@Will Hasey Apologies for the delay response!
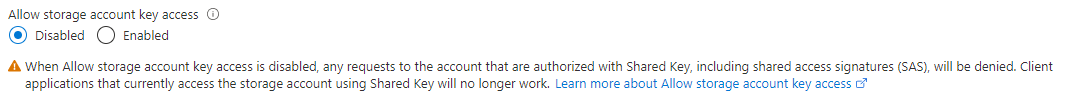
Note: If you disable account access keys, you will not be able to access Azure Files or Table storage as they do not support (yet?) Azure AD authentication.
Azure Storage supports Azure AD authorization for requests to Blob and Queue storage only. **
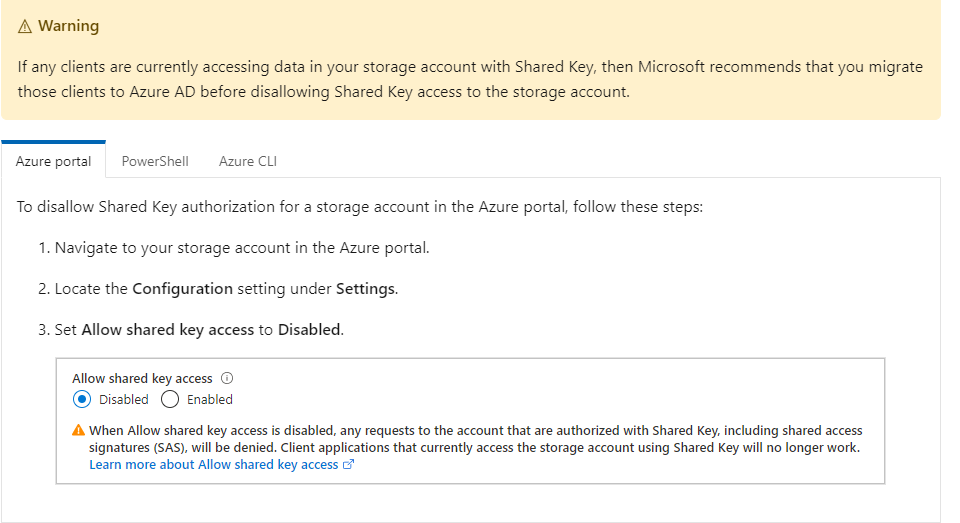
If you disallow authorization with Shared Key for a storage account, requests to Azure Files or Table storage that use Shared Key authorization will fail.
** Because the Azure portal always uses Shared Key authorization to access file and table data, if you disallow authorization with Shared Key for the storage account, you will not be able to access file or table data in the Azure portal.
Microsoft recommends that you either migrate any Azure Files or Table storage data to a separate storage account before you disallow access to the account via Shared Key, or that you do not apply this setting to storage accounts that support Azure Files or Table storage workloads.
Disallowing Shared Key access for a storage account does not affect SMB connections to Azure Files.
If you are looking for this specific feature, you can leave your feedback here, Please take a few minutes to submit your idea in the one of the forums available on the right or vote up an idea submitted by another Azure customer. All of the feedback you share in these forums will be monitored and reviewed by the Microsoft engineering teams responsible for building Azure.
Kindly let us know if the above helps or you need further assistance on this issue.
----------------------------------------------------------------------------------------------------------------------------------------
Please do not forget to "Accept the answer” and “up-vote” wherever the information provided helps you, this can be beneficial to other community members. and “up-vote” wherever the information provided helps you, this can be beneficial to other community members.


 ]
]
 We strongly recommend you to review the
We strongly recommend you to review the