@Liam Fermoyle Thanks for reaching out.
The concern regarding normal user being the admin after connected to Intune can be solved in 2 ways with endpoint manager.
Windows Autopilot - Windows Autopilot provides you with an option to prevent primary user performing the join from becoming a local administrator. You can accomplish this by creating an Autopilot profile.
Bulk enrollment - An Azure AD join that is performed in the context of a bulk enrollment happens in the context of an auto-created user. Users signing in after a device has been joined are not added to the administrators group.
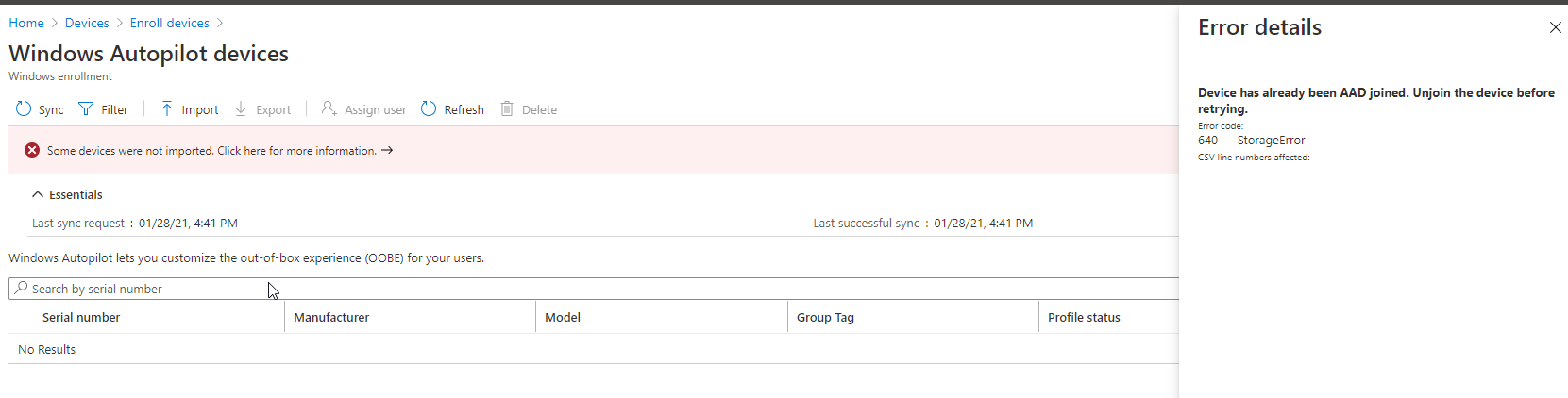
Coming to your next issue with forcing the join, as long as the AAD detects that the device is already AAD joined, it will continue to throw that error, you can delete the device from Devices list in AAD and try again. IF not, then you must remove the device from AAD and re-join.
This device seems to have follow the autopilot path before as well and somehow not properly completed the process.
A support case with Intune team will help you investigate further.
-----------------------------------------------------------------------------------------------------------------
If the suggested response helped you resolve your issue, please do not forget to accept the response as Answer and "Up-Vote" for the answer that helped you for benefit of the community.
 We are working towards our Cyber Essentials Plus.
We are working towards our Cyber Essentials Plus.