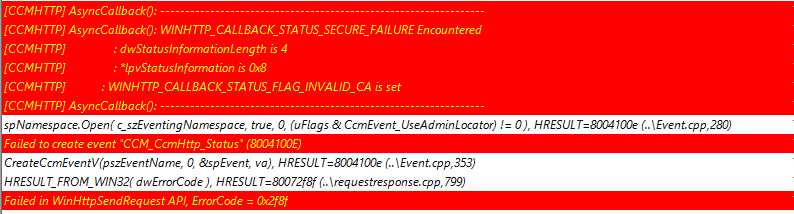
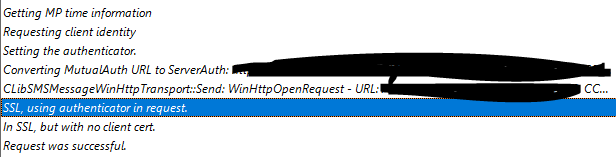
If token-based wasn't working at all, then there'd be no communication between the CMG, the internal MP and clients - but comms for those are working fine with token-based auth.
Correct and I concur.
but would the CA also need to be visible in order for it to be reachable in terms of trust?
No specifically, no, however, the CRL for the CA needs to be accessible and that can be hosted in a variety of ways, one of which must be accessible. I don't believe there is a way to disable CRL checking during WinPE.
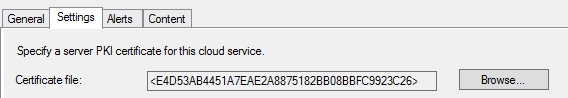
You may be able to add the cert from the internal root CA to your site's configuration (on the Communication Security tab of the site's properties). This is meant to add the CA as trusted on managed devices as well as within boot images although this was specifically designed for sites using HTTPS client communication, so I don't 100% know if it will work for this newer scenario. I think that it should, but I haven't tested explicitly. You will have to regen the boot image after adding the cert. And further, disabling CRL checking on this same page may also disable CRL checking in the boot image as well -- it does normally for the HTTPS client communication scenario but not sure for this scenario.
Here's a random screenshot from the web for reference in case you are not familiar with this property page: https://www.bing.com/images/search?view=detailV2&ccid=jwWIntbt&id=2D27B2A53759DBE7725E3FB4300EA443E9661D94&thid=OIP.jwWIntbt19DgotM5Cnr62AHaHH&mediaurl=https%3a%2f%2fsocial.technet.microsoft.com%2fForums%2fgetfile%2f1605721&exph=568&expw=591&q=%22Communication+Security%22+sccm&simid=608043979562289357&ck=704C8B3066F7C6706CBF4F2E8E41CFF6&selectedIndex=1&FORM=IRPRST&ajaxhist=0