Hello @Tony Price , sorry there's been no response to your questions. Here are some answers based on my understanding of your scenario.
Currently our policy only monitors and reports non-compliance with Tags. Will creating a deny policy of resource creation impact existing resources, that is stop them from functioning?
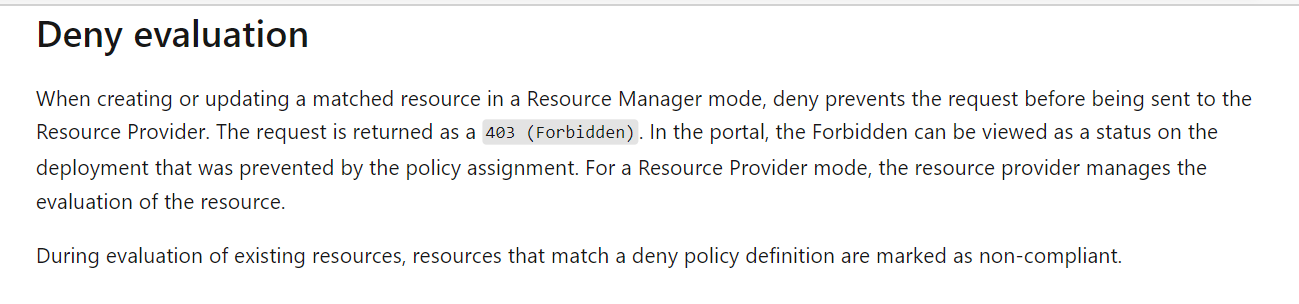
No, the Deny Policy will not stop exsiting/running resources from functioning. During evaluation, the existing resource is marked as non-compliant if conditions on the resource matches the policy definition. You have the option to create a remediation task to fix the non-compliant resource(s). Source: how deny effect works on new and existing resources.
I need to enforce tags on all Azure resources not just resource groups. We need to be able to track expenses on any resource that incurs a cost. This json below will only work on resource groups. How should I edit this to include other Azure resources?
To enforce tags on resources, you will need to reference the resource attribute in your policy definition. Here's a sample definition that uses the Modify effect to evaluate resources and adds specified tag/values if missing from a newly created or existing resource - snippet below. Check out this content on how to use tags to group billing/cost data.
{
"properties": {
"displayName": "Add a tag to resources",
"policyType": "BuiltIn",
"mode": "Indexed",
"description": "Adds the specified tag and value when any resource missing this tag is created or updated. Existing resources can be remediated by triggering a remediation task. If the tag exists with a different value it will not be changed. Does not modify tags on resource groups.",
"metadata": {
"version": "1.0.0",
"category": "Tags"
},
Our student email is in the same domain/tenant as our Azure tenant. Is it possible to automate filtering those free/trial subscriptions from this policy?
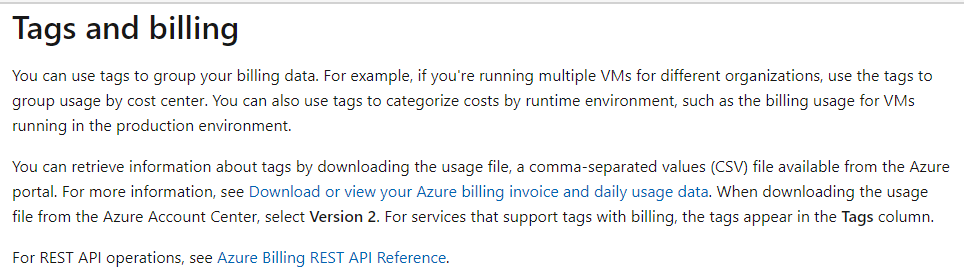
Not sure I completely understand this question but AFAIK you should be able to define a scope for your policy to include or exclude subscriptions based on your preference. Here's some useful content on defining Scope in Azure policy.