Hello Matthew
I understand that you need to disable public access to log analytics workspace and app insights. You are on the right track with private endpoints and Azure Monitor private link scope, so any access (including from the Azure portal on your PC) must go through a private path.
Since your PC is outside the VNet, accessing logs using Azure portal is not possible as you disabled the public access.
Here are few options to allow access:
1.Use a VPN (Site-to-Site or Point-to-Site)
Connecting your local machine to the Azure VNet via VPN will make it part of the virtual network:
• Set up a Point-to-Site VPN on the Azure Virtual Network Gateway.
• Connect from your PC using the VPN client.
• Once connected, you’ll be able to access logs through the Azure Portal
2.Access via Bastion
Deploy a VM within the VNet (or a peered one) that can access the private endpoint.
You can then:
• Use Azure Bastion to securely RDP or SSH into the VM.
• Open the Azure Portal from a browser on that VM, and access Log Analytics or Application Insights.
Since the traffic originates from within the VNet, private endpoint access will work as expected.
3.Temporarily Enable Public Access (IP-Restricted)
If VPN or Bastion isn’t feasible and you need temporary access:
• Go to the Log Analytics Workspace > Networking section.
• Set Public Network Access to “Enabled from selected networks.”
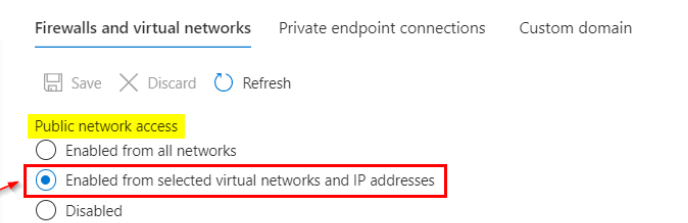
• Add your PC’s public IP address to the firewall rule list. This allows you to access the workspace from your current machine, while still restricting exposure to known IPs.
Please don’t forget to close the thread by clicking "Accept the answer" and "Yes" wherever the information provided helps you, as this can be beneficial to other community members.
