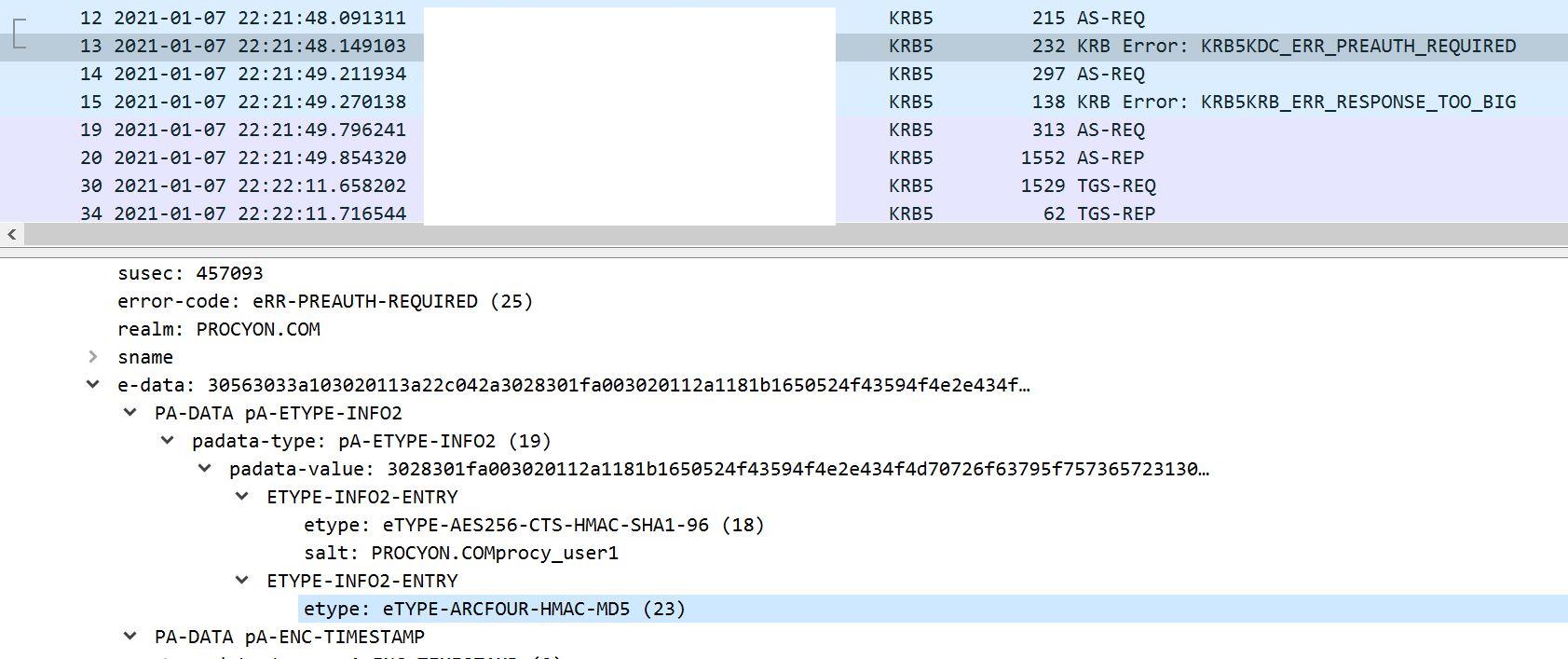
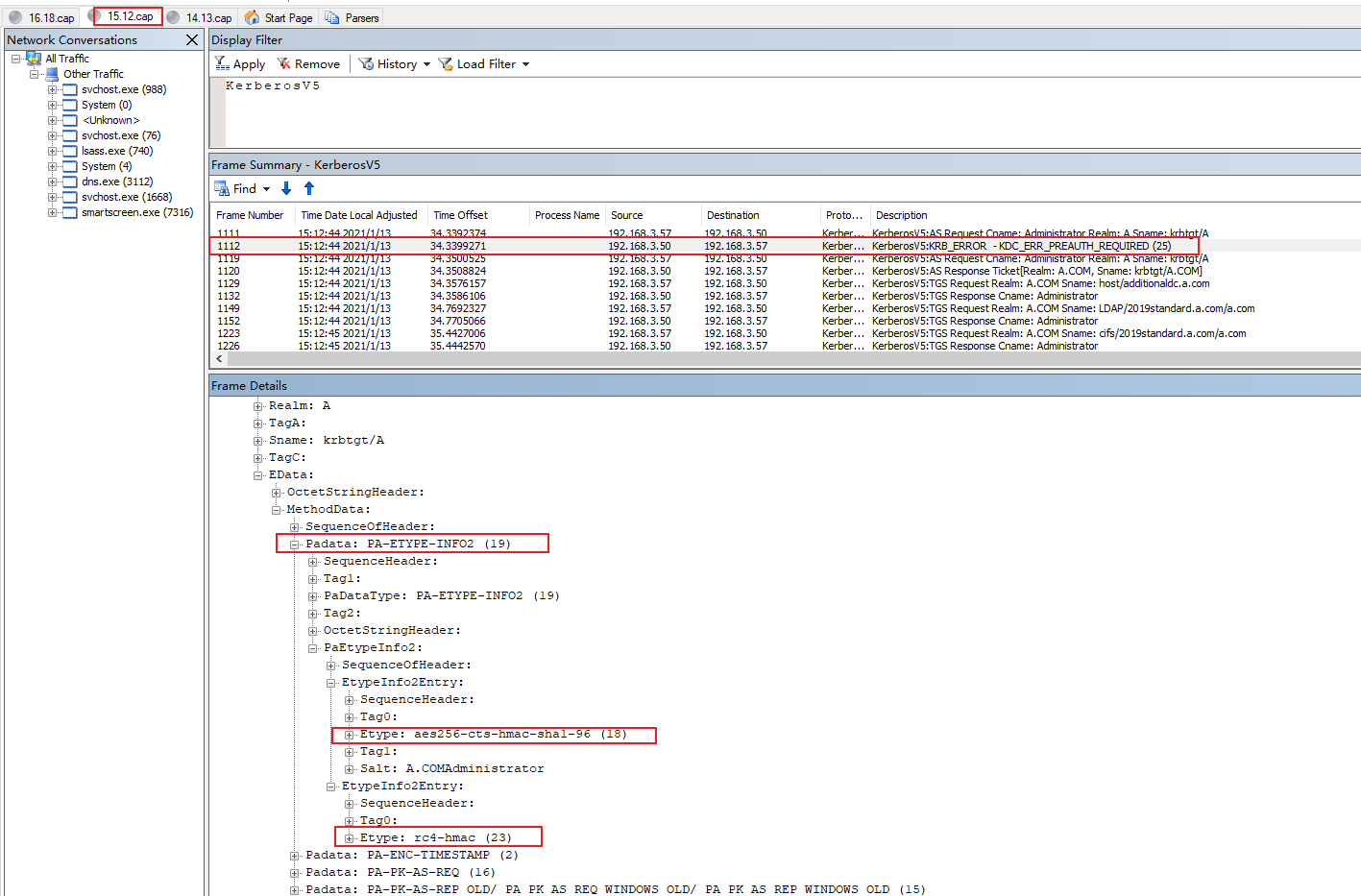
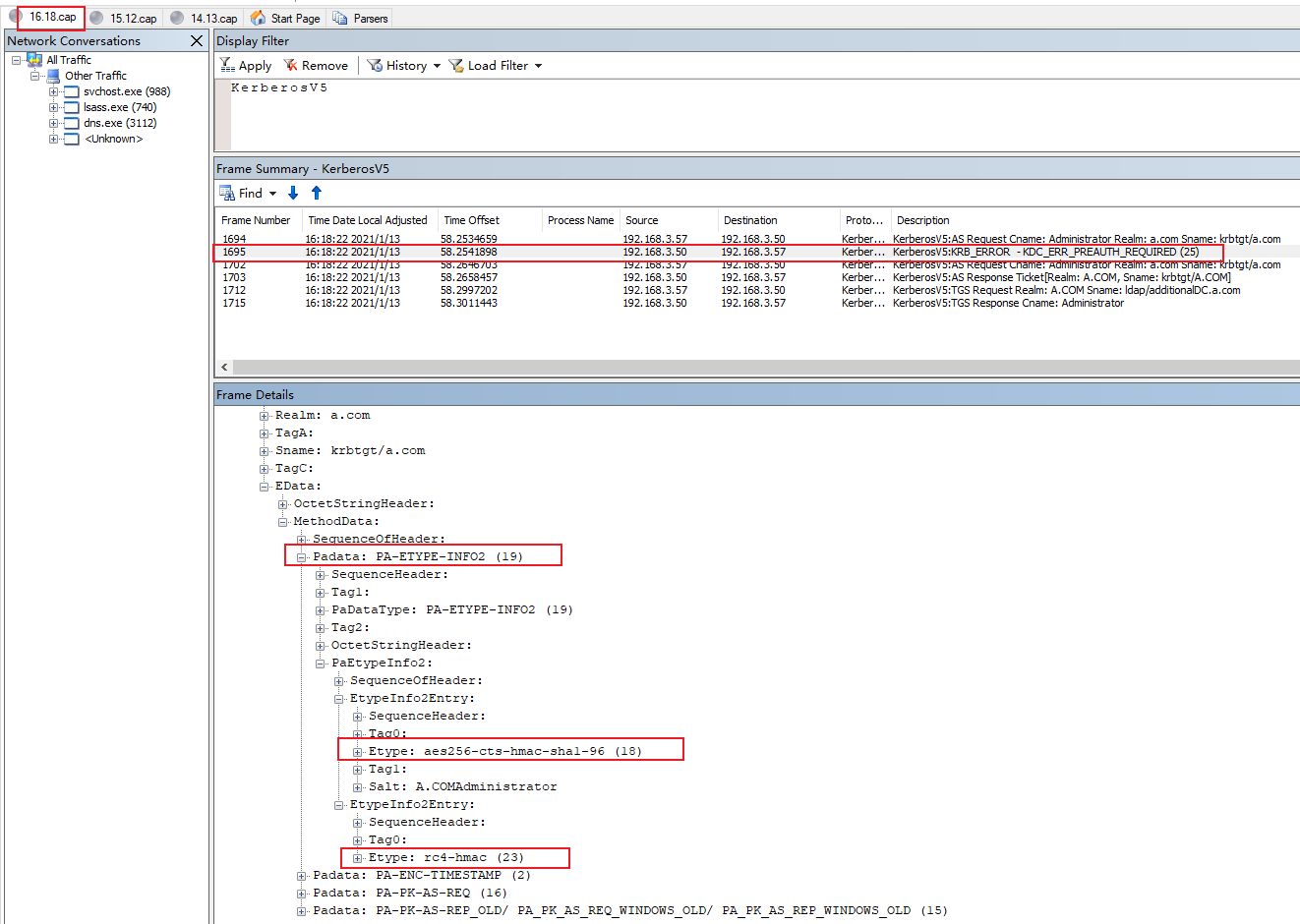
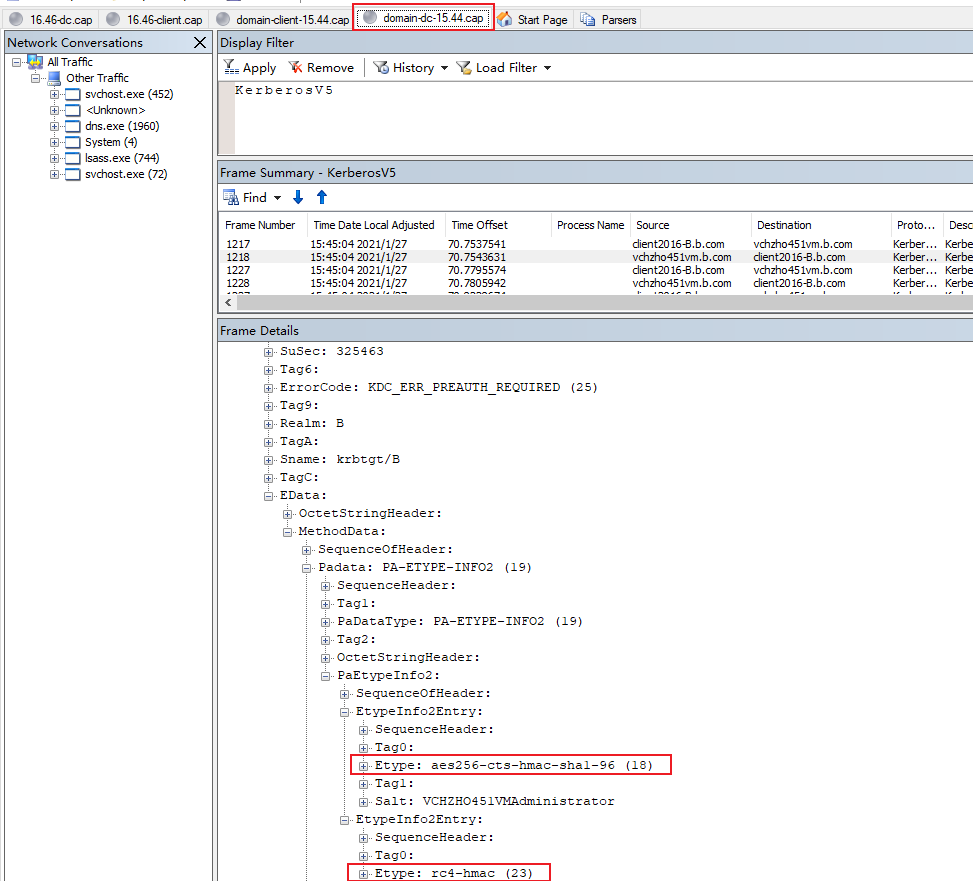
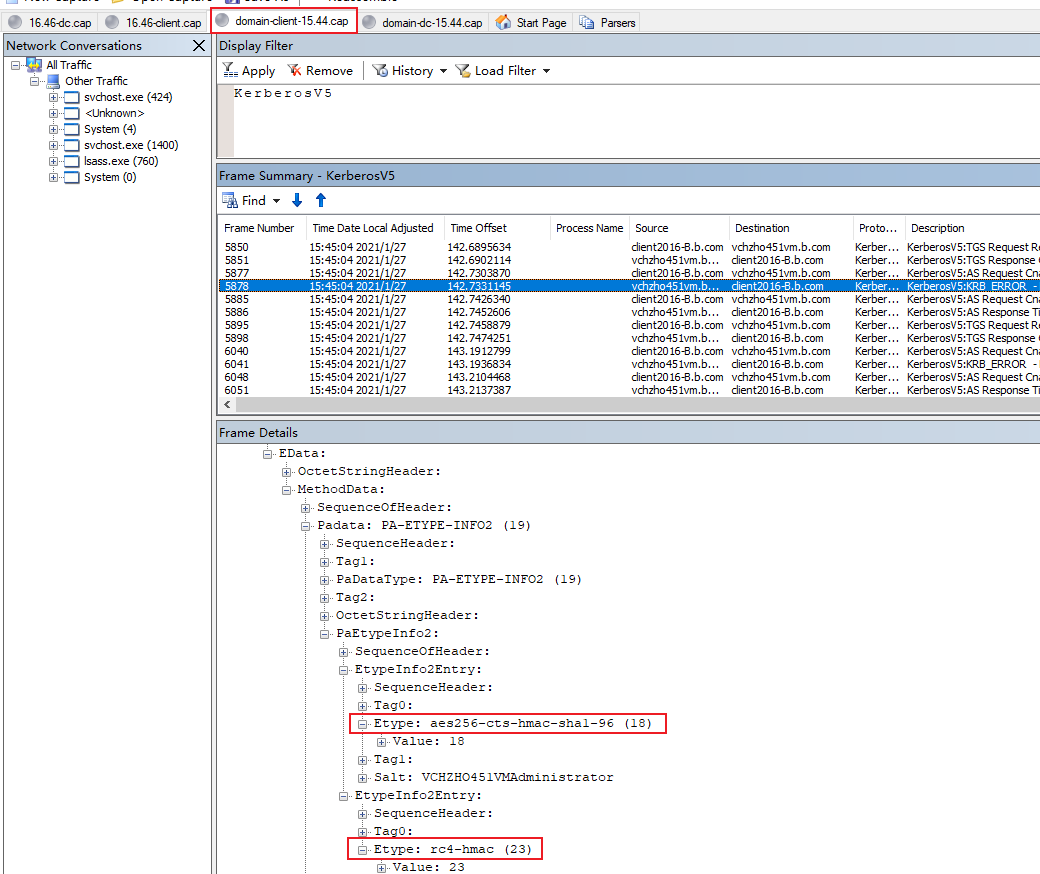
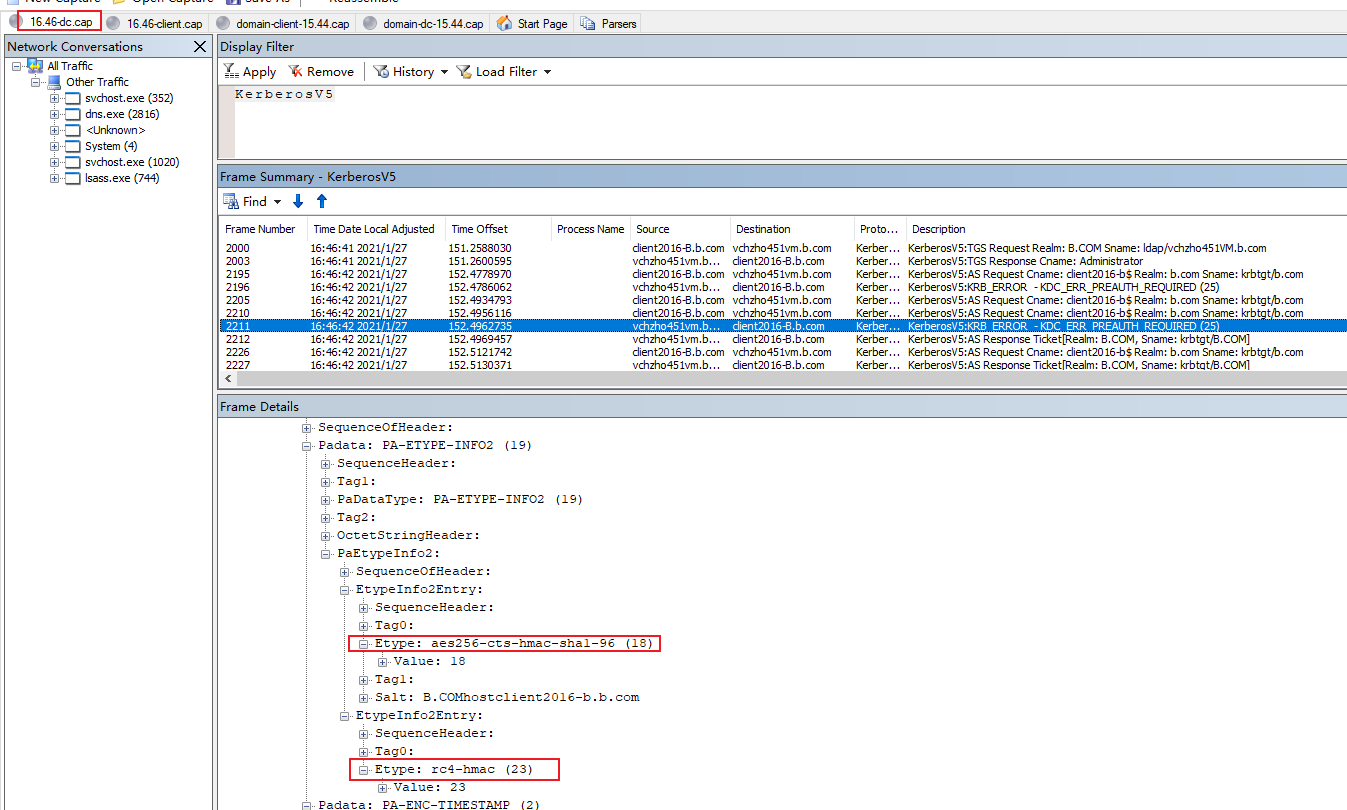
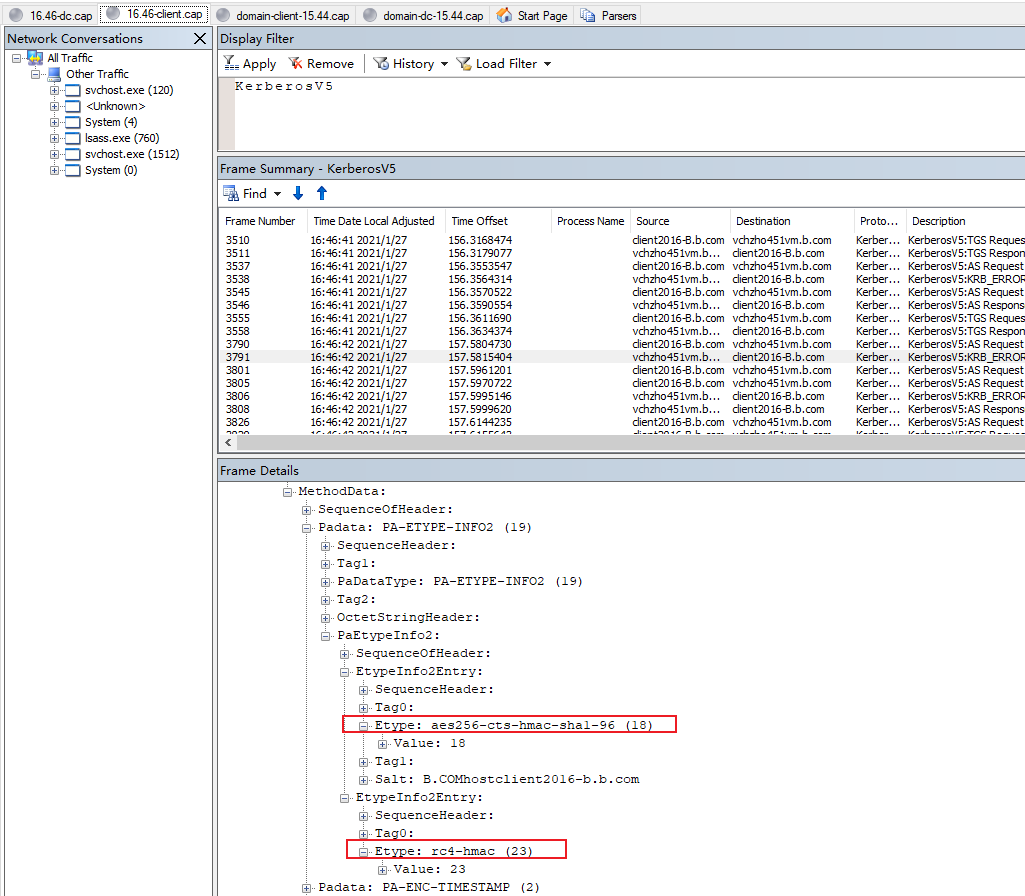
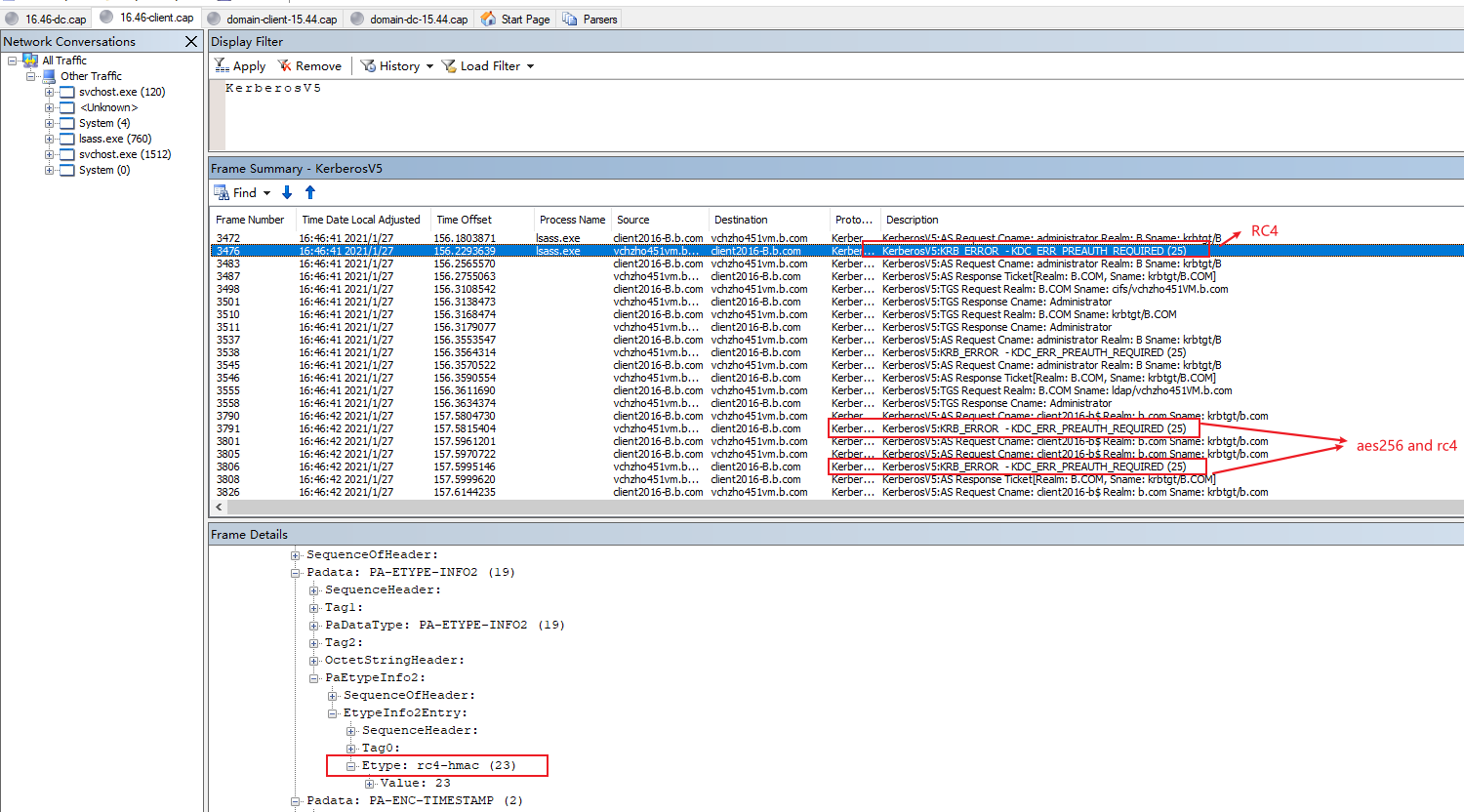
Here is the Etype of authenticator in pre-authentication below.
If registry setting DefaultEncryptionType is set to a non-zero value
Client will use this value as the Etype in pre-authentication
Else
If Etype related Group Policy is set
Client will pick the strongest Etype in the supported list set in GP
Else
If client is running on machine before Windows 7/Windows 2008
Its supported encryption list includes RC4 and DES
Else
Its supported encryption list includes AES, RC4 and DES
We can check the following registry values on this DC and user's domain PC:
SupportedEncryptionTypes (corresponding to GPO setting Network Security: Configure Encryption types allowed for Kerberos)
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters\SupportedEncryptionTypes
KdcUseRequestedEtypesForTickets
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\Kdc\KdcUseRequestedEtypesForTickets (DWORD)
If the value of this key is non-zero, the server will try and use the highest encryption level supported by the client PC.
DefaultEncryptionType
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters\DefaultEncryptionType
Entry: DefaultEncryptionType
Type: REG_DWORD
This value indicates the default encryption type for pre-authentication. Default value is RC4 is 23 (decimal) or 0x17 (hexadecimal)
When you want to use AES, set the value to the following:
aes256-cts-hmac-sha1-96: 18 or 0x12
aes128-cts-hmac-sha1-96: 17 or 0x11
Tips:
If you can not find SupportedEncryptionTypes or DefaultEncryptionType under
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters\SupportedEncryptionTypes
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Control\Lsa\Kerberos\Parameters\DefaultEncryptionType
You can find SupportedEncryptionTypes or DefaultEncryptionType under
HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\Parameters\SupportedEncryptionTypes
HKLM\Software\Microsoft\Windows\CurrentVersion\Policies\System\Kerberos\Parameters\DefaultEncryptionType
Hope information above is helpful. If anything is unclear, please feel free to let us know.
References
Kerberos protocol registry entries and KDC configuration keys in Windows
https://learn.microsoft.com/en-us/troubleshoot/windows-server/windows-security/kerberos-protocol-registry-kdc-configuration-keys
Decrypting the Selection of Supported Kerberos Encryption Types
https://techcommunity.microsoft.com/t5/core-infrastructure-and-security/decrypting-the-selection-of-supported-kerberos-encryption-types/ba-p/1628797
Use the UserAccountControl flags to manipulate user account properties
https://learn.microsoft.com/en-us/troubleshoot/windows-server/identity/useraccountcontrol-manipulate-account-properties
Best Regards,
Daisy Zhou