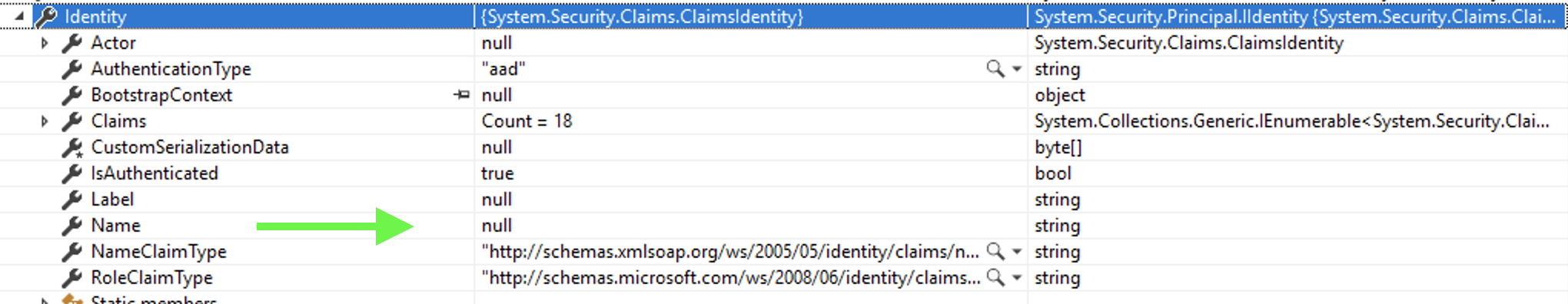
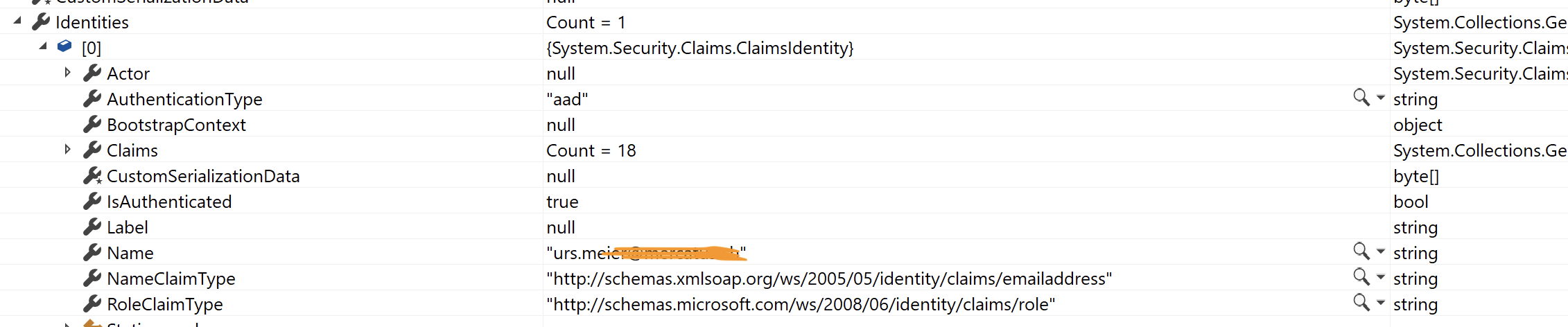
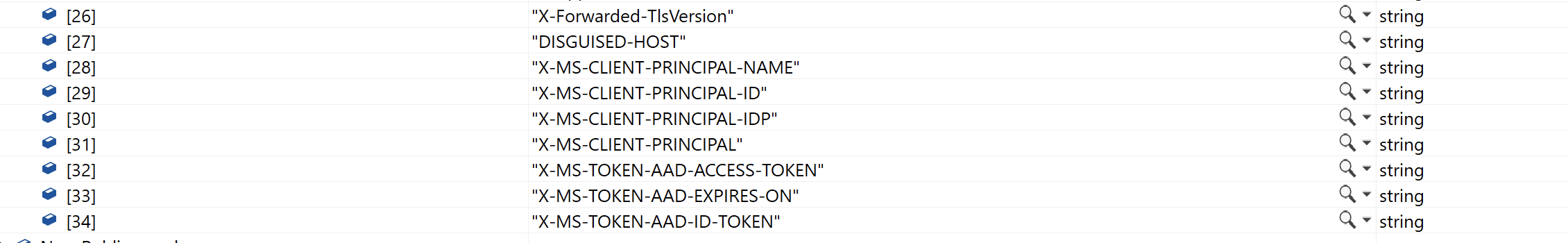
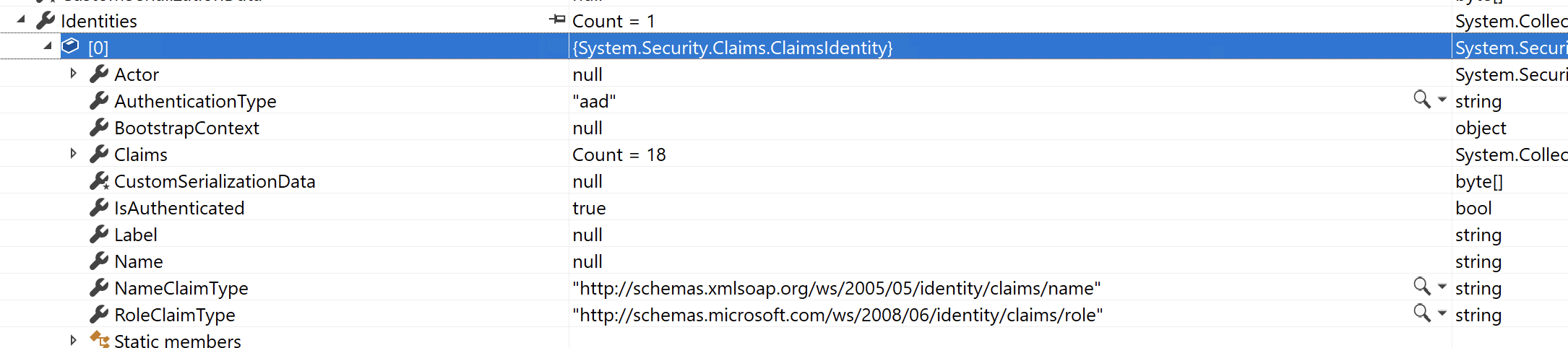
@Urs Meier The Client Identity is available when using App Service Authentication / Authorization which are driven by special headers injected by App Service. You can leverage the same by implementing the Authentication Flow described in the docs.
For direct OAuth/OpenID Connect, usually all claims are present in the JWT which you would verify and extract from. If this is what you are looking for, instead of App Service Authentication, you could use Azure APIM in front of your function apps and setup pre-validation of tokens. With this, you could simply use MSAL.js to fetch the token and pass in the Authorization header.