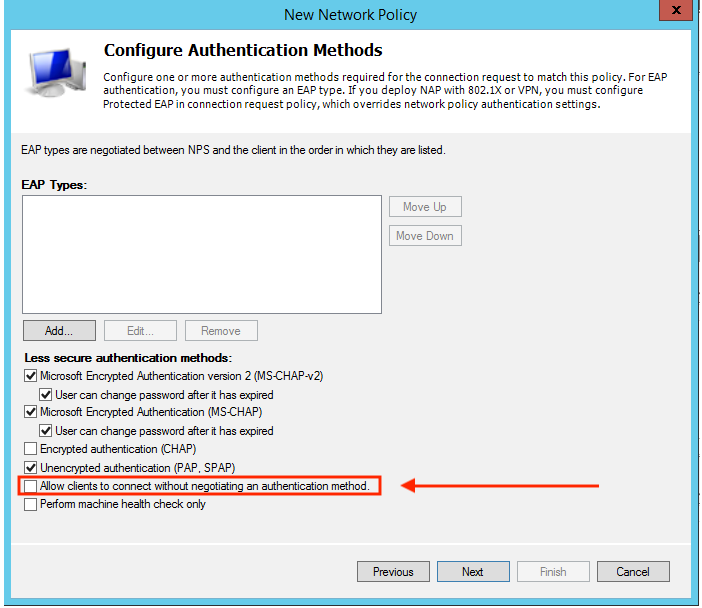
While it is true you need a username and password to authenticate, I did not ask about authentication. I asked about authorization only. I also discovered that this is 100% possible with NPS. The ASA profile is configured to send an Authorization only request to the NPS server after it Authenticates from a different source (in my case Okta). Then, in the NPS you have to check the "Allow clients to connect without negotiating an authentication method" box shown in the image below in the Network policy. This allows the ASA to receive the attribute back from the network rule that satisfies the condition. In my case the condition is that the user is in a specific AD group.
You can also set the policy in the ASA to fail Authentication if the user is not present in the Authorization database. This can add an extra layer of security. Even if the user is Authenticated by the different source (in my case Okta) Any Connect will not allow the user to connect if they are not also in one of the AD groups that is defined in the NPS server for Authorization.