so before for communicating with SPO you have to register your app via appregnew.aspx (where you get clientId and clientSecret) and then grant permissions to this app via appinv.aspx (using xml request).
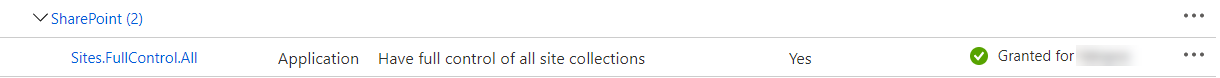
In new approach you register add in Azure AD (Azure portal > AAD > App registrations) first. After that go to API permission tab of this app and add necessary permissions for Sharepoint: it may be app permissions or delegated (since you mentioned DisableCustomAppAuthentication I assume that you use app permissions). After that grant Admin consent on the same page if needed. E.g. if you need full control on all site collections permissions may look like that:
After that you have to choose how you want to authenticate using this app: using clientSecret or certificate. Both are configured on Certificates & secrets tab of the app. Client secret is simpler but is considered outdated. MS recommends to use cert-based authentication: it is little bit more complex to configure - see Granting access via Azure AD App-Only.