@AnkurSoni-4dx
Thank you for following up on this. Please see below for words from our product team.
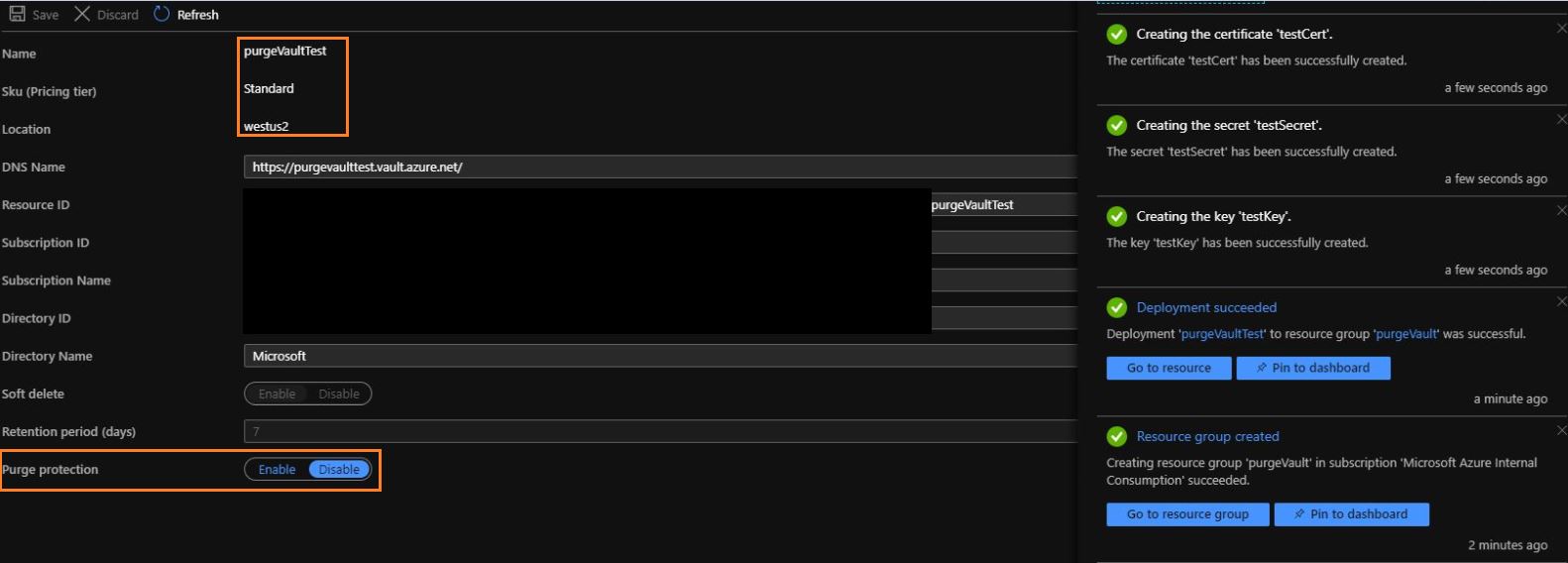
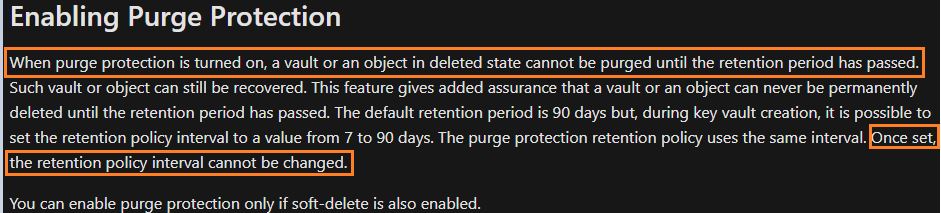
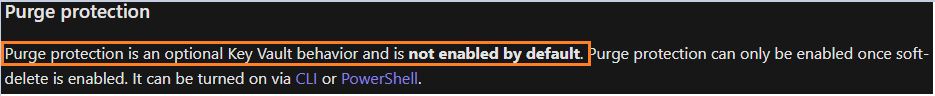
"Purge protection once enabled cannot be disabled. This is by design. There is no plan to offer a way to disable purge protection once enabled. We are considering some other options in future for customers to be able to use SSE without turning on purge protection."
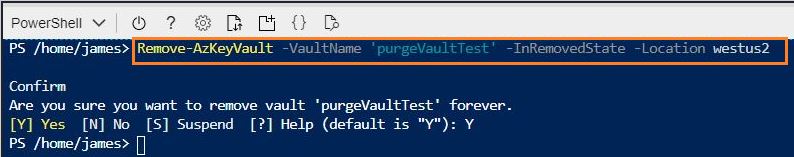
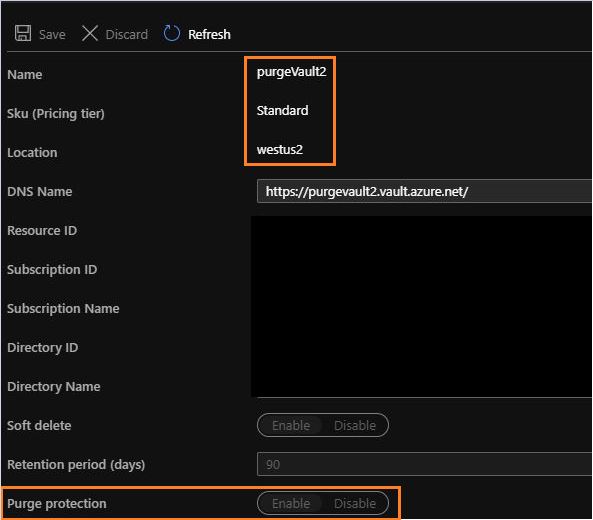
Since this issue is by design, I have updated our CLI/PS docs for enabling purge protection to reflect that "disabling purge protection isn't supported". Corresponding GitHub issues follow.
Enable Purge Protection PS:
#58744
Enabling Purge Protection CLI:
#58742
Please allow some time for the changes to reflect and if you don't see the document update, please let me know.