Hello @Ju , Thank you for reaching out. This error usually comes up when the request that is being sent by the application contains a redirect uri that doesn't match up with the one configured in the app registration.
The best way to troubleshoot this issue all by yourself would be to follow the steps mentioned below and figure out the redirect uri that the app is sending to AAD in the request and what is configured in your app registration.
- Install fiddler and make sure you enable HTTPS decryption option enabled on Fiddler before taking a trace.
- Fiddler download link: https://www.telerik.com/download/fiddler
- Enable HTTPS decryption: https://docs.telerik.com/fiddler/Configure-Fiddler/Tasks/DecryptHTTPS - Once the fiddler is installed and configured, start the fiddler trace and try to perform the login test. if this is a web-app, try accessing the web-app in the in-private browsing mode.
- Once you have performed the login test and it fails with that error, stop the fiddler trace and check for the request in Fiddler (Hint: look for the request to authorize endpoint. Refer to the screenshot below)
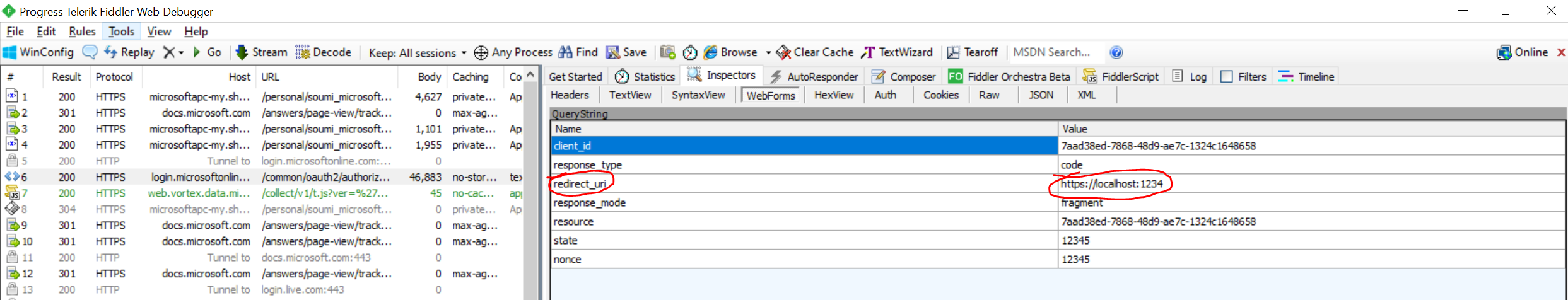
- So from Fiddler you would know the request URI that is being sent by your app to AAD.
- Next, open up Powershell as an administrator and run the following cmd:
Get-AzureADApplication -SearchString "{App-Name}" | Select-Object DisplayName, AppId, ReplyUrls | fl - This cmdlet would give you a list of replyURLs/RedirectURIs configured in your app registration.
- Last thing, you just need to compare the redirect URI you found from Fiddler and the Reply URLs you found from the Powershell cmdlet and check if there is a mismatch. If there is a mismatch, fix the request and make your app to send one of the reply URLs found in the app registration, or the reply URL sent in the request is correct from App side, update the same in the app registration.
By this, we will make sure the reply URL is sent in the request and the reply url configured in the Ap-Registration in AAD are the same and this error won't come up.
Hope this helps.
Do let us know if this helps and if there are any more queries around this, please do let us know so that we can help you further. Also, please do not forget to accept the response as an Answer; if the above response helped in answering your query.