Hi @Peter Behrik ,
Could you share more information about this message with us? Such as "Times and time frame of the suspicious activities.", "Severity of the suspicious activity, High, Medium, or Low.",etc.
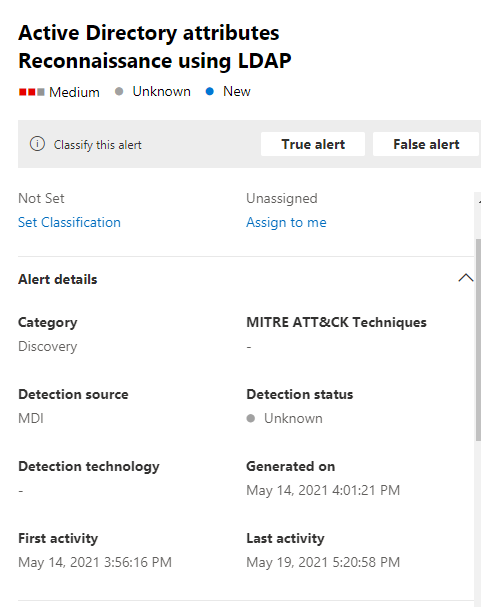
This message shows that it is searching for objects of "PasswordNotRequired" in the Domain. Based on this message alone, we cannot determine who sent the query request. All mailboxes created in Exchange have passwords.
In order to prevent other objects from receiving threats, you could run the following command line in the powershell of the DC server to check that the "PasswordNotRequired" of those objects is set to "True". If it is an important object, please run the second command line below to set it to "False".
Get-ADUser -Filter {PasswordNotRequired -eq $true}
Set-ADUser -Indetity "" -PasswordNotRequired $false
In addition, have you run the LDAP scanning tool?
Please refer to: Active Directory attributes reconnaissance (LDAP) (external ID 2210)
----------
If the response is helpful, please click "Accept Answer" and upvote it.
Note: Please follow the steps in our documentation to enable e-mail notifications if you want to receive the related email notification for this thread.