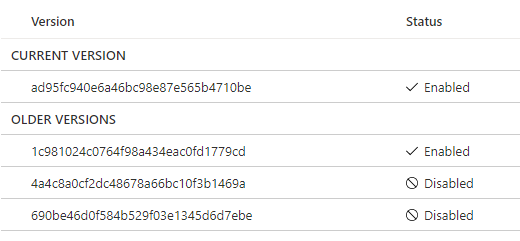
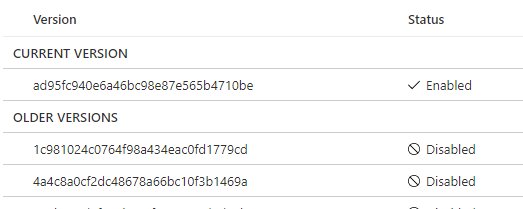
Here's what happens, by default, when you create your master key, you specify the name of the key under "WITH_PROVIDER_KEY_NAME = 'ContosoKey'". As you can see, that's not specifying a key version which basically means "always call the latest available". The issue with that is that if at the moment you created the master key, the latest version was v1, the backup will be done with ContosoKey v1, and when you create a v2, then v2 becomes the latest available version and that won't let you restore the backup, Ideally, you should be able to point the restore operation to a specific key's version, however, that's doesn't seem to be possible and backing up the key to later on restore it in AKV won't work if you have purge protection turned on in your Key Vault.
I would say that a good workaround would be to create a master key-specific version per DB, I mean, you can create the master key like this:
CREATE ASYMMETRIC KEY [EKM_CMK_799ac65f4c2f4f29bb1adf10b8f627d9]
FROM PROVIDER [AzureKeyVault_EKM]
WITH PROVIDER_KEY_NAME = 'ContosoKey/799ac65f4c2f4f29bb6adf10b8f625d8',
CREATION_DISPOSITION = OPEN_EXISTING;
Where '/799ac65f4c2f4f29bb6adf10b8f625d8' represents the specific version of the key that will be used. With this, it doesn't matter if you update the Key with a new version, it will always attempt to use 799ac65f4c2f4f29bb6adf10b8f625d8 version for DB operations such as recovering a backup or at least, that's my theory (yet to be tested).