Thanks for using Microsoft Q&A !!
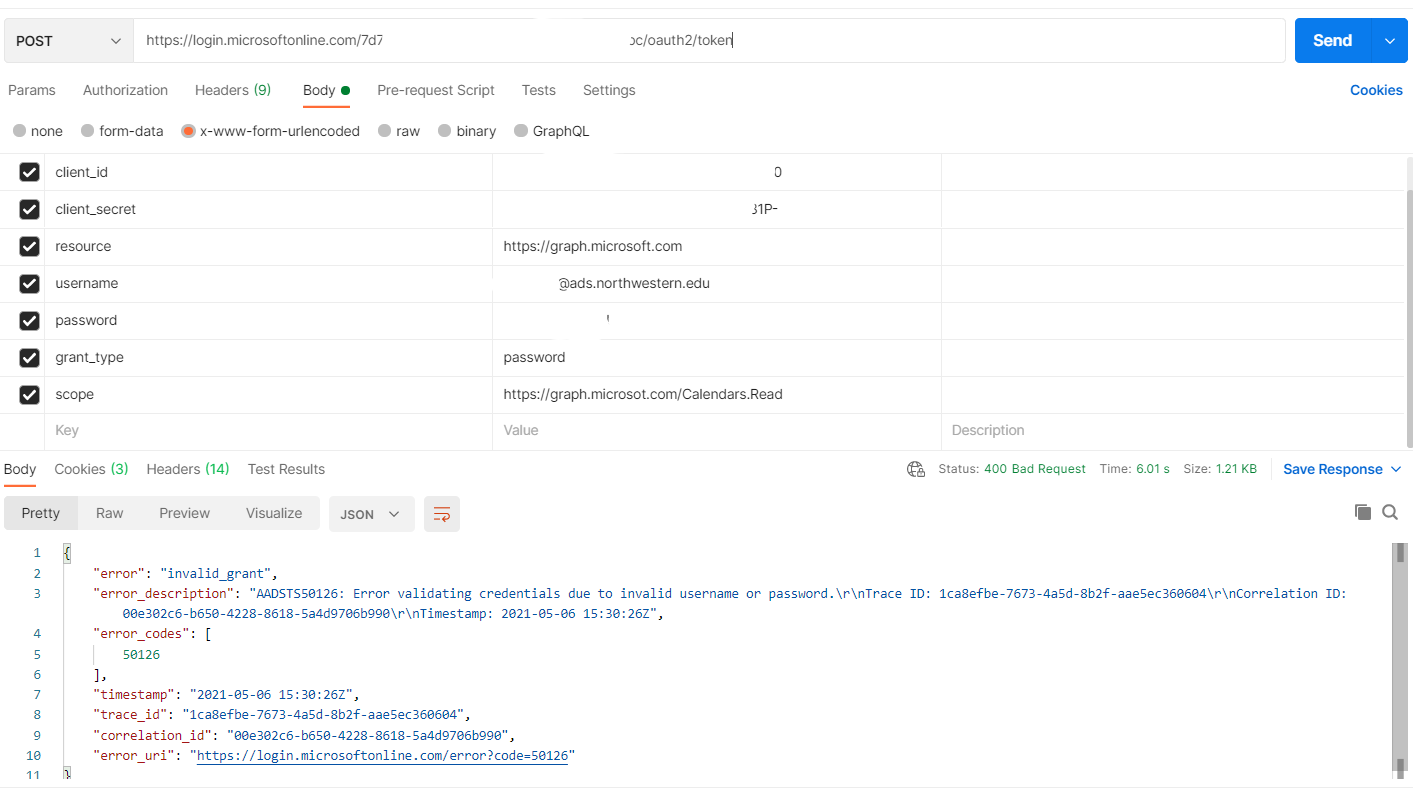
You are getting this error as ROPC is not supported in hybrid identity federation environment with the exception of PTA as Azure AD is not able to test the user name and password against the identity provider. So, when you re making api call from postman ( as it can't do the redirection) credentials can't verified and you get this error. Please refer to these threads -
- Error validating credentials due to invalid username or password
- invalid_grant: AADSTS50126: Error validating credentials due to invalid username or password
Thanks
Saurabh