@Stephen Thank you for reaching out.
You are right. For complete isolation from public internet, Deny Public Access should be set to Yes.
This also means that customers will now have to go through creating and managing services like Azure Private Endpoint or Azure Private Link
Some customers have their workloads on multiple cloud providers and need to connect to Azure SQL Database over public internet.
When customers have a database that is exposed, new tooltips encourage customers to create a private end point and deny public internet access.
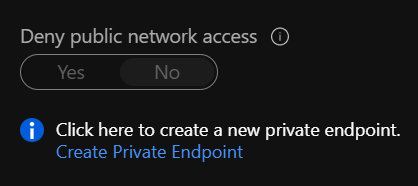
Azure Security Center identifies and makes recommendations accordingly.
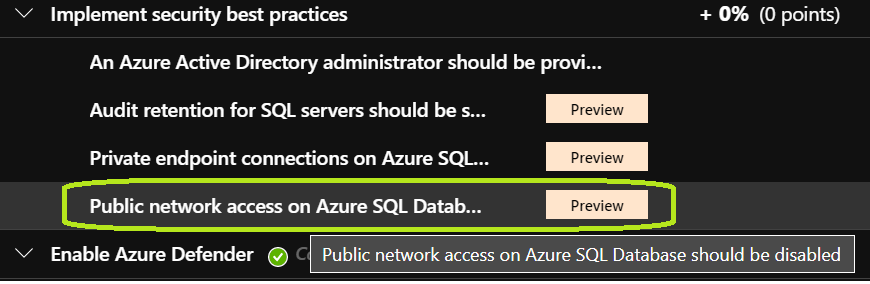
As of today, to cater to all generic use cases, Deny Public Access is not currently enforced by default while sensitizing customers on the subject and encouraging them to take action.
Your suggestion is definitely valid, please do post it here
----------
If an answer is helpful, please "Accept answer" or "Up-Vote" for the same which might be beneficial to other community members reading this thread.


