
Hello @Bojan Zivkovic ,
Thank you for posting here.
We can see one domain user on one domain client wants to access \server\shared folder to read a file. The process follows this sequence (the user has already logged on, and the user has requested and received a ticket for the workstation):
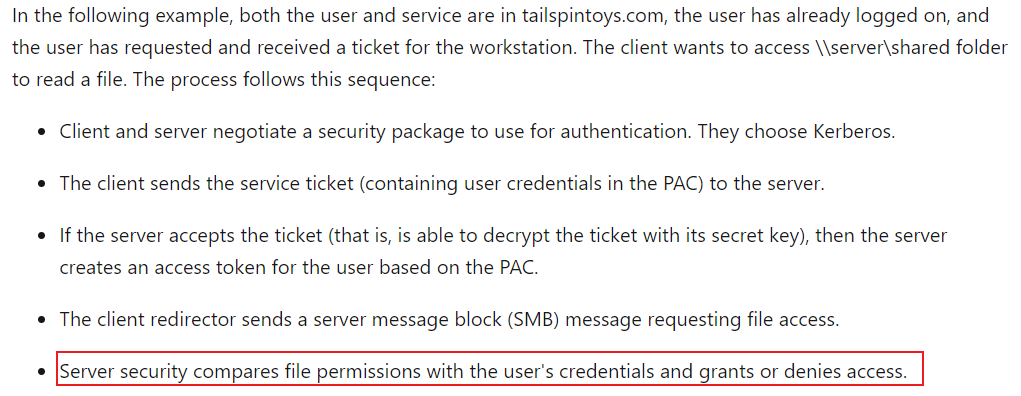
Then for a user session that originally logged in normally, the user's access token only includes the permissions that the user had when logging in.
Winlogon creates a window station and several desktop objects for the user, attaches the user's access token, and starts the shell process the user will use to interact with the computer. The user's access token is subsequently inherited by any application process that the user starts during the logon session.
When the user logs out, the credential cache is refreshed, and all service tickets and all session keys are destroyed.
If the user is allowed to change the permissions of the shared folder (the original user did not have permission to the shared folder, now the user is given the permission one the shared folder), log off the user, and log in to the client with the user’s account again.
Only the new permissions are included in the user's access token in user's new logon session, and then the user can access the shared folder.
For more information we can refer to link below.
How the Kerberos Version 5 Authentication Protocol Works
https://learn.microsoft.com/en-us/previous-versions/windows/it-pro/windows-server-2003/cc772815(v=ws.10)?redirectedfrom=MSDN
Hope the information above is helpful.
Should you have any question or concern, please feel free to let us know.
Best Regards,
Daisy Zhou
