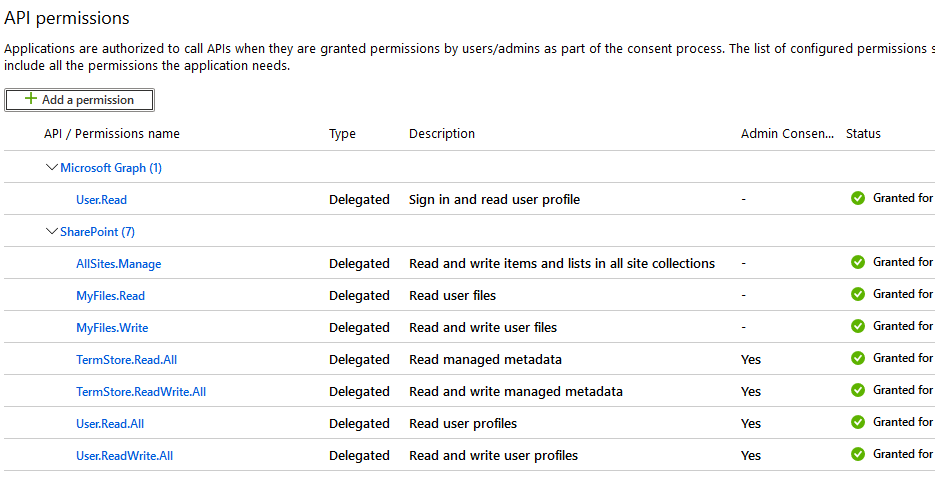
I'm following up on this. We will need some more information in regards to this, can you please provide the information that Shashi was requesting? If you can get a fiddler trace and provide the error response that would be much more beneficial. Are you sure that the token has the right permissions/scps?
You can decode your JWT Tokens here : https://jwt.ms/
The Claims tab will also provide an explanation of what the claims in your JWT token are supposed to do.
Also, it's suggested to utilize the microsoft graph api when possible. The sharepoint rest api should be available on the msft graph API: https://learn.microsoft.com/en-us/graph/api/resources/sharepoint?view=graph-rest-1.0
The Azure Q&A Forums do not support Sharepoint as they are still on the MSDN Forums. These forums can be found here :
https://social.msdn.microsoft.com/Forums/en-US/home?category=openspecifications
Protocol Reference can be found here:
https://learn.microsoft.com/en-us/openspecs/sharepoint_protocols/ms-spprotlp/8a50af28-2b50-43d8-9c5a-3e520255ef7e
Specifically for OAuth2 and Sharepoint Servers, you can find the technical docs on implementation here : https://learn.microsoft.com/en-us/openspecs/sharepoint_protocols/ms-sps2sauth/f80a09df-8e0e-434f-93bd-a348d52a8022
Accessing the Sharepoint Server API call you are referring to is going to be dependent on the Sharepoint Server's OAuth Authentication. The technical doc provided above is a part of the same doc repo as the getCurrentUserInfo API call as it's a part of the openspec, so I would suggest making sure that your implementation follows the technical doc.
GetCurrentUserInfo reference : https://learn.microsoft.com/en-us/openspecs/sharepoint_protocols/ms-asws/d8bf93a5-69b4-4d3c-9154-d5bc1eaa542f