You can find how to do it in the Log Forwarder deep dive in module 4 of the Azure Sentinel Ninja Training
Azure Sentinel - Syslog log filtering on VM
Hello,
I created VM (linux) for syslog role. I configured Sophos UTM to send firewall' 'daemon' 'information'' logs to the syslog server. Log further are sent to Azure Sentinel. From AS side I enabled daemon(info) logs receiving. So far all good.
Problem - so i'm receiving logs from Sophos UTM and there are lots of firewall logs (and they are consisting of info i want) but for example i have FW rule ID- 144 and it's total over 6 million entries which were sent to Azure Sentinel from syslog server.
Can i do some kind of firewall filtering? So i could determine which kind of fw rule id i need to sent to azure sentinel at syslog server level?
Or i need to do firewall log collecting and sending at Sophos UTM device level?
Also is there some kind of automation for clearing log files on syslog server because after 1 week of receiving logs it's disk drive is full and i need manually clear *.log file
Microsoft Security | Microsoft Sentinel
2 answers
Sort by: Most helpful
-
-
Eduards 791 Reputation points
2021-02-09T12:54:24.337+00:00 Ok for example i created and 50-filter.conf file inside of rsyslog.d
Which looks like this.
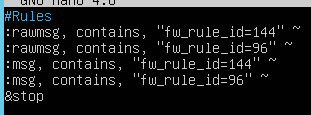
So basically log which include fw rule id 144,96 will not be delivered to Azure Sentinel?