Not unless you're exporting them somewhere. If you are using Office 365, you can use the Unified audit log, which ingests events from Azure AD as well: https://learn.microsoft.com/en-us/microsoft-365/compliance/search-the-audit-log-in-security-and-compliance?view=o365-worldwide
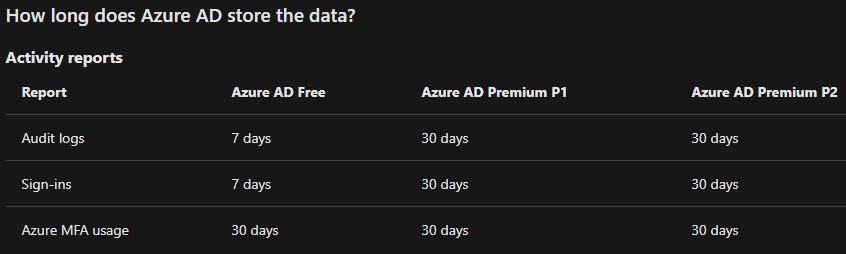
As detailed in the article, depending on the license you can get events from up to 90 days/1 year back.