@fhtino
Thank you for the detailed post and I apologize for the delayed response!
Based off the information from your thread:
-You can sign-in with users from your AzureAD Tenant.
-Authentication doesn’t work from other personal/consumer accounts (Outside of your AzureAD tenant).
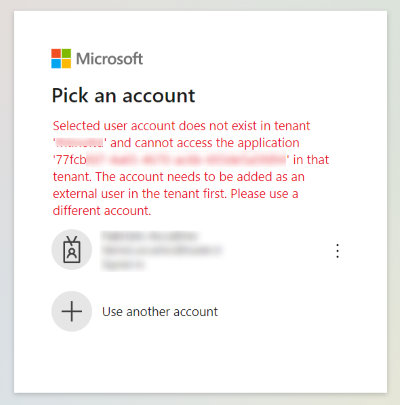
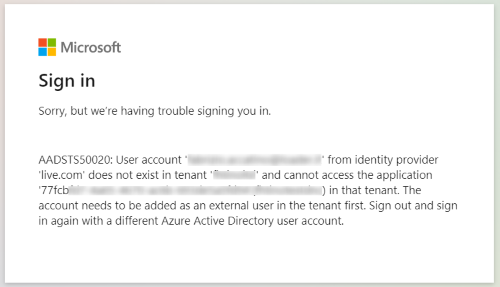
Error Message:
AADSTS50020: User account 'xxxxxxx' from identity provider 'live.com' does not exist in tenant 'xxxxxxxx' and cannot access the application 'xxxxxxxxxx'(xxxxxxx) in that tenant. The account needs to be added as an external user in the tenant first. Sign out and sign in again with a different Azure Active Directory user account.
Findings:
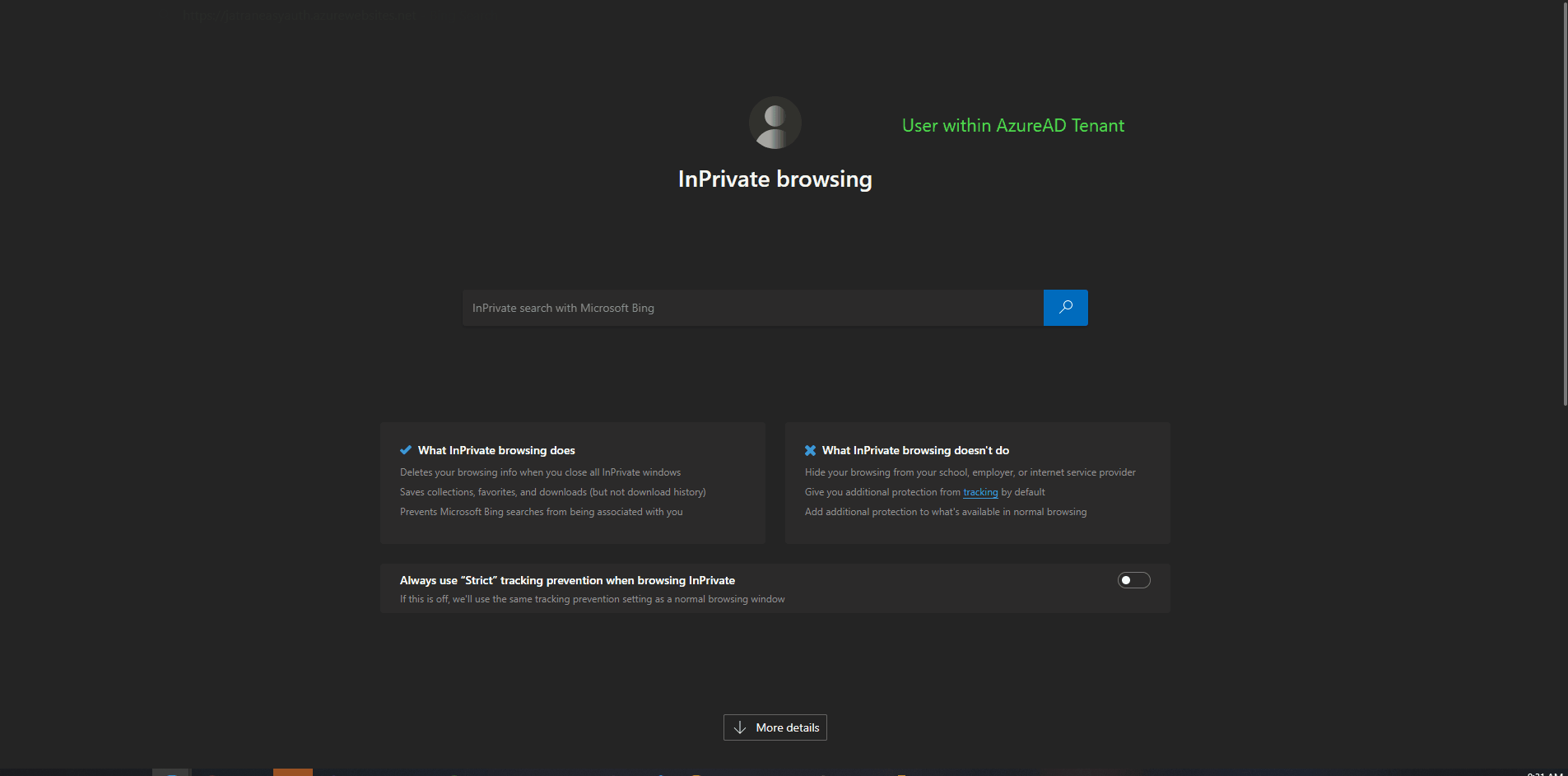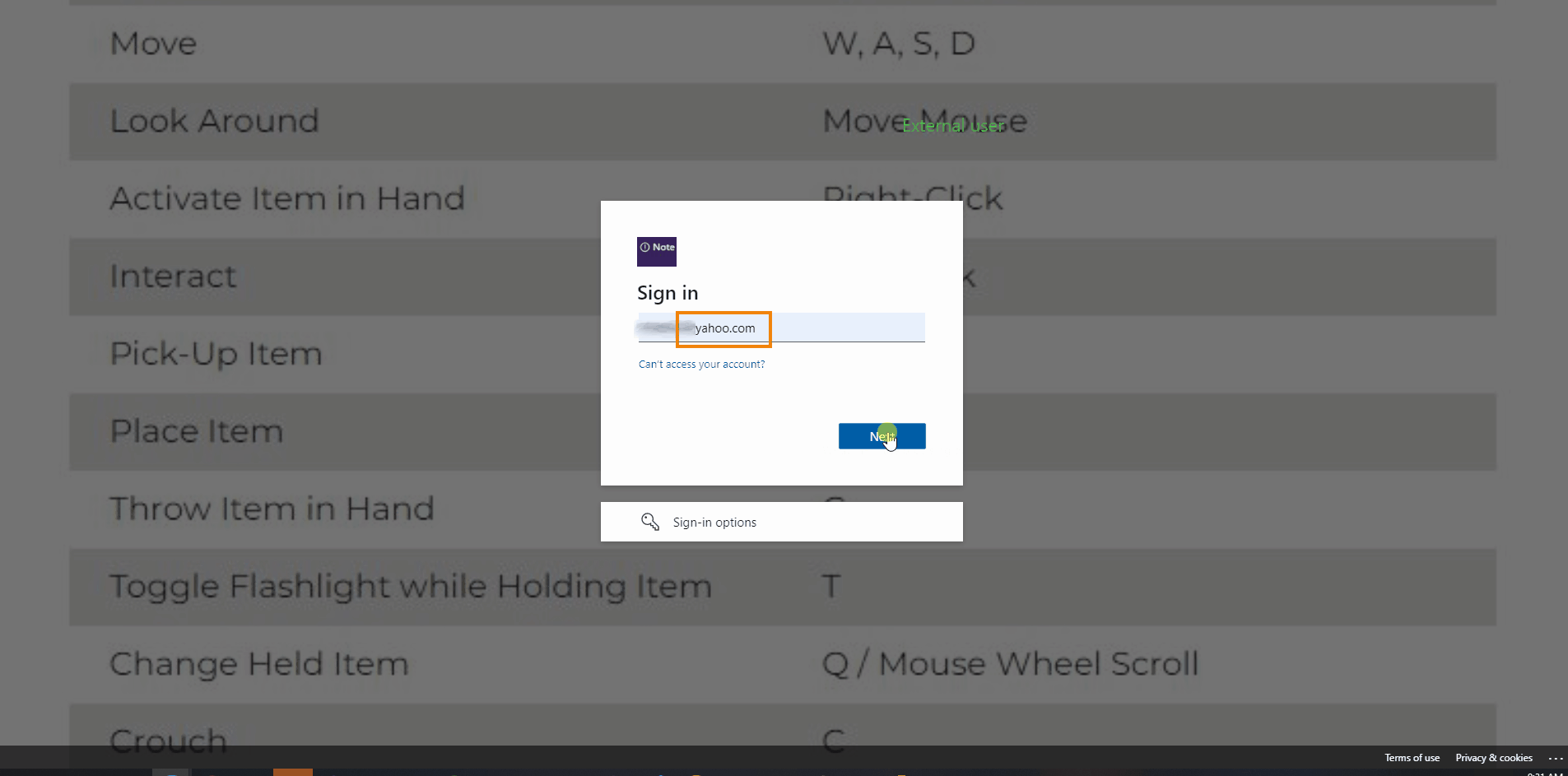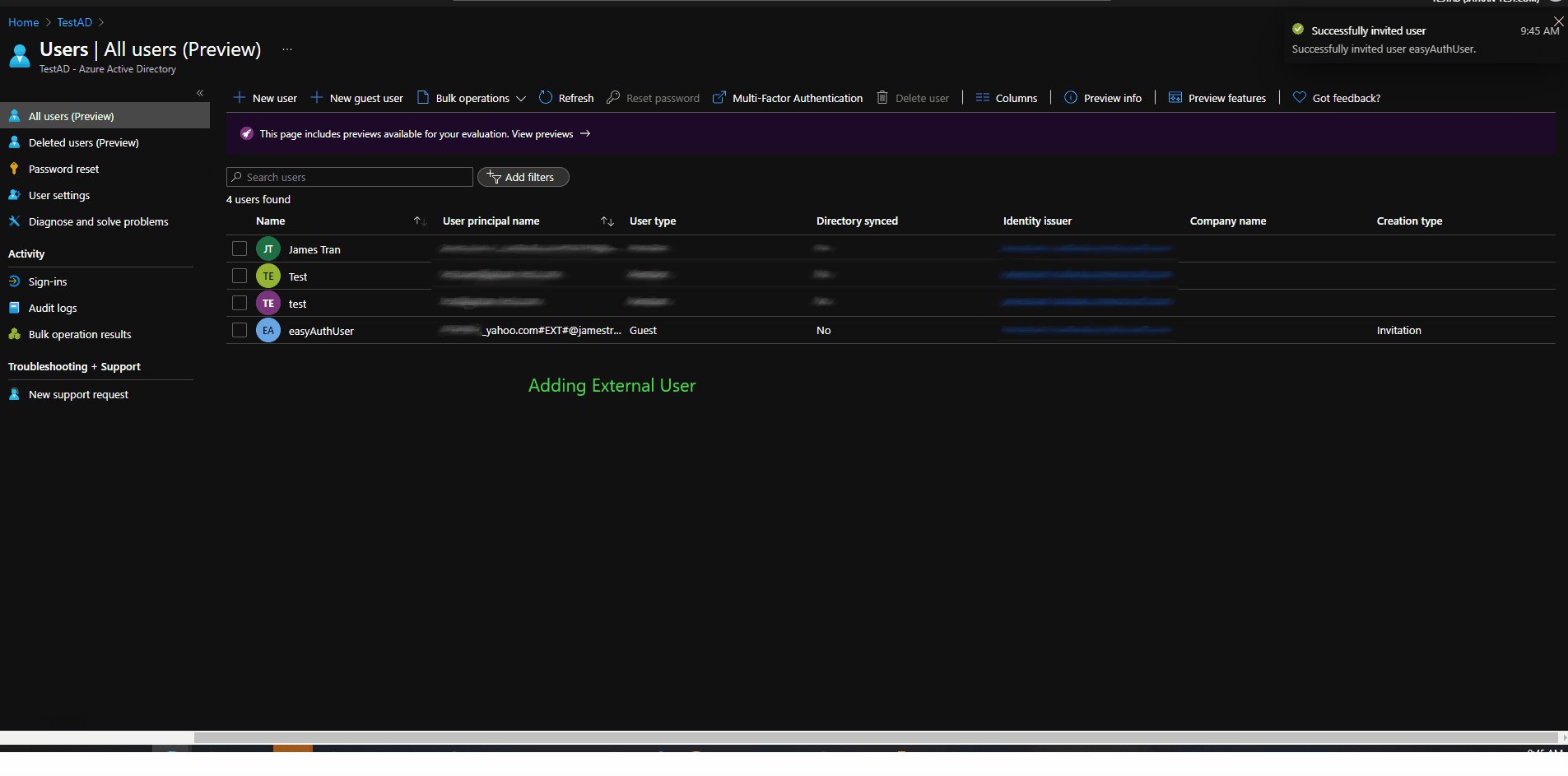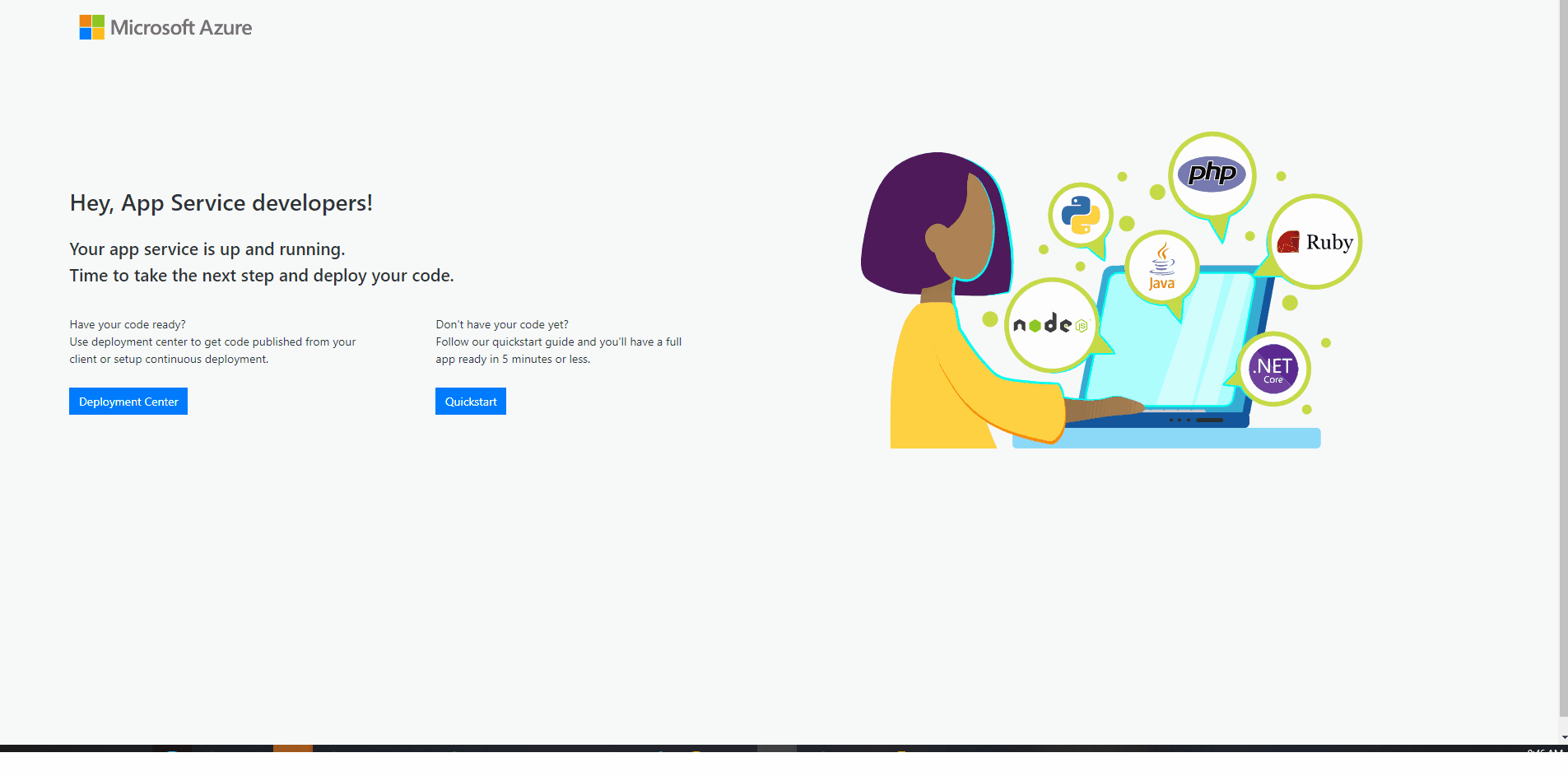
Following this article - Tutorial: Add authentication to your web app running on Azure App Service, I was able to reproduce your issue. However, after adding my external account to my AzureAD tenant, I was able to successfully sign-in to my web app.
Next Steps:
- From your error message, you'll need to manually add the user you're trying to sign-in with to your Azure Active Directory.
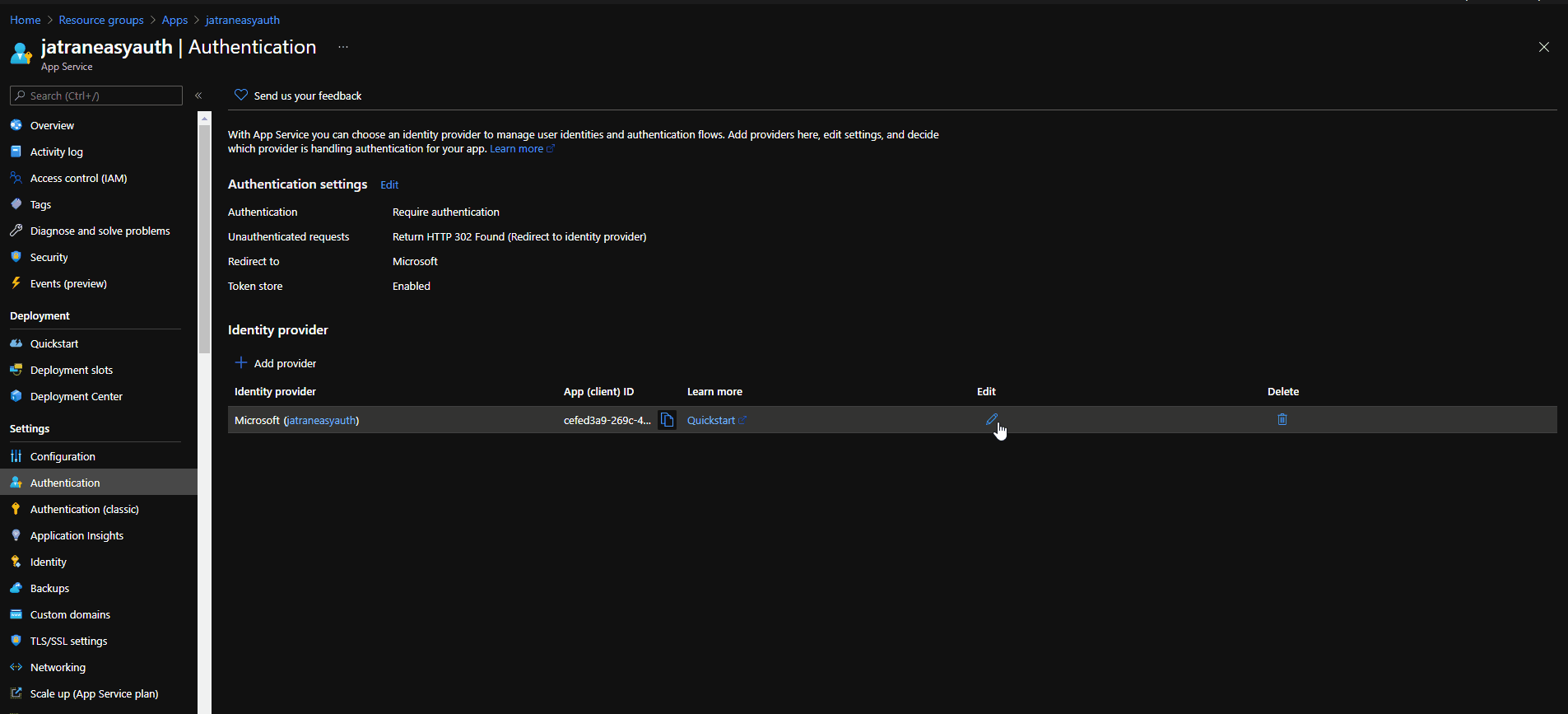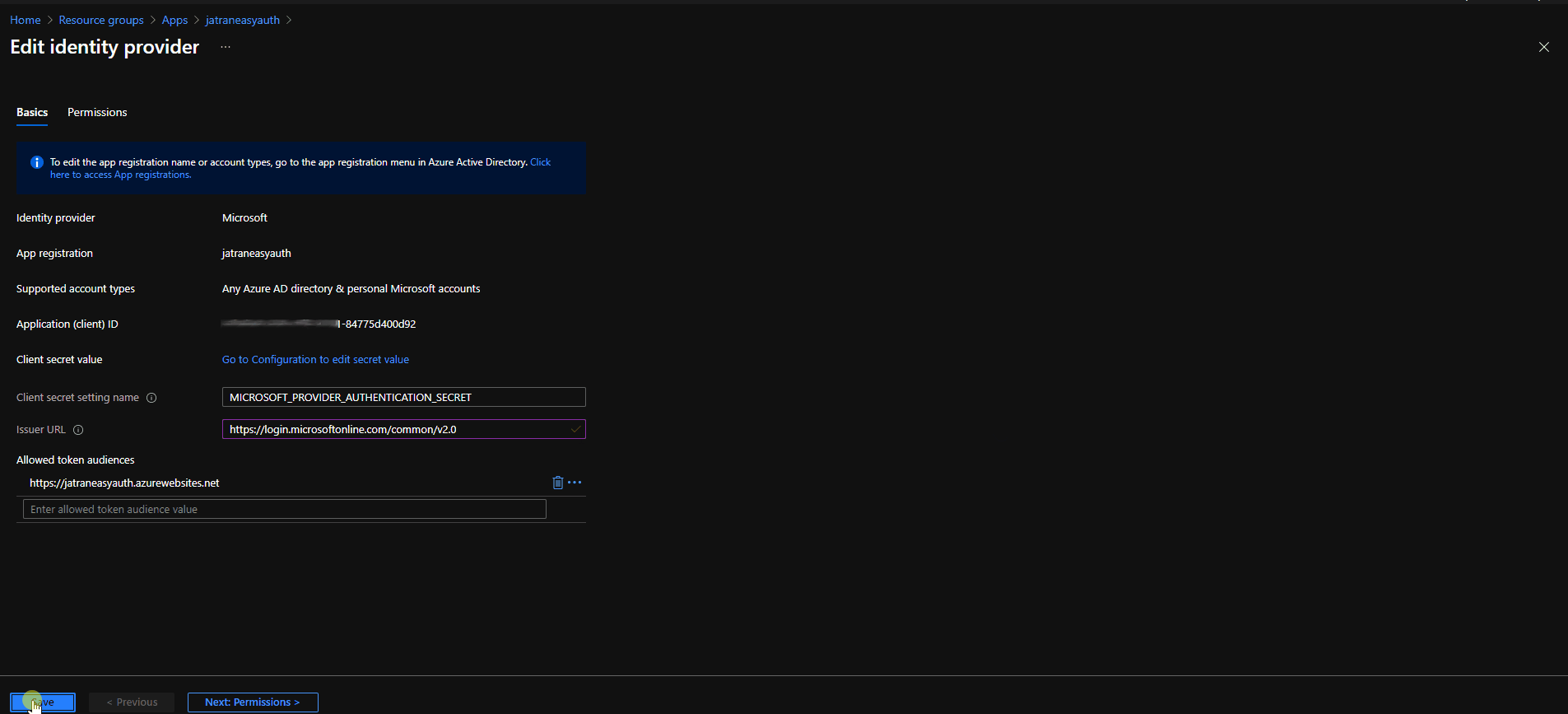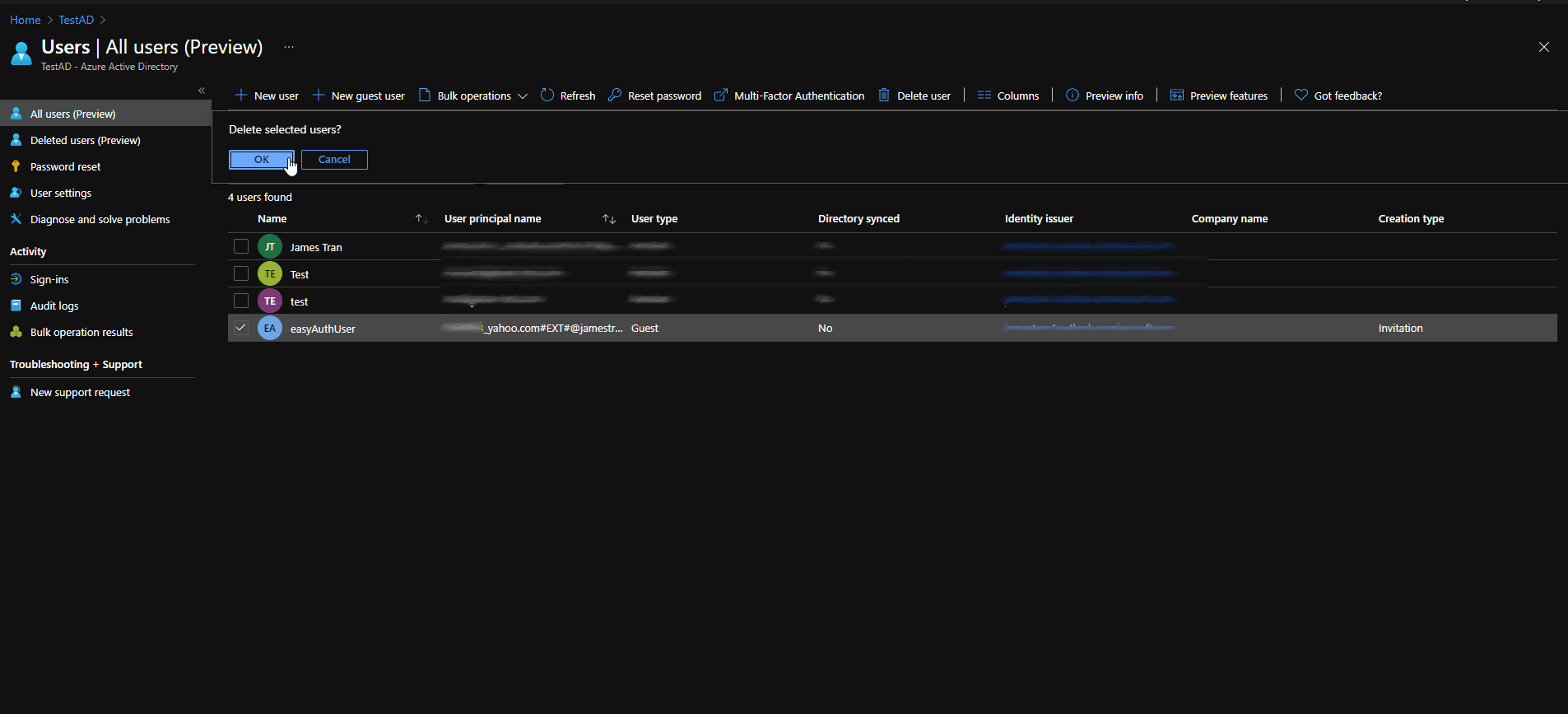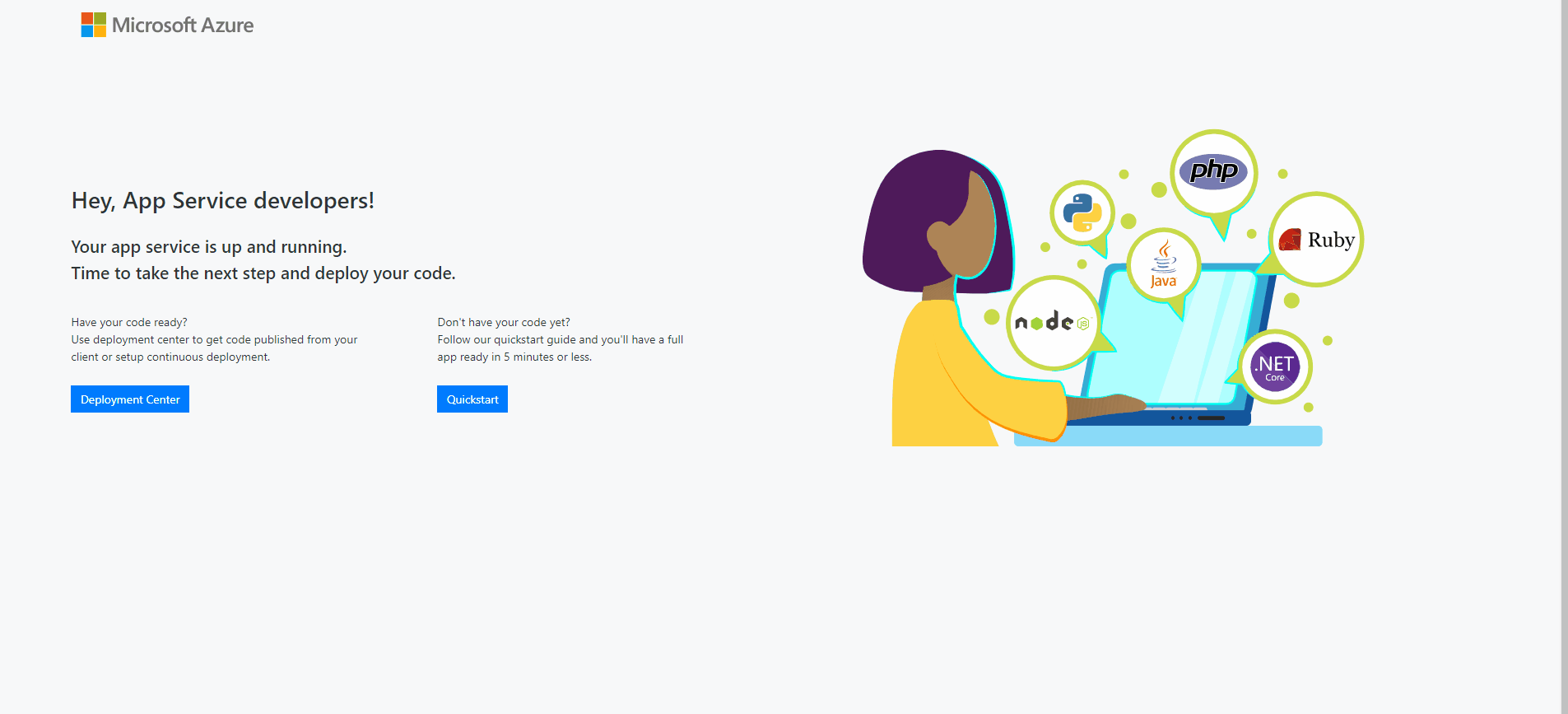
- You can also add a new Issuer URL (Copy and Save the old one as needed).
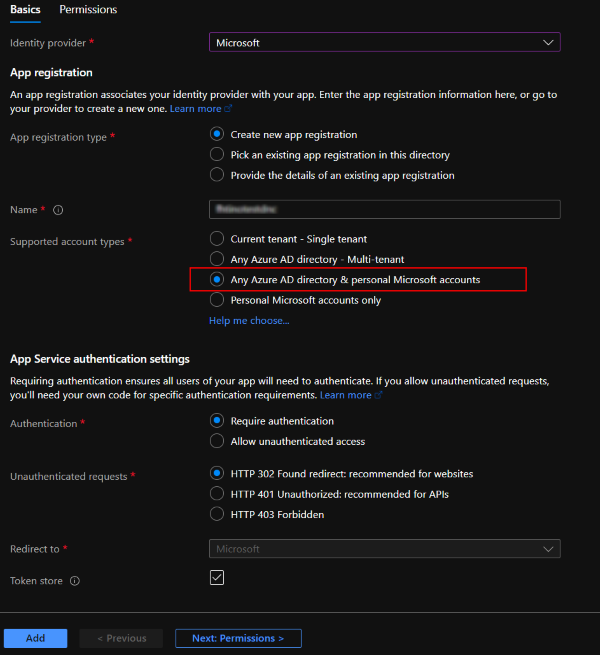
Navigate to your Web App -> Authentication -> Edit your Identity Provider -> Issuer URL.
URL: https://login.microsoftonline.com/common/v2.0
If you have any other questions, please let me know.
Thank you for your time and patience throughout this issue.
----------
Please remember to "Accept Answer" if any answer/reply helped, so that others in the community facing similar issues can easily find the solution.