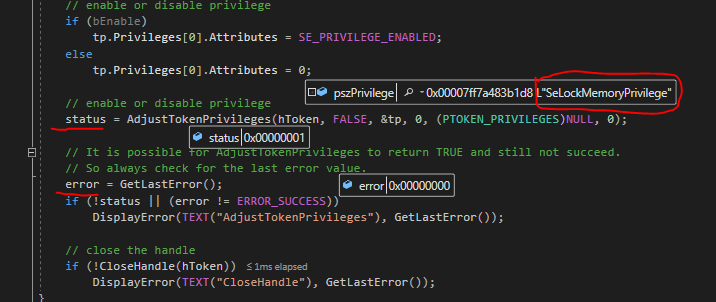
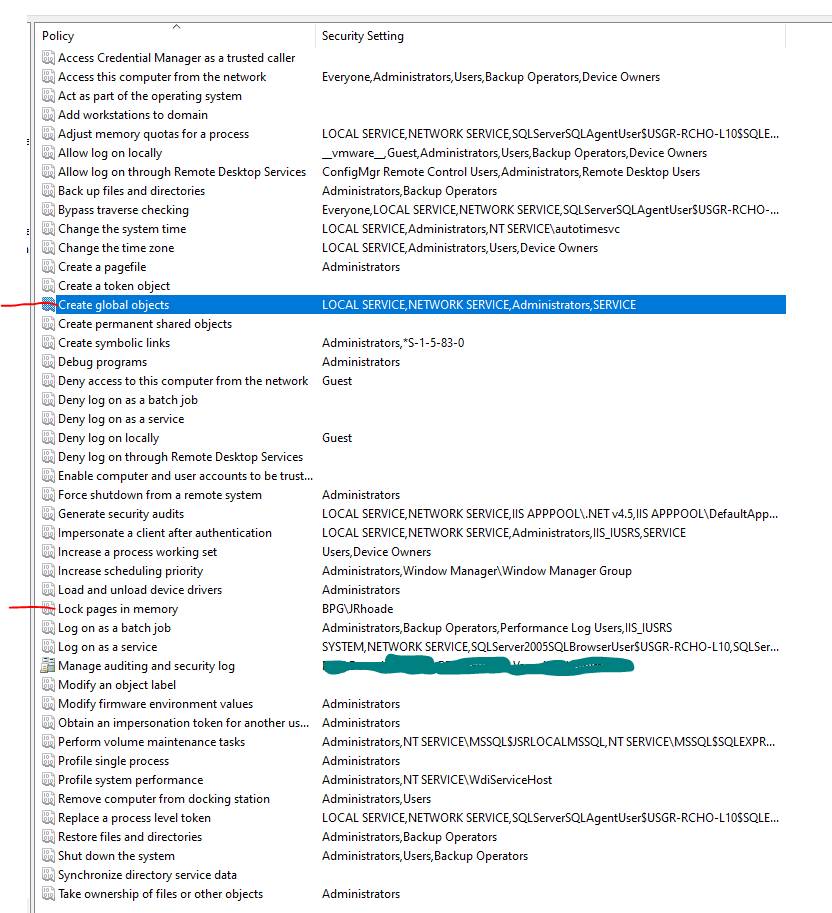
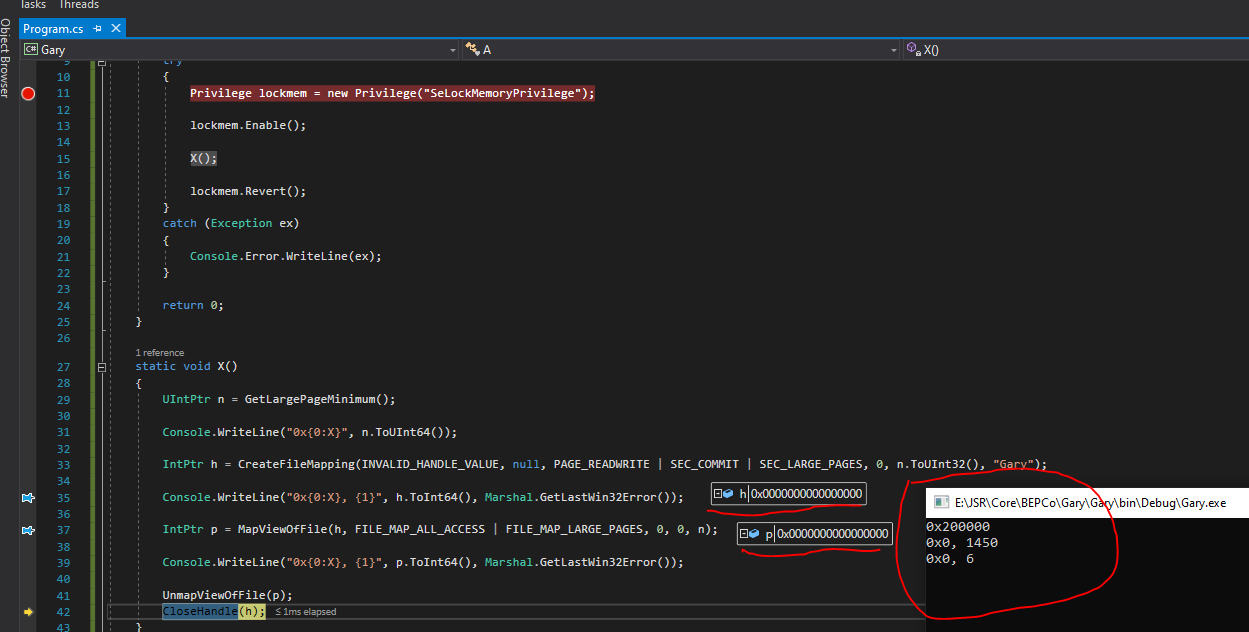
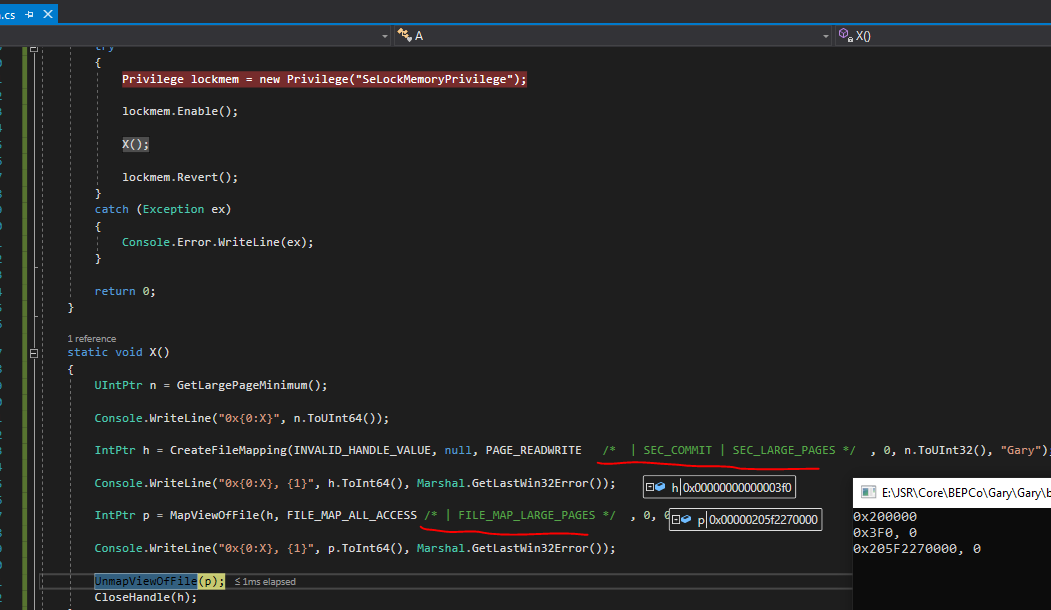
Hello @jay rhoades ,
Can you try compiling and running this program and then reporting what it shows? Success would look something like this:
0x200000
0xD8, 0
0x1B000000, 0
I checked that large page(s) were actually used and it seems that they are:
0: kd> !vad 1B000000
VAD Level Start End Commit
ffffce8206e94b60 6 1b000 1b1ff 0 Mapped LargePag READWRITE Pagefile section, shared commit 0x200
The program can be compiled by just invoking the command "%SystemRoot%\Microsoft.NET\Framework64\v4.0.30319\csc" with the name of the file containing the saved program text. You can add the "-platform:x64" option to the compilation if you want but the default (anycpu) should be OK too if there is nothing unusual about your environment.
Gary
using System;
using System.Reflection;
using System.Runtime.InteropServices;
class A
{
static int Main(string[] args)
{
try
{
Privilege lockmem = new Privilege("SeLockMemoryPrivilege");
lockmem.Enable();
X();
lockmem.Revert();
}
catch (Exception ex)
{
Console.Error.WriteLine(ex);
}
return 0;
}
static void X()
{
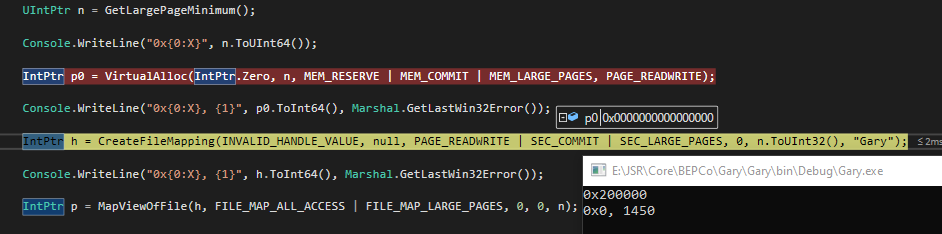
UIntPtr n = GetLargePageMinimum();
Console.WriteLine("0x{0:X}", n.ToUInt64());
IntPtr h = CreateFileMapping(INVALID_HANDLE_VALUE, null, PAGE_READWRITE | SEC_COMMIT | SEC_LARGE_PAGES, 0, n.ToUInt32(), "Gary");
Console.WriteLine("0x{0:X}, {1}", h.ToInt64(), Marshal.GetLastWin32Error());
IntPtr p = MapViewOfFile(h, FILE_MAP_ALL_ACCESS | FILE_MAP_LARGE_PAGES, 0, 0, n);
Console.WriteLine("0x{0:X}, {1}", p.ToInt64(), Marshal.GetLastWin32Error());
UnmapViewOfFile(p);
CloseHandle(h);
}
static IntPtr INVALID_HANDLE_VALUE = new IntPtr(-1);
const uint SEC_COMMIT = 0x08000000;
const uint SEC_LARGE_PAGES = 0x80000000;
const uint FILE_MAP_ALL_ACCESS = 0x000F001F;
const uint FILE_MAP_LARGE_PAGES = 0x20000000;
const uint PAGE_READWRITE = 0x04;
[DllImport("kernel32.dll", SetLastError = true)]
static extern bool CloseHandle(IntPtr handle);
[DllImport("kernel32.dll", SetLastError = true, CharSet = CharSet.Unicode)]
static extern IntPtr CreateFileMapping(IntPtr file, object sa, uint protect, uint n2, uint n, string name);
[DllImport("kernel32.dll", SetLastError = true)]
static extern IntPtr MapViewOfFile(IntPtr mapping, uint access, uint m2, uint m, UIntPtr n);
[DllImport("kernel32.dll", SetLastError = true)]
static extern bool UnmapViewOfFile(IntPtr p);
[DllImport("kernel32.dll")]
static extern UIntPtr GetLargePageMinimum();
}
class Privilege
{
Type t = Type.GetType("System.Security.AccessControl.Privilege");
object privilege;
public Privilege(string name)
{
privilege = t.GetConstructor(new Type[] {typeof(string)}).Invoke(new object[] {name});
}
public void Enable()
{
t.GetMethod("Enable", BindingFlags.Public | BindingFlags.Instance).Invoke(privilege, null);
}
public void Revert()
{
t.GetMethod("Revert", BindingFlags.Public | BindingFlags.Instance).Invoke(privilege, null);
}
}


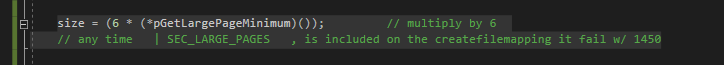
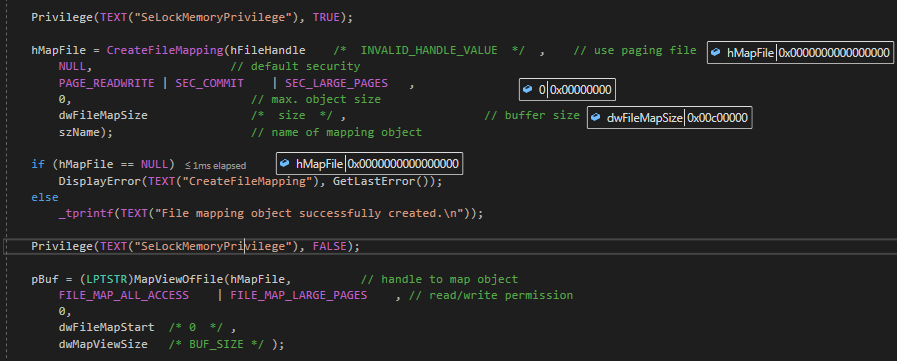
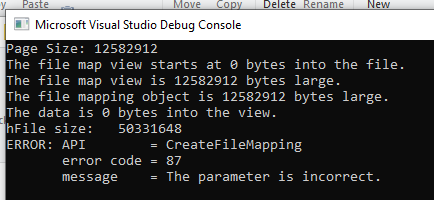
 mapping file,
mapping file,