Hello @Sem, Gunnar Windsand ,
Welcome to the Microsoft Q&A platform.
While creating and running a scan, initially I had faced the same problem.
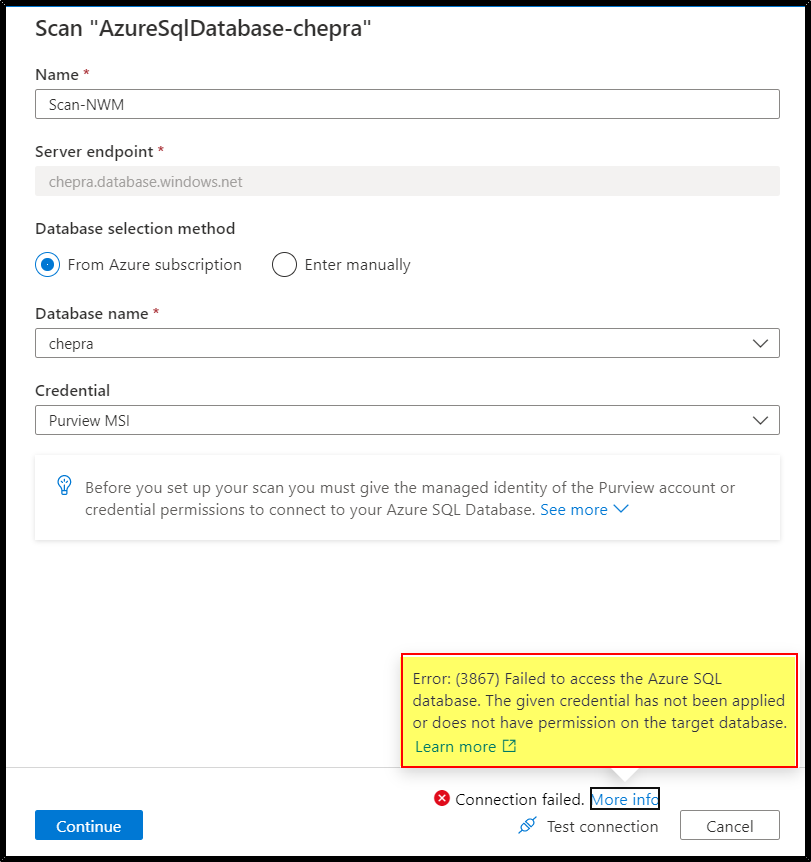
After going through the document, I had found this information which helped to resolve the issue.
If you are using managed identity, your Purview account has its own managed identity which is basically your Purview name when you created it. You must create an Azure AD user in Azure SQL Database with the exact Purview's managed identity or your own service principal by the following tutorial on Create the service principal user in Azure SQL Database. You need to assign proper permission (e.g. db_owner or db_datareader) to the identity.
Example SQL syntax to create user and grant permission:
CREATE USER [Username] FROM EXTERNAL PROVIDER
GO
EXEC sp_addrolemember 'db_owner', [Username]
GO
Note: The Username is your own service principal or Purview's managed identity. You can read more about fixed-database roles and their capabilities.
Steps to resolve the issue:
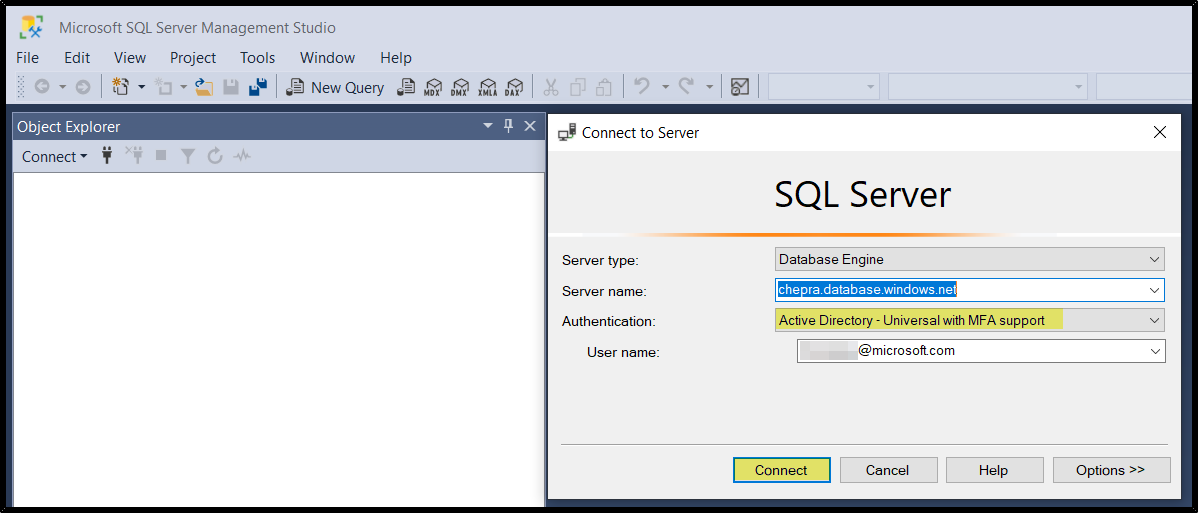
Step1: Connect to Azure SQL Database using SSMS using Active Directory option.
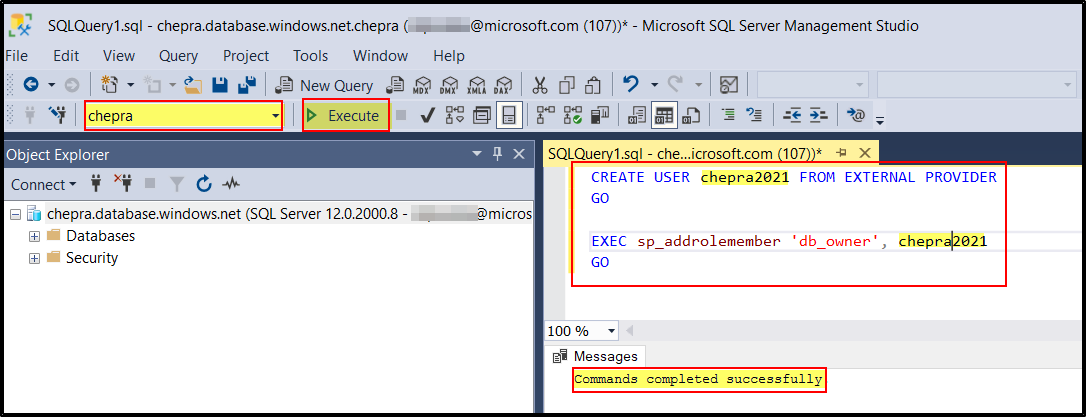
Step2: Select the database and run the below command.
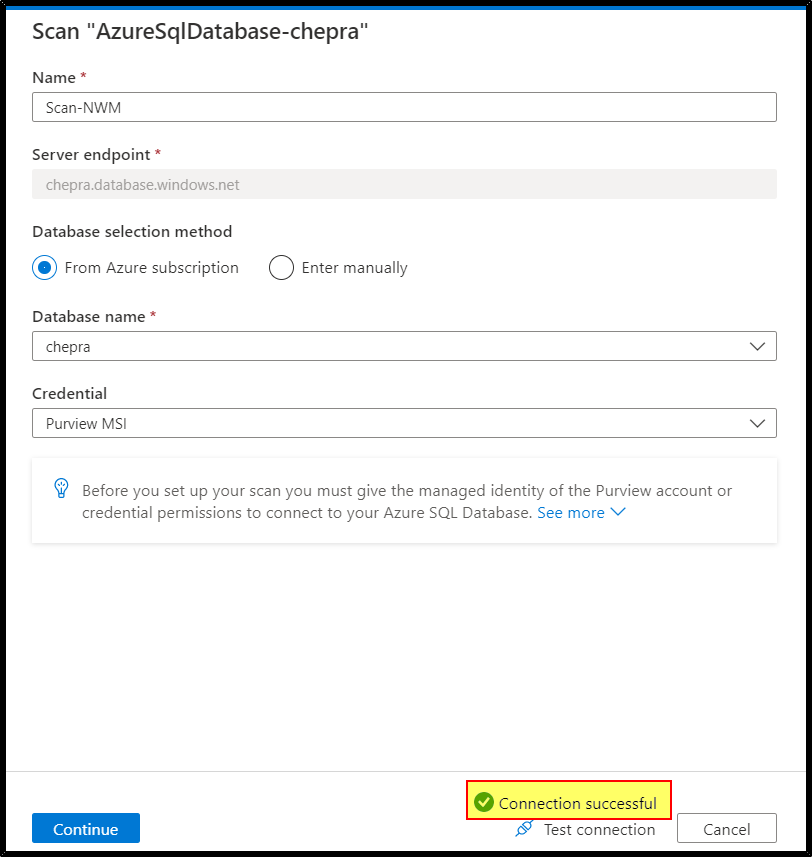
Step3: Go back to Azure Purview portal and test connection
Hope this helps. Do let us know if you any further queries.
------------
- Please accept an answer if correct. Original posters help the community find answers faster by identifying the correct answer. Here is how.
- Want a reminder to come back and check responses? Here is how to subscribe to a notification.
