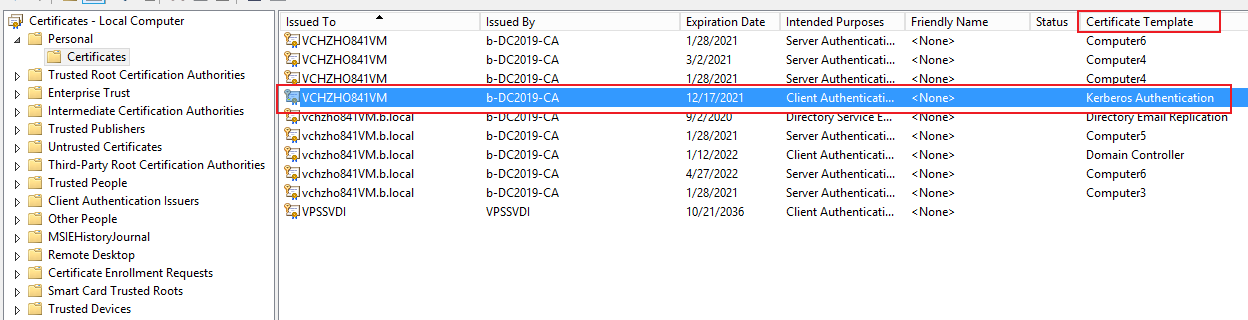
I have spent many months on this issue, but recently on a new Windows Server 2019, I have the same issue:
I would think that the internal Windows 2019 certificates would be fine for LDAPS, not sure if it is a matter of trust, or a configuration issue. I have looked at many documents on the internet, but none seem to help me get beyon this LDAPS issue. My goal is to use a Windows 2019 ldaps certificate so other applications can authenticate and retrieve ldap data.
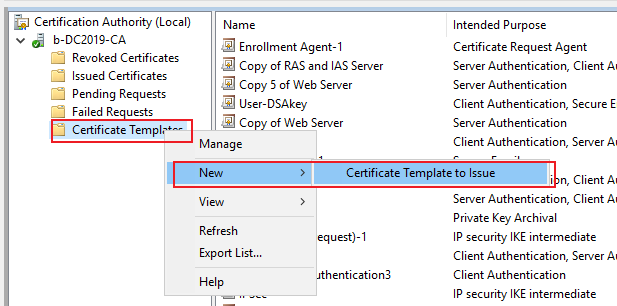
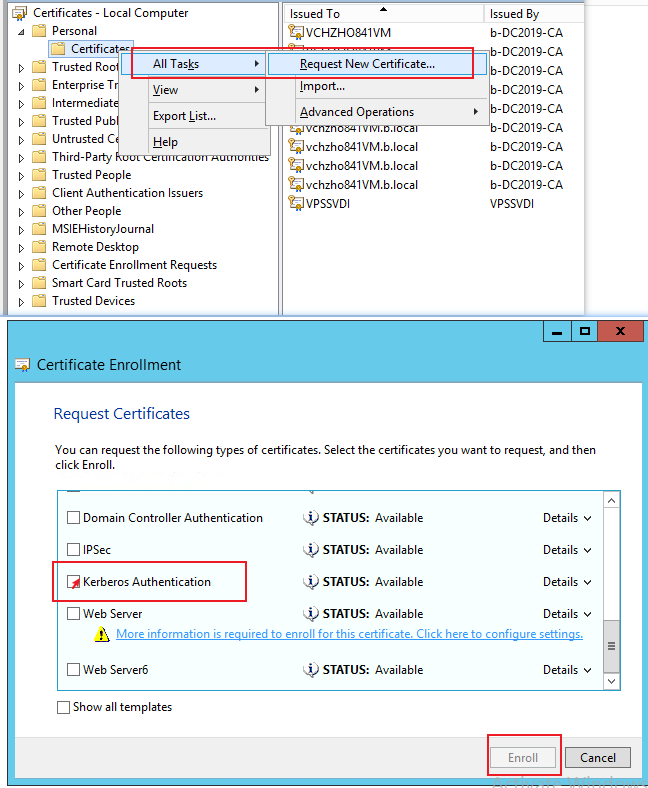
I have installed Windows Server 2019 and I installed the Certification Authority and I see port 389 and 636 in a listen mode, but when I attempt to use port 636 I have errors. Port 389 is fine. When I use the openssl connect command on port 443 I have no errors.
What I have tried.
I have spent hours searching for solution that work in www.google.com. This has not worked.
I have used a JXplorer ldap browser i can login to port 389 and see active directory objects fine, but when I use port 636 it fails immediately with the error "Error opening connection: LDAP connection has been closed". The details on the error are: javax.naming.NamingException: LDAP connect has been closed".
When I do this command, I get a response as shown below that :
openssl s_client -connect FicticiousServerName.com:636 -showcerts
CONNECTED(00000003) depth=0 CN = LAB.FicticiousServerName.com verify error:num=20:unable to get local issuer certificate verify return:1 depth=0 CN = LAB.FicticiousServerName.com verify error:num=21:unable to verify the first certificate verify return:1
Certificate chain 0 s:/CN=LAB.FicticiousServerName.com i:/DC=com/DC=FicticiousServerName/CN=FicticiousServerName.com
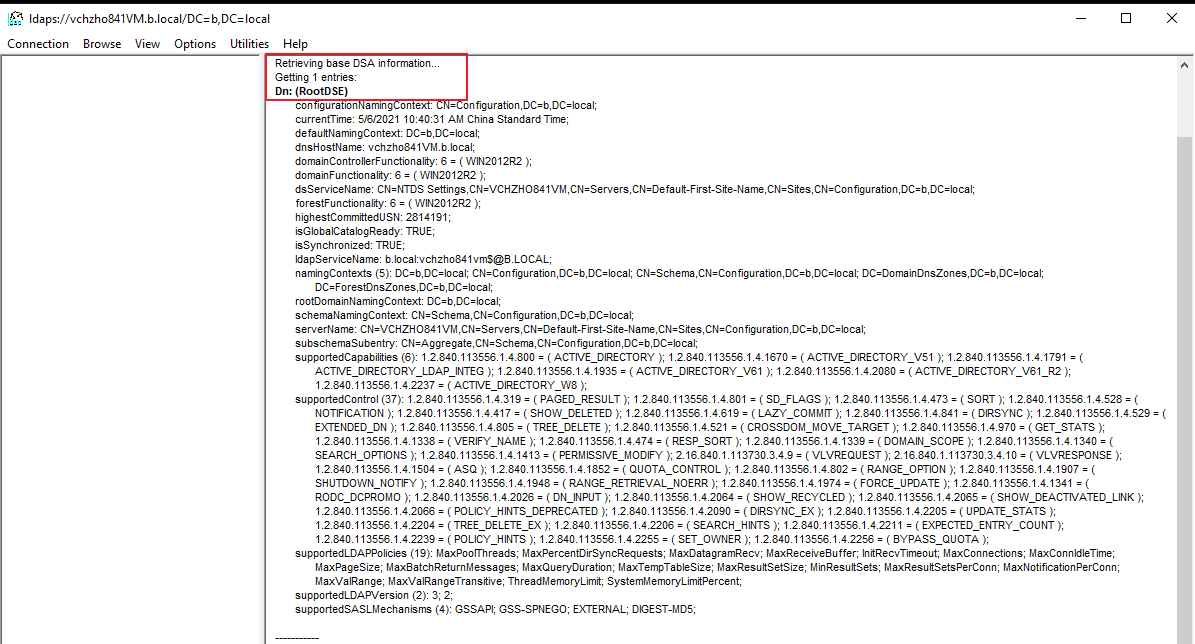
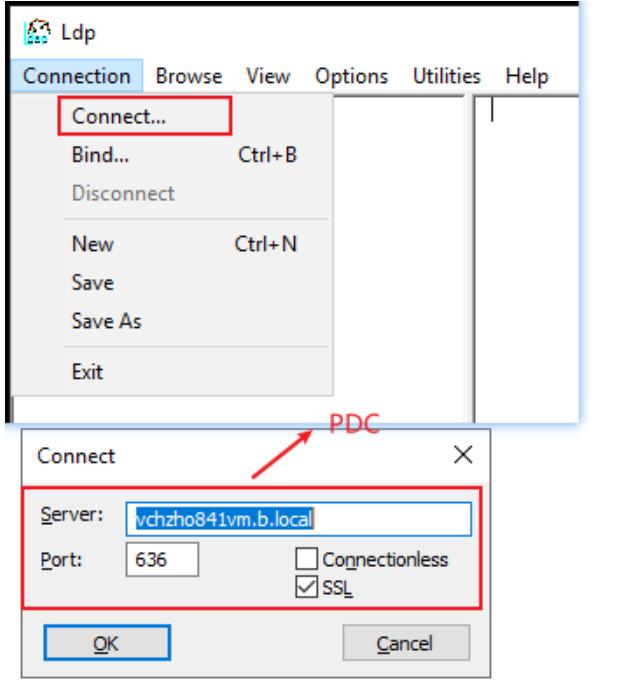
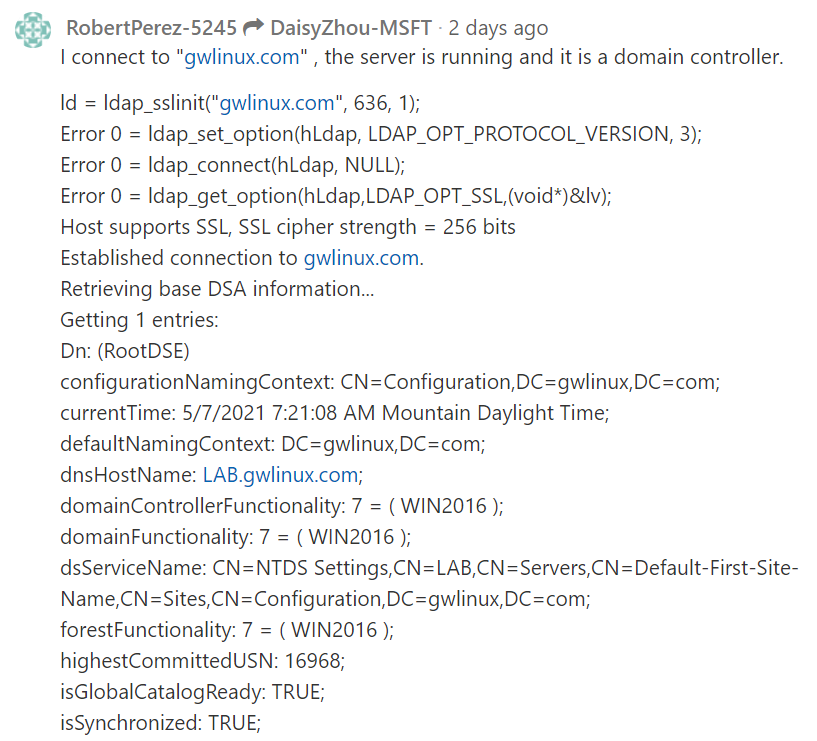
Use Windows 2019 ldp.exe to test ldap and port 636, IT LOOKS FINE.... :
How can I use the existing ldap certificate in Windows 2019 and not get errors when
doing :
openssl s_client -connect FicticiousServerName.com:636 -showcerts