Hello @shiva patpi ,
Thanks for your reply.
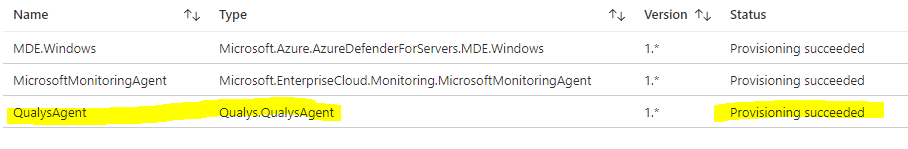
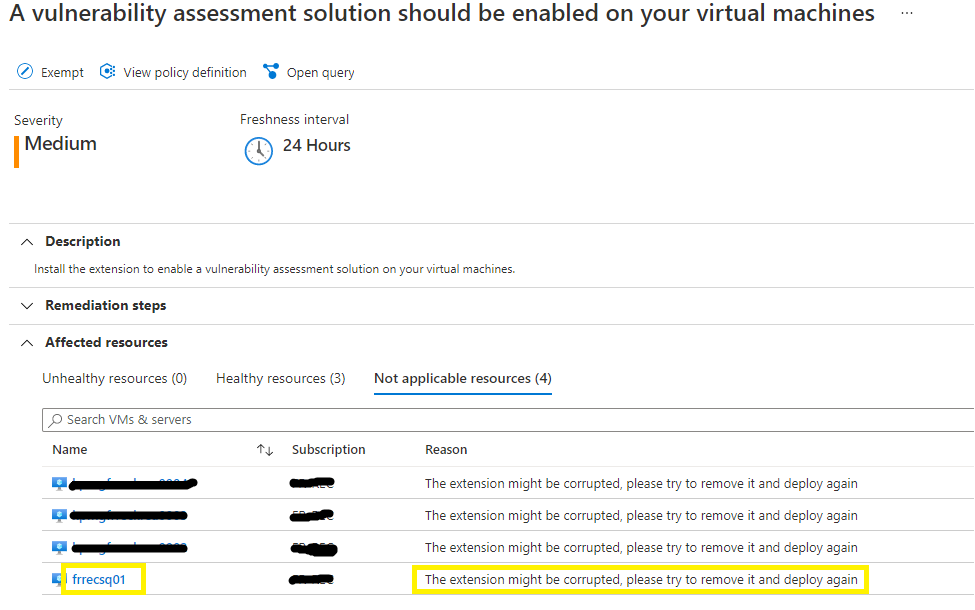
The extension you mention is for the ASC integrated vulnerability scanner, where on my side, I a m using a "BYOL Qualys solution" (exact naming is 'Deploy your configured third-party vulnerability scanner (BYOL - requires a separate license)').
I configured the solution as described in https://qualys-secure.force.com/discussions/s/article/000005837.
I got some more information for the issue I am facing: it appears to be a bug from Qualys, and they plan to fix it/deploy it by mid of April (new release of the agent).
So I will wait until that time!