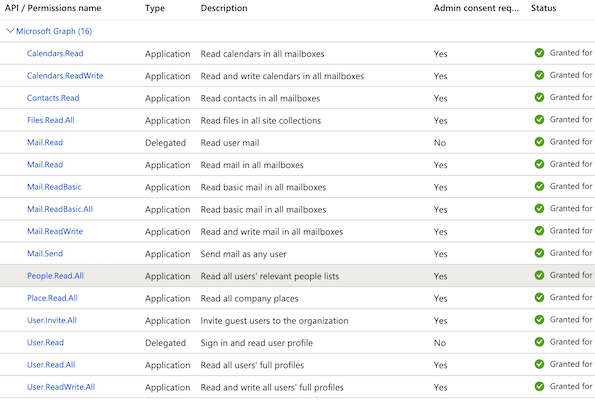
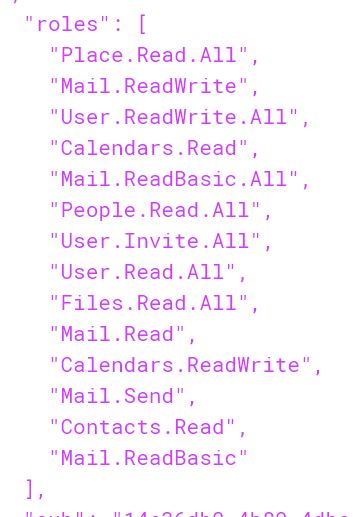
From what I see, The first screenshot you shared shows a token which has roles(application permissions) while the token request attached shows scp( delegated permissions). Since you are trying to call GET /users/{id | userPrincipalName}/events, I suppose you are trying to access Graph using Application permissions.
To get this to work I suggest you review between delegated permissions vs applications permissions auth code flow vs client credential flow which one works best for you and reconfigure. You are better off with application permissions using client credential flow. Here is a sample request of how to get the access token using this flow. Ensure the application has these permissions added and approved by admin.
curl --location --request GET 'https://login.microsoftonline.com/tenant-id/oauth2/v2.0/token' \
--header 'Content-Type: application/x-www-form-urlencoded' \
--data-urlencode 'grant_type=client_credentials' \
--data-urlencode 'client_id=your-client-id' \
--data-urlencode 'scope=https://graph.microsoft.com/.default' \
--data-urlencode 'client_secret=client-secret'
Note that I am not calling https://login.microsoftonline.com/common/oauth2/v2.0/token which also commonly causes this issue.
On the other hand if you are trying to get access token using auth code flow like you share using
https://login.microsoftonline.com/a1cd3436-6062-4169-a1bd-79efdcfd8a5e/oauth2/v2.0/authorize?
response_type=code
&client_id=403a1dca-c4f5-4296-99da-25d7094096df
&redirect_uri=https%3A%2F%2Fkaseya--crmitdev.my.salesforce.com%2Fservices%2Fauthcallback%2FMaxNetOutlook
&scope=User.Read+User.Read.All+User.ReadWrite.All+User.Invite.All+Calendars.Read+Calendars.ReadWrite+openid+email+profile+offline_access+Calendars.Read.Shared+Calendars.ReadWrite.Shared+Place.Read.All
&state=CAAAAXmin1VNMDAwMDAwMDAwMDAwMDAwAAAA5jd50IUCTDJcEWVXWtwKRbfVSbh
&sso_reload=true
Note that you can not use the token from above to call GET /users/{id | userPrincipalName}/events when the id | userPrincipalName is not the user who consented.
That said, I think you have the scopes and flows mixed up and would be better using client credential flow as suggested above if you don't need use consent. If you need user consent you will only call the API for resources for the user that has consented.
Incase you need more help, feel free to comment on this answer and if this answer is helpful, consider accepting and upvoting to get better help other users.
 .
.