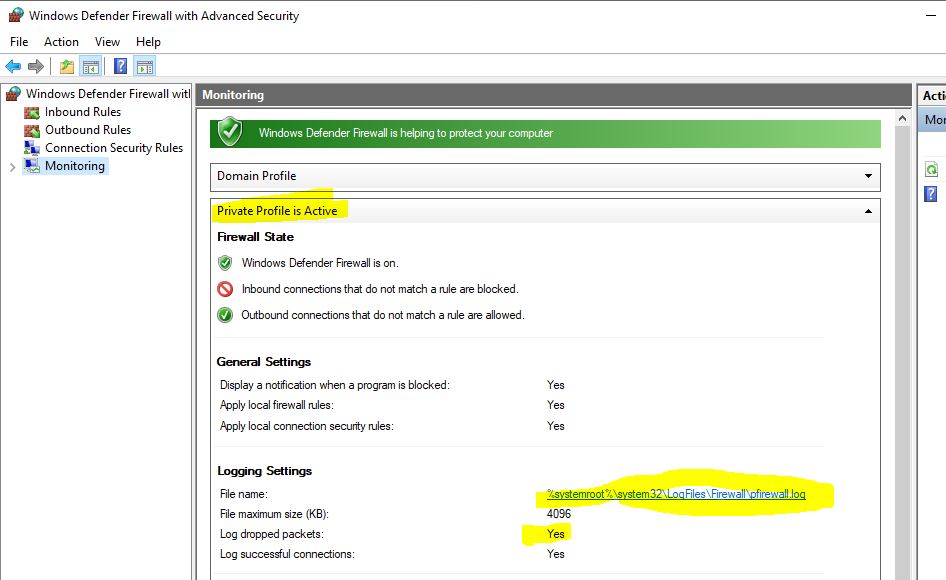
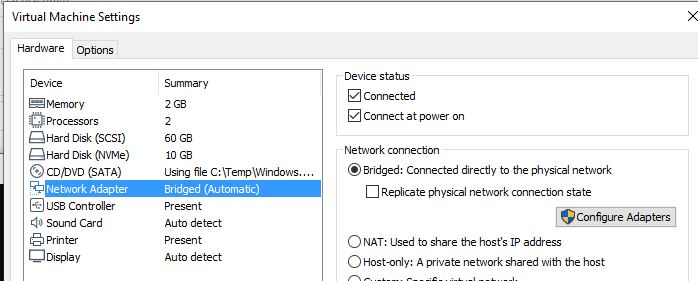
@MotoX80 , thank you for your reply. The "bridged" option that you suggested works, but for some reason I do not want to change my VM interface card from NAT to bridged. I also enabled the logging of dropped packets as you suggested. When I opened the log file, I found that the first data packets from the TFTP server are actually being dropped by the Wi-Fi interface of my laptop. When I disabled the windows 10 firewall, everything worked fine.
BTW: from the laptop. even with the firewall active, I can use the Windows TFTP client to request the same file from the same TFTP server without any problem.
How come my laptop sends the client request to the TFTP server (after translating the source IP of the original TFTP packet to it's own IP address) and then drops off the reply packet from the server?
I also noticed that the TFTP server reply packets have a randomly selected UDP source port instead of UDP port 69. Could that be the problem?