Hi anonymous user,
Thanks for clarifying the ask. As per the current ADF SharePoint connector limitation, it uses service principal authentication to connect to SharePoint. This is limitation by design at the moment. Hence managed identity not an option
My main query here is, after following the above mentioned link, it expects the client credentials to be written in body part. I need a workaround to that specific part for my solution to be implemented in my case. So if you can help me with that specific part, would be really appreciated.
In order to avoid exposing client credentials in the body of the web activity while getting the access token, you can store the value of the client credentials in Azure Key Vault. Then have another web activity before GetBearerToken web activity to retrieve the client credentials from Key Vault using Get Secret API - GET {vaultBaseUrl}/secrets/{secret-name}/{secret-version}?api-version=7.1
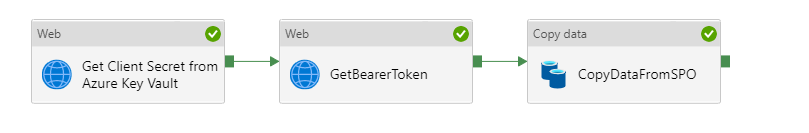
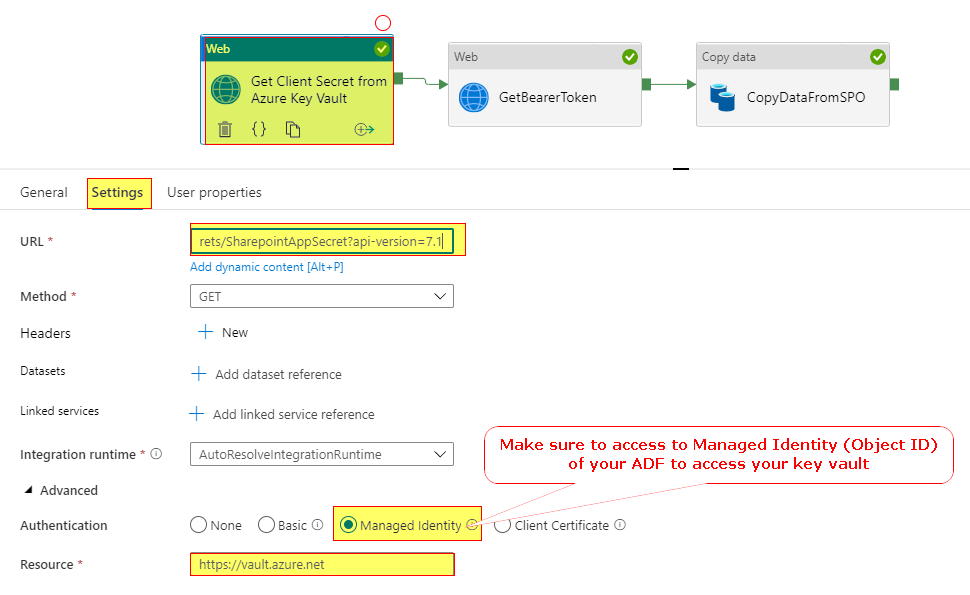
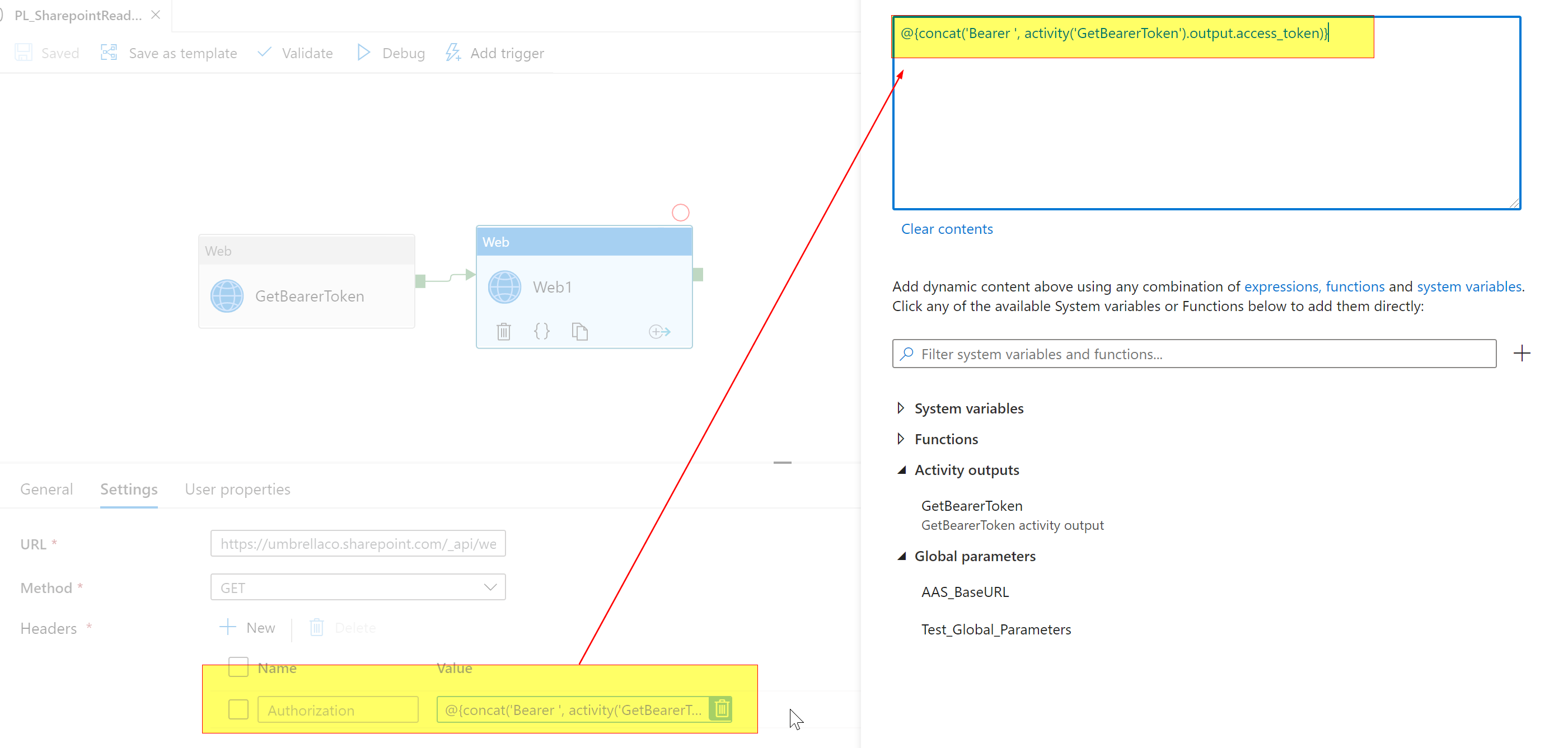
And use output.value of that web activity in body of the GetBearerToken web activity using a dynamic expression as below. This way you can avoid exposing the client credentials in your ADF web activity.
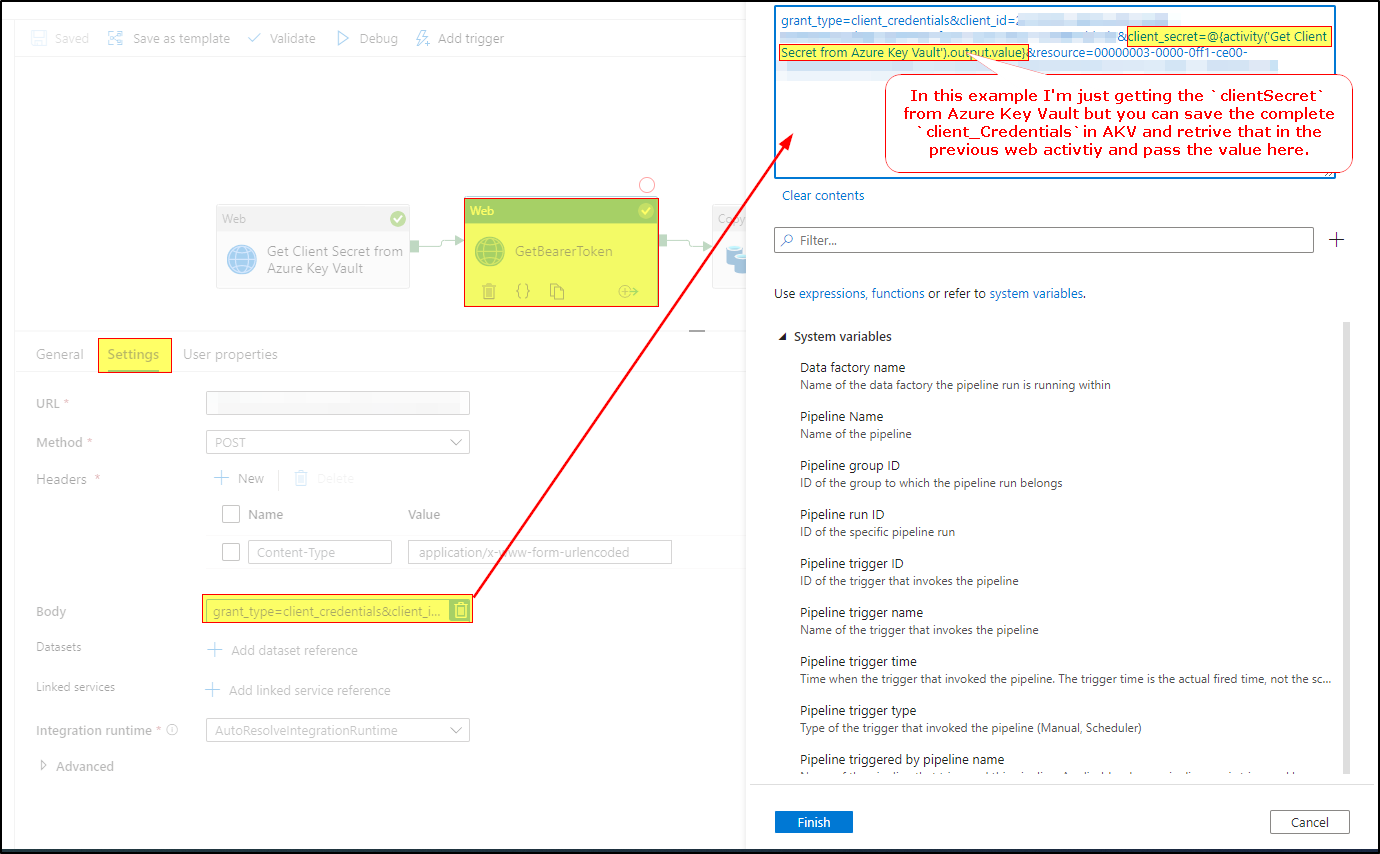
Hope this info helps. Do let us know if you have further query.
----------
Please don’t forget to Accept Answer and Up-Vote wherever the information provided helps you, this can be beneficial to other community members.