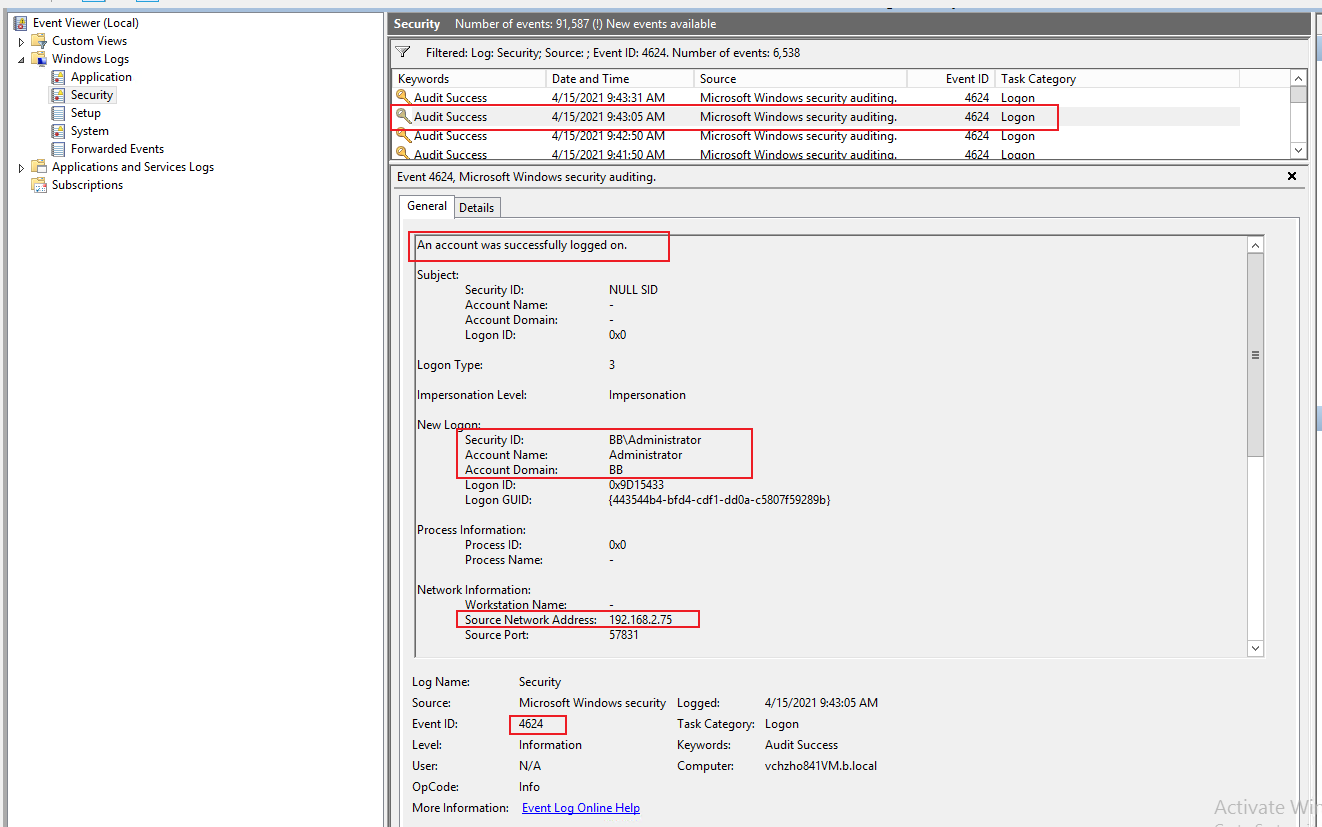
Hello @matteu31 ,
I mostly understand your issue, but I did not understand the bit about not being able to distribute the root certificate.
I can only think of three options:
- Turn up Active Directory logging (https://learn.microsoft.com/en-us/troubleshoot/windows-server/identity/configure-ad-and-lds-event-logging) to the maximum and see whether any of the logged events meet your needs.
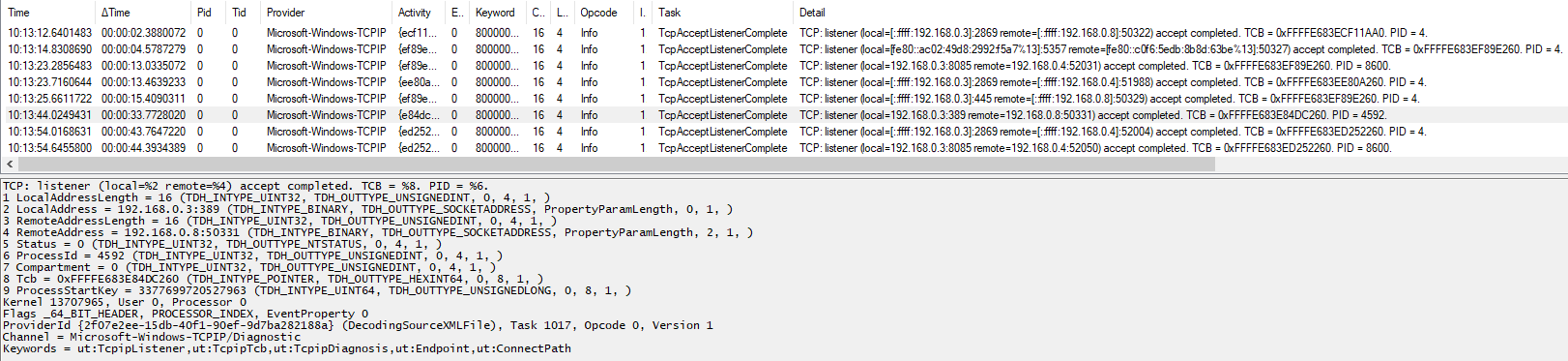
- Trace all network traffic (filtering for LDAP ports if possible) and analyze their contents (if possible - the traffic might be protected by SASL confidentiality).
- Use heuristics to guess whether LDAP is being protected by TLS. For example, capture the connections as before and trace the Microsoft-Windows-SChannel-Events provider too, looking for AcceptSecurityContext events (which could signal, among other things, that a TLS channel is being established); correlating the events via process id and time, it might be possible to (unreliably) infer whether LDAP is being protected by TLS.
Gary