Hi @Ryan Ash · Thank you for reaching out.
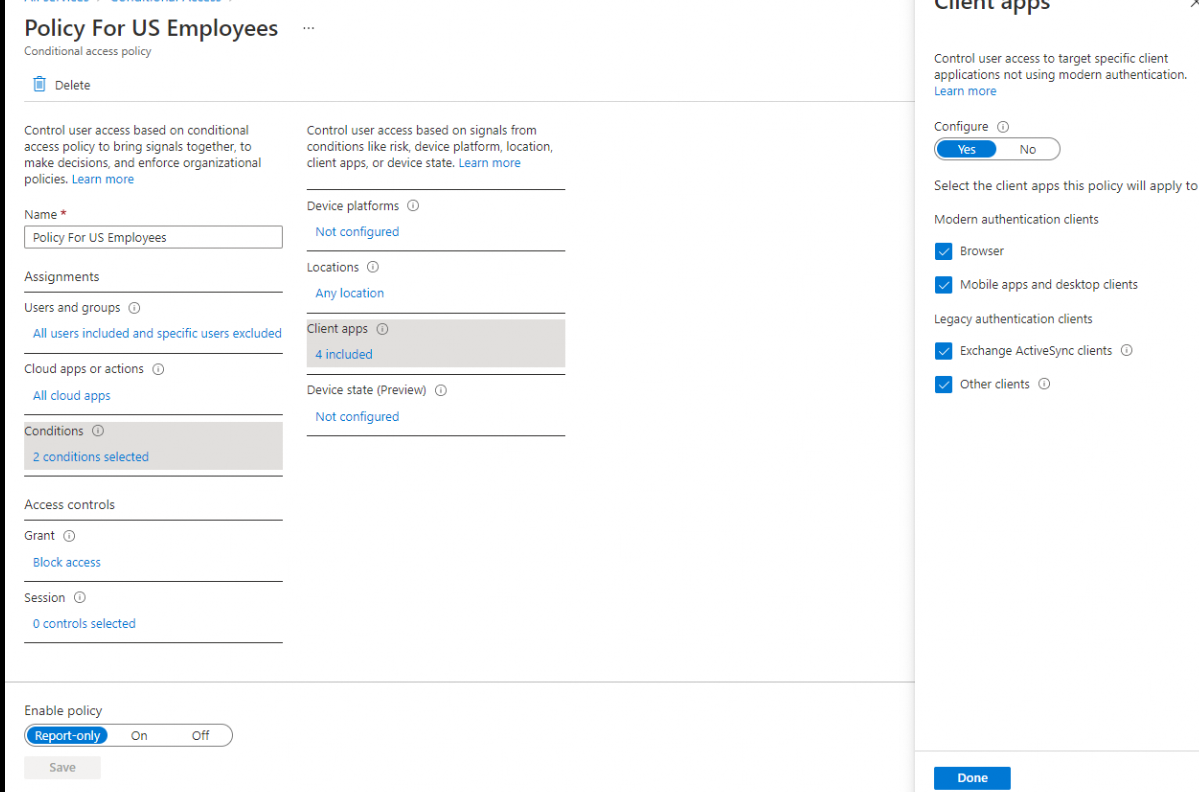
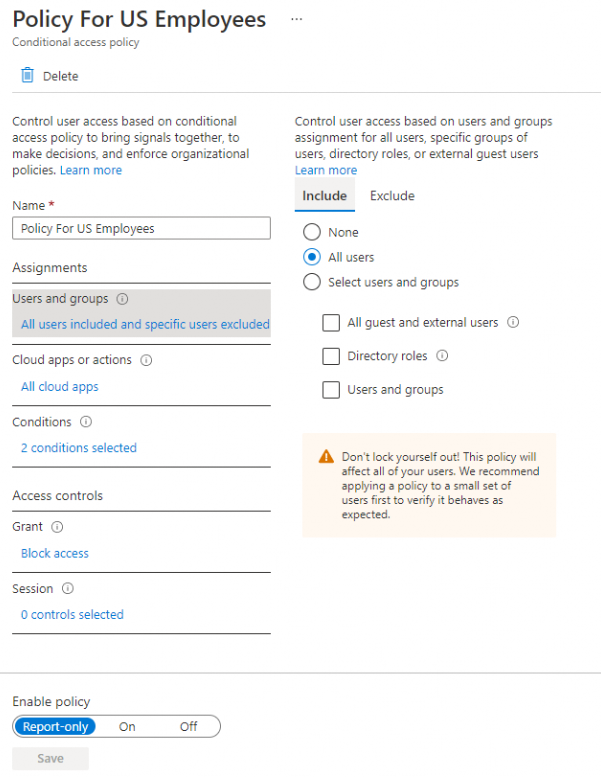
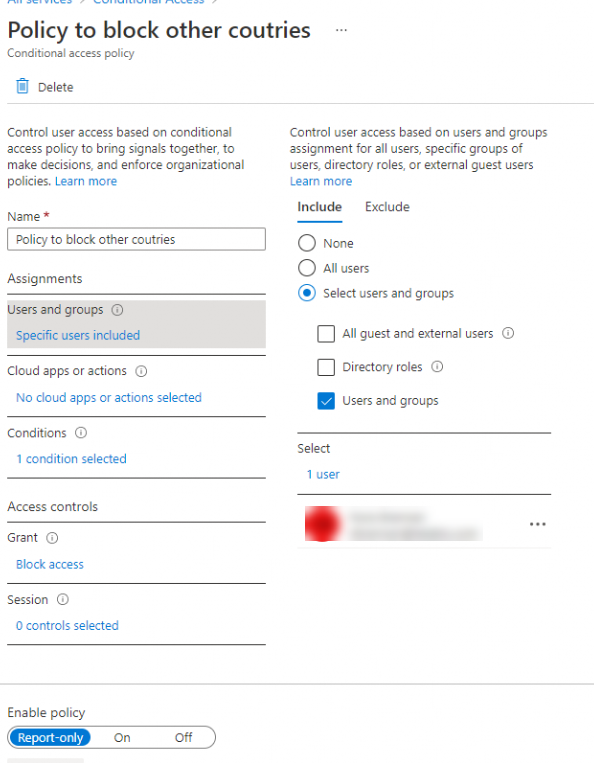
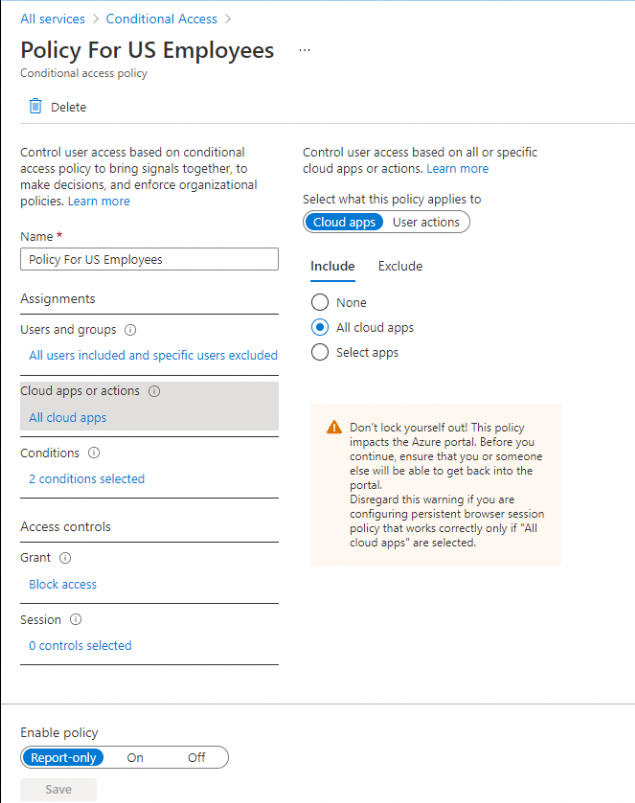
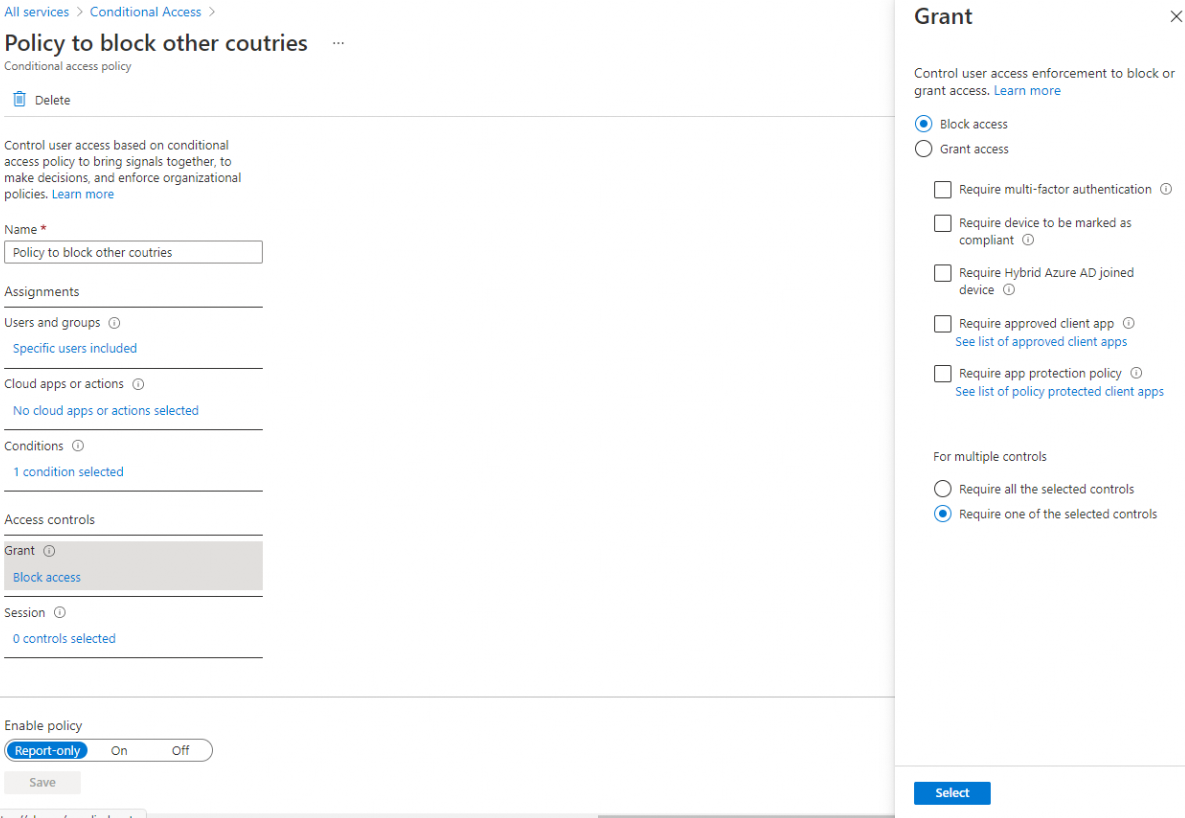
Looking at the screenshots, you have configured 2 policies (mentioned below) to block all access from any country outside of the US.
- Policy For US Employees
- Policy to block other countries
A better way of configuring Conditional Access for this purpose would be to:
- First create a Named Location by navigating to Azure AD > Security > Named Locations > + Countries location > provide a name and select United States.
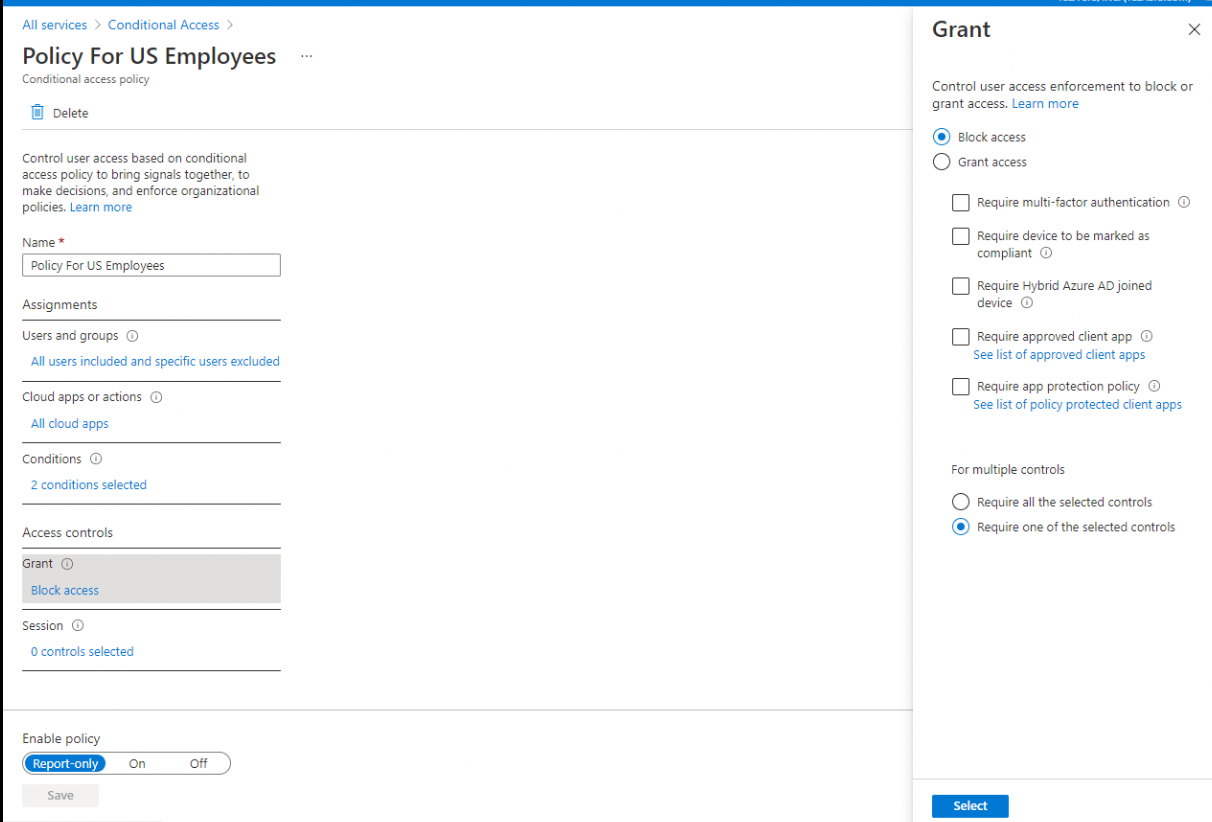
- Create single CA policy, where you will include Any location, exclude Named location created for the country US, and Block access. Please refer to below screenshot, where I have configured bare minimum settings to achieve your requirement:
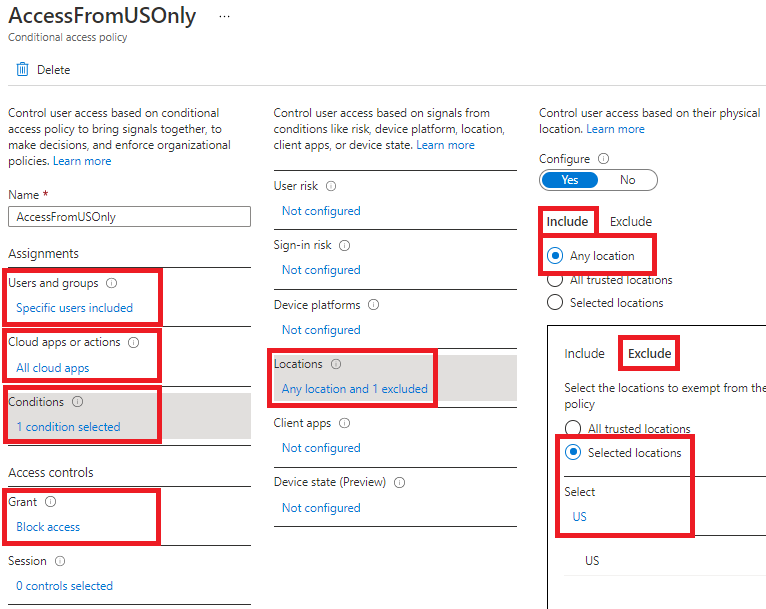
Now, the policy will only apply when someone tries to access any Cloud App outside of the US and access will be blocked. As US is excluded from the Policy, it will not apply when cloud apps are accessed from within the US and access will be granted (provided no other policy is blocking the access).
-----------------------------------------------------------------------------------------------------------
Please "Accept the answer" if the information helped you. This will help us and others in the community as well.