Hello,
Thank you so much for posting here.
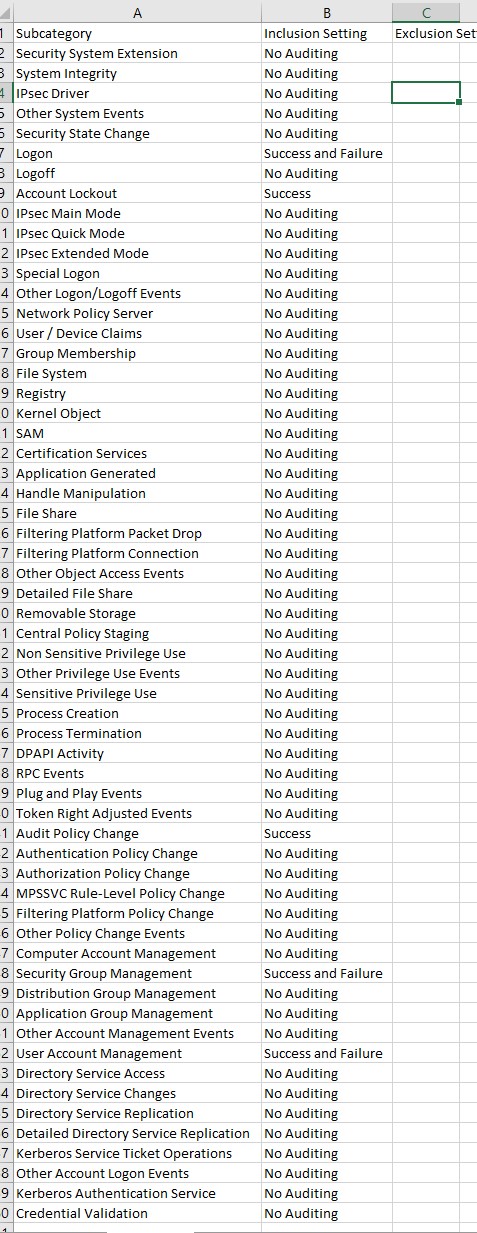
To track users logon/logoff, we need to enable Auditing by using Group Policy. There are two types of auditing that address logging on, they are Audit Logon Events and Audit Account Logon Events.
Audit "logon events" records logons on the PC(s) targeted by the policy and the results appear in the Security Log on that PC(s).
Audit "Account Logon" Events tracks logons to the domain, and the results appear in the Security Log on domain controllers only.
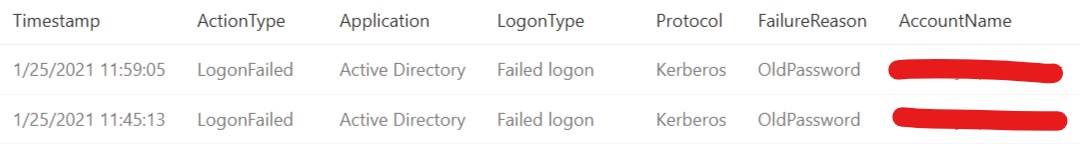
As for the event 4625: An account failed to log on, It generates on the computer where logon attempt was made, for example, if logon attempt was made on user’s workstation, then event will be logged on this workstation. That's to say, it will not be recorded in the event logs on domain controller.
https://learn.microsoft.com/en-us/windows/security/threat-protection/auditing/event-4625
Best regards,
Hannah Xiong
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.