Hello @ASaurdiff ,
Microsoft Graph API permission only works with Microsoft Graph API level calls (https://graph.microsoft.com/) and reason it was falling through PowerShell because AAD PowerShell V2 modules still uses Azure AD Graph API ( https://graph.windows.net) calls instead Microsoft Graph API to retrieve AAD resource information and this is an know behavior of AAD V2 PowerShell Module.
As we all know that "Azure AD Graph API" is on a deprecation path, so our product group is working on AAD module migration from Azure AD Graph API to Microsoft Graph API before it fully deprecate.
Therefore, you can either use Azure AD role or Azure AD Graph API permission for service principal to delegate the permission.
Alternatively, you could Check out Microsoft Graph PowerShell for Azure AD automation so you can granulate the permissions more by leveraging Microsoft Graph API permission (like: User.ReadWrite.All , User.Read.All etc..,) . To know more about refer this article
Here are some example cmdlet when you use Microsoft Graph PowerShell :
To install the latest version, run the Install-Module as Administrator as here.
Install-Module Microsoft.Graph -Repository PSGallery -force
To see a list of all commandlets (which is looong), use Get-Command -Module "Microsoft.Graph.*
Cmdlet to Connect Graph by using service principal :
Connect-Graph -AppId "447672e9-da89-123f-a2b5-99232a7bb08a" -CertificateThumbprint "2DBD6360F4D1EFB478BA1EF311F25CDA4ABA70BF"
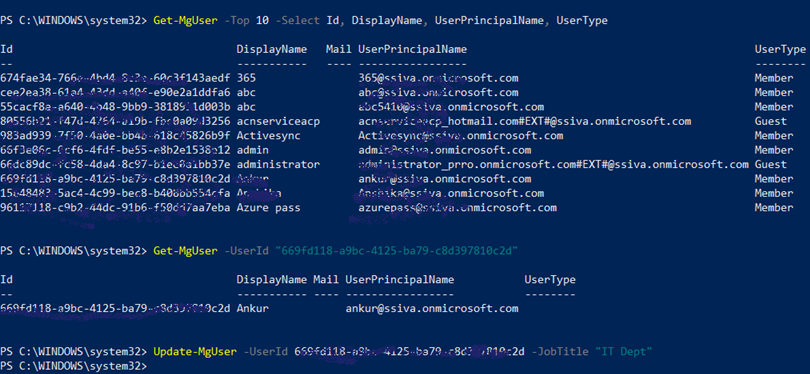
To Get top 10 user: Get-MgUser -Top 10 -Select Id, DisplayName, UserPrincipalName, UserType
To get user with ID : Get-MgUser -UserId "669fd118-a9bc-4125-ba79-c8d397810c2d"
To update users attribute: Update-MgUser -UserId 669fd118-a9bc-4125-ba79-c8d397810c2d -JobTitle "IT Dept"
Screenshot
-----------------------------------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.