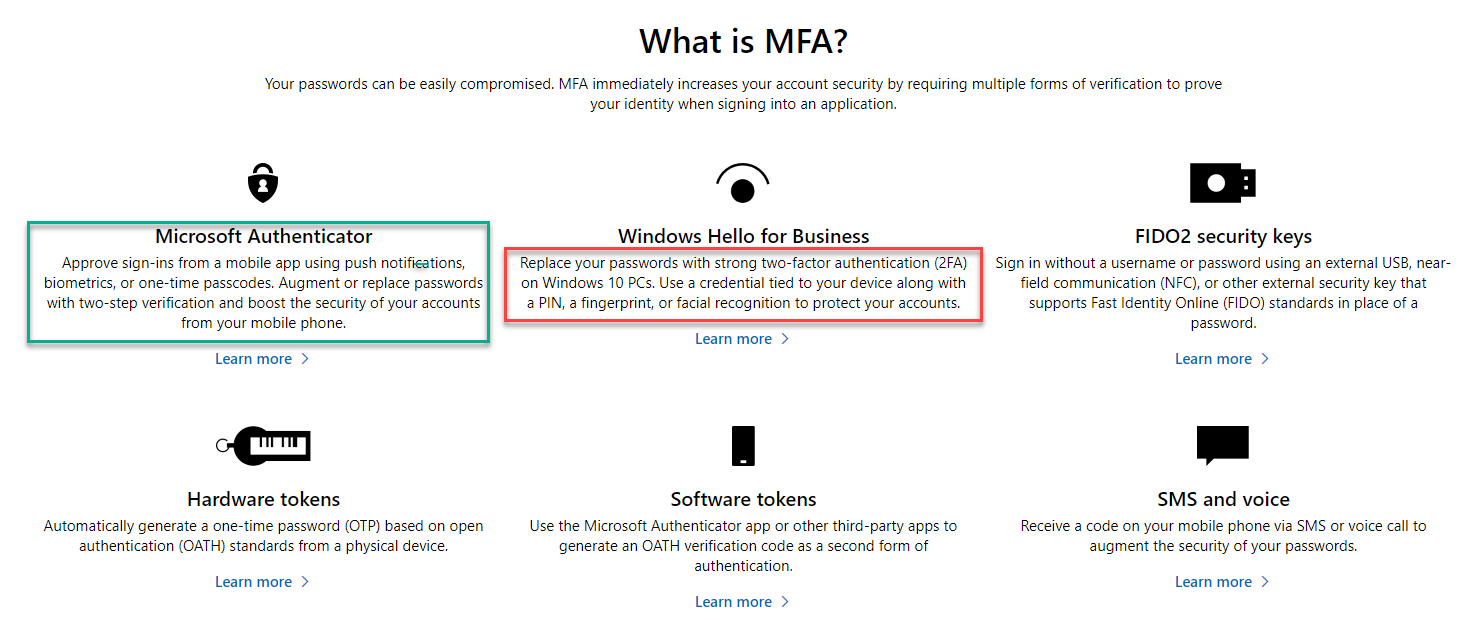
@Robbert MS does not allow any Azure MFA at the time of Windows login. A normal MFA which is supported by MS is Windows Hello or Pin.
However, if you must find a way with authenticator App during Windows Login, you can try some 3rd parties that integrate this functionality with their 3rd party tools.
Using 3rd parties for this is solely up to you and MS does not support/recommend them.
As a informational piece, you can look at : https://james-rankin.com/articles/adding-microsoft-authenticator-mfa-to-windows-logon-using-manageengine-ad-self-service-plus/ to understand how other people might be using it.
[The link is a 3rd party link and is used for knowledge purpose only, MS is not responsible for any information shared in that.]