@sakuraime
Thank you for the detailed post and I apologize for the delayed response!
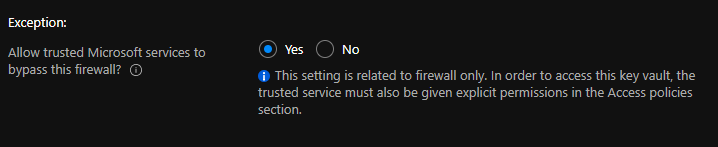
For the Key Vault side of things, when you enable the Key Vault Firewall, you will be given an option to 'Allow Trusted Microsoft Services to bypass this firewall.' The trusted services list does not cover every single Azure service. The trusted services list encompasses services where Microsoft controls all of the code that runs on the service.
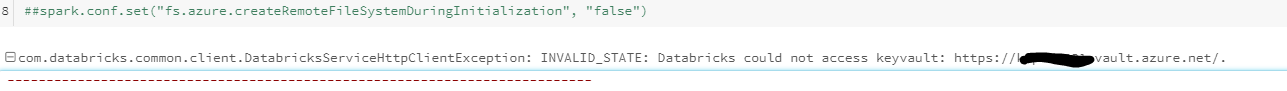
Since you enabled the Azure Key Vault (AKV) Firewall feature, it's normal that your Databricks service was able to access the key vault after you selected "yes, otherwise you would've had to specify a specific IP address for your Databricks service.
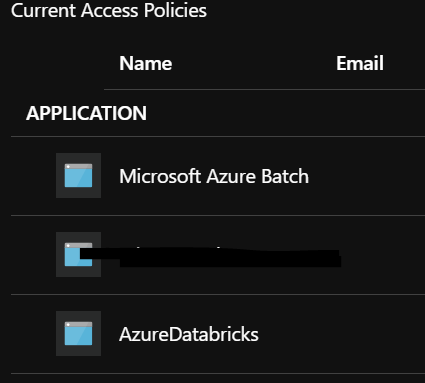
When it comes to the access policy, this is completely normal behavior since access to a key vault is controlled through two interfaces: the management plane and the data plane. As for your current scenario, you granted data plane access to your Azure Databricks, by adding it to your Key Vault access policies.
Additional Link:
Create an Azure Key Vault-backed secret scope
I hope this helps, if you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.