@vijje-3055 Here are the steps on how to achieve deny assignment using Azure Blueprints. To show deny assignment being added to Azure Blueprints, I will use existing built-in policy as an example.
A. Select All services in the left pane. Search for and select Blueprints.
B. Select Blueprint definitions from the page on the left and select the + Create blueprint button at the top of the page.
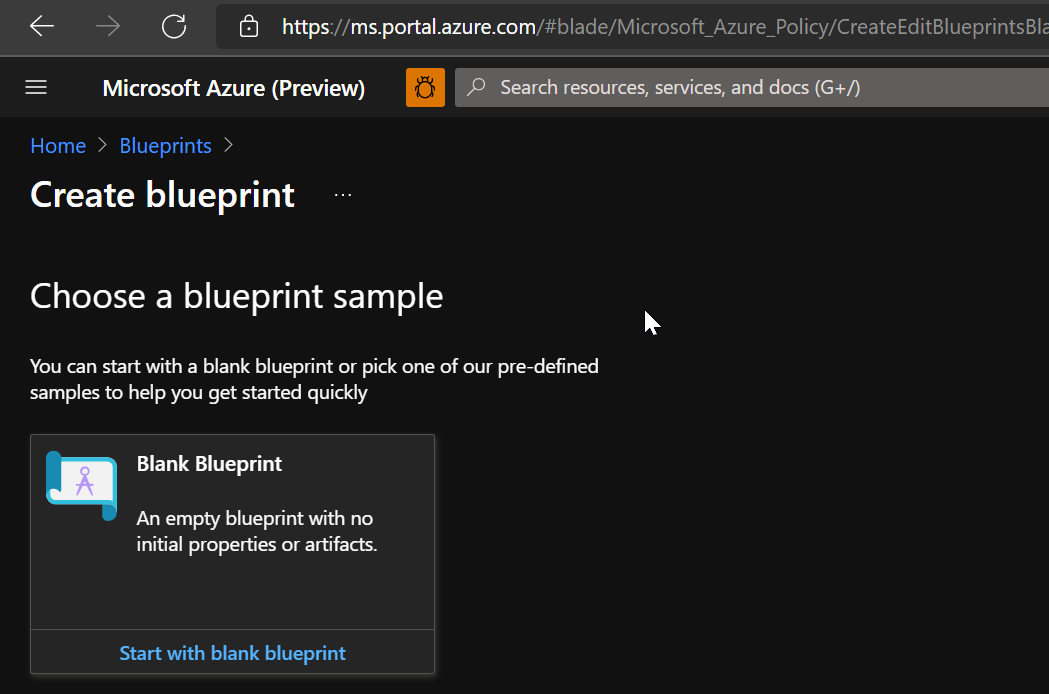
C. Select Start with blank blueprint from the card at the top of the built-in blueprints list.
D. Provide a Blueprint name such as testblueprint. (Use up to 48 letters and numbers, but no spaces or special characters).
In the Definition location box, select the ellipsis on the right, select the management group or subscription where you want to save the blueprint, and choose Select.
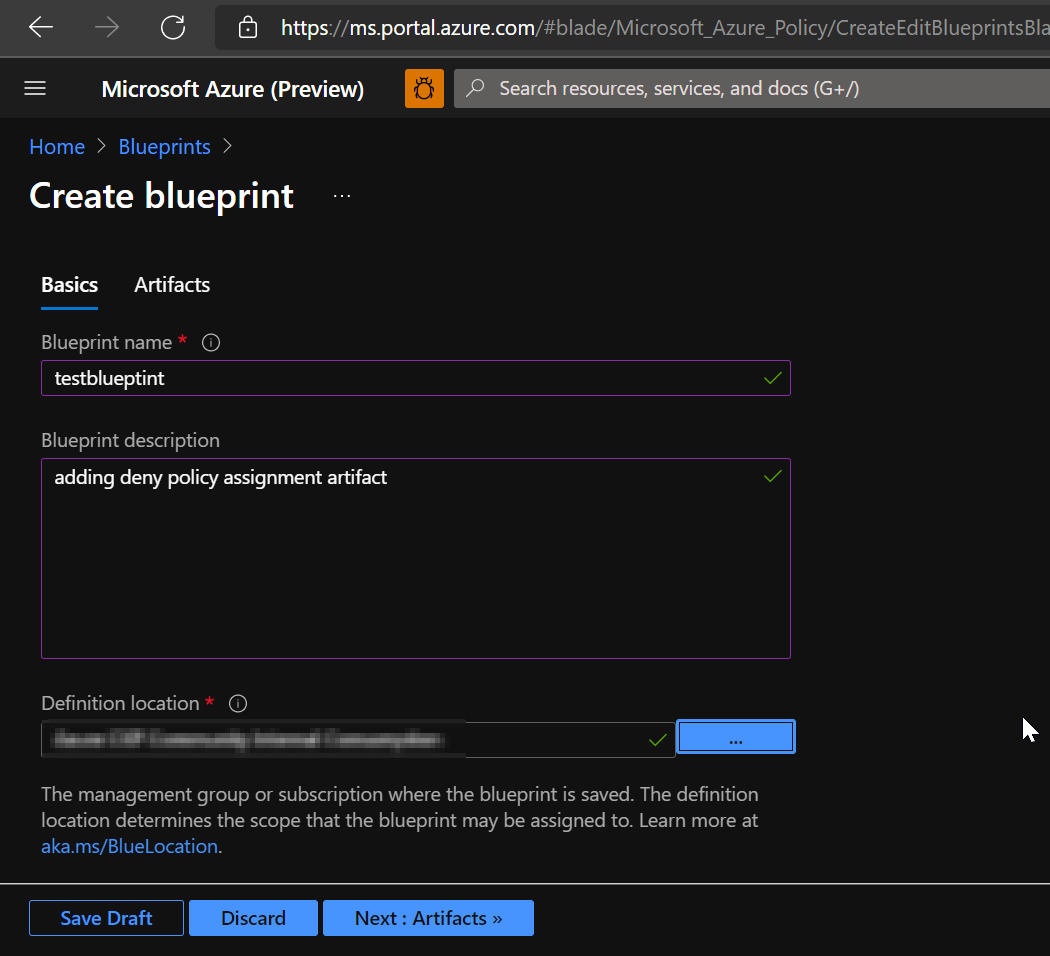
E. To add a policy assignment at the subscription level:
- Select the + Add artifact row under the role assignment artifact.
- Select Policy assignment for Artifact type.
- Change Type to Built-in. In Search, enter Automation Account .
- Change focus out of Search for the filtering to occur. Select Automation Account variables should be encrypted.
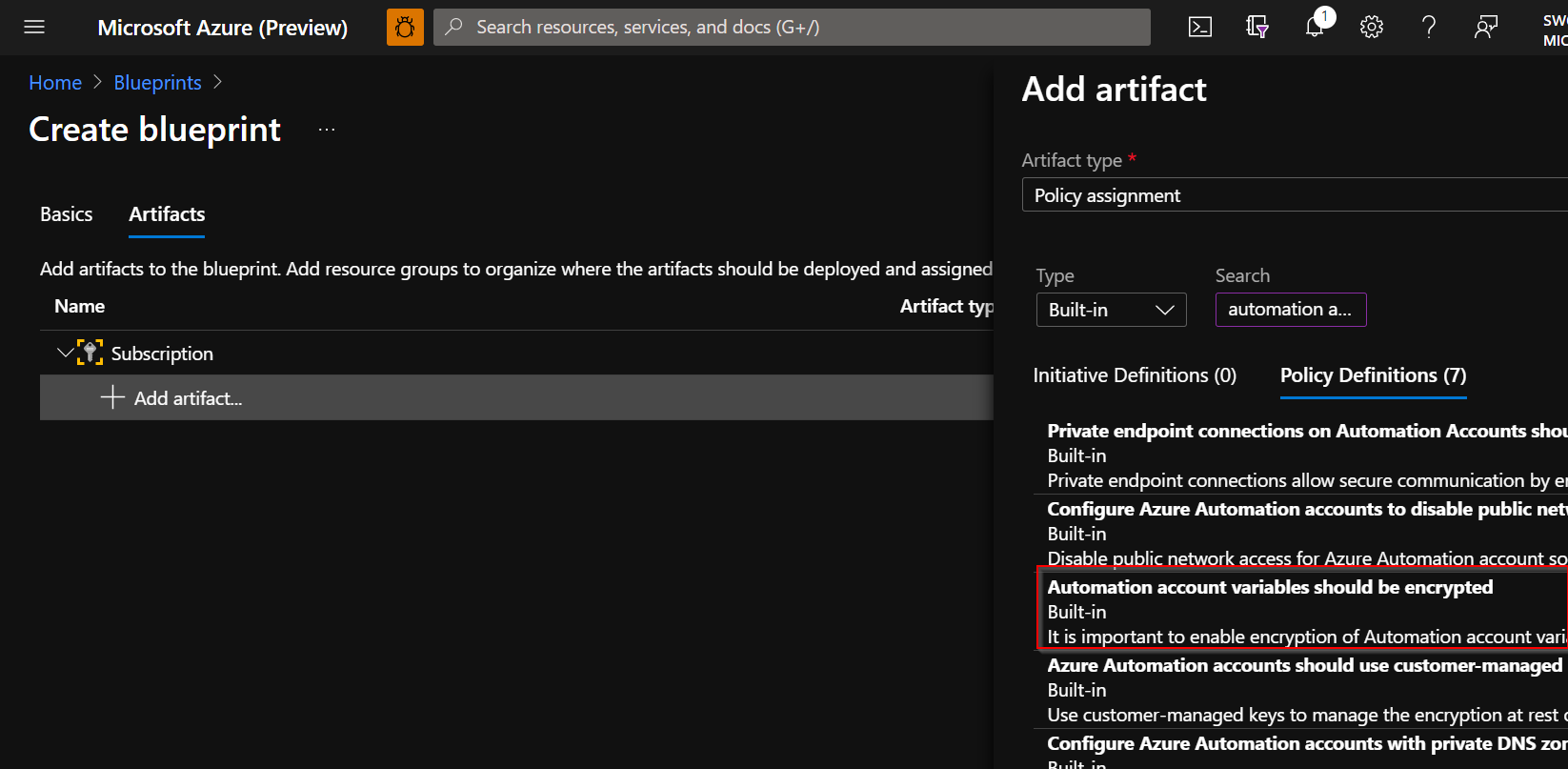
Select Add to add this artifact to the blueprint.
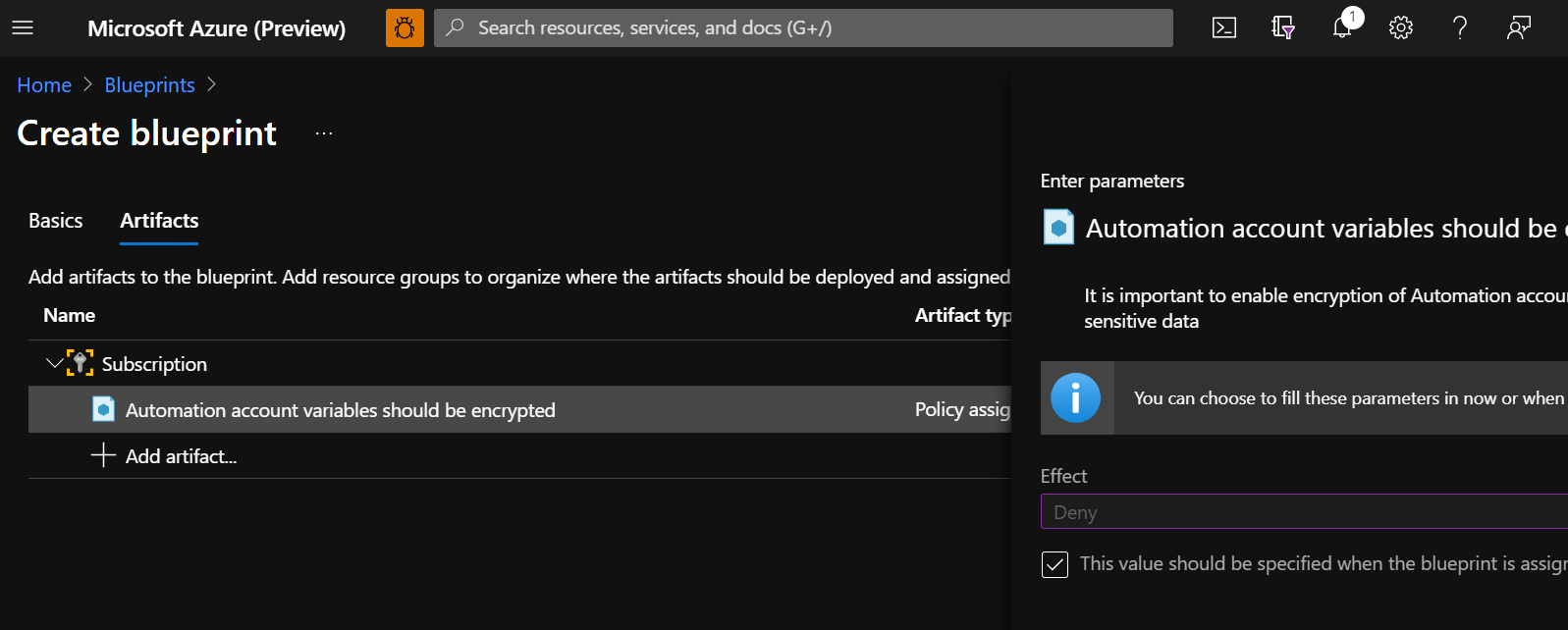
F. Select the artifact and uncheck the "This value should be specified when the blueprint is assigned". Then Change the effect to "Deny"
G. Click on Save Draft.
Note : To disable inheritance, it can be done by following this document or this document.