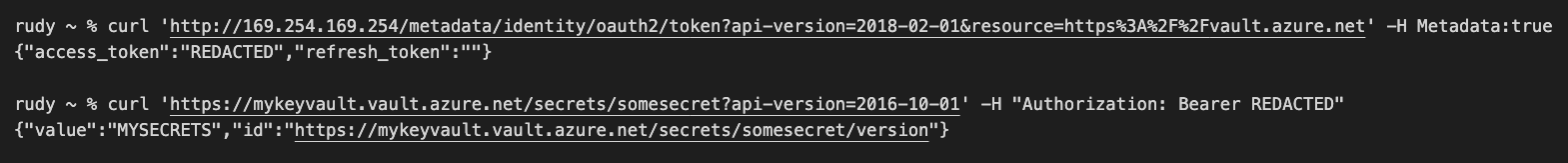
@Anonymous
Thank you for your detailed post and I apologize for the delayed response!
I've forwarded your feedback to our AKV team and will update any responses from their end as necessary. Additionally, I'd recommend leveraging our User Voice forum to leave feedback as well so our engineering team can look into improving this feature.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.