Hi,
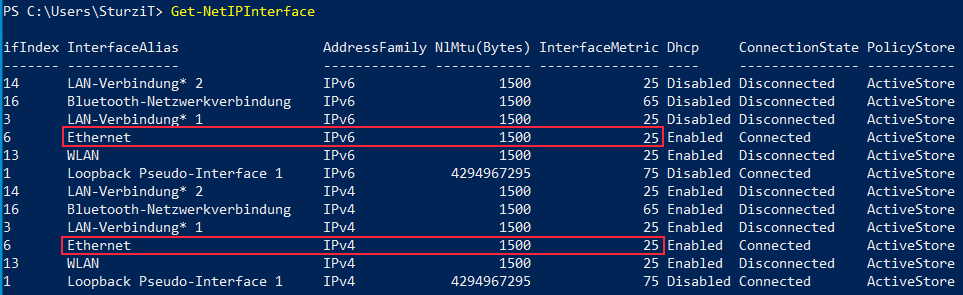
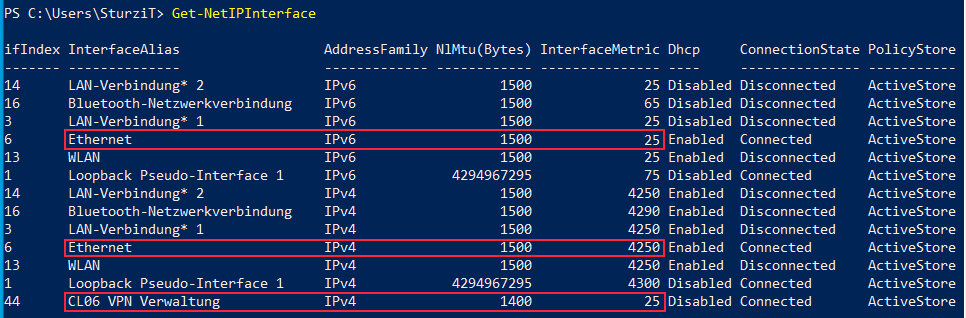
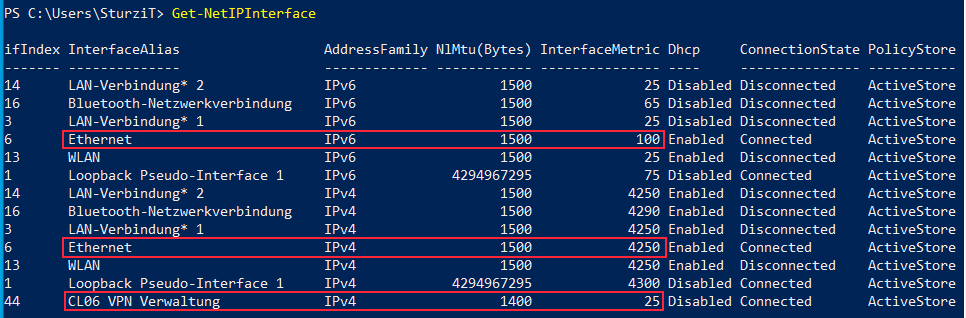
we seem to be running into the same issues.
Thought resolving issues with NRPT would resolve this. As we also had the issue that:
Get-DnsClientNrptPolicy
didn't output anything. It's supposed to forward domain.local and external-domain.tld (for exchange amongst other things as it's not available externally, but does resolve to an external IP externally and thus breaks if it doesn't use the split DNS as it's not accessible through that IP).
This is caused by registry key:
HKLM\SOFTWARE\Policies\Microsoft\Windows NT\DNSClient\DnsPolicyConfig
Which is created by setting a DNS search suffix through GPO.
See here for example: https://social.technet.microsoft.com/Forums/sqlserver/en-US/99b7ad27-e58e-411c-8fa8-12782992ee3b/always-on-vpn-local-dns-issue-for-clients-using-a-nic?forum=winserverNIS
We remove that registry key with the same GPO now, but it's still not stable unfortunately and this only seems to be the case for users with cabled IPv6 connections.