ZhengqiLou-MSFT,
Thank you for your reply/input. Here are the answers to your questions (hope they help).
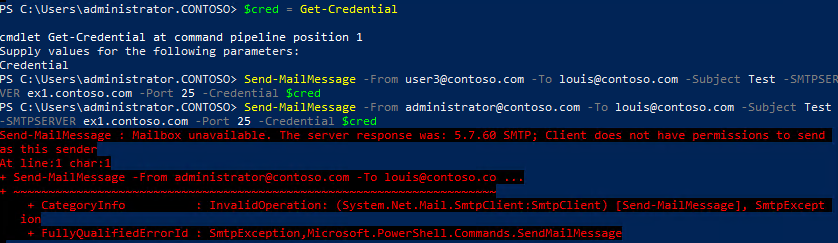
- We receive the 5.7.60 error when I or the Users launch Powershell under their Windows profile and run the Send-MailMessage commands from above. This was done mainly to try and test an Authenticated relay in PowerShell first to make sure the default Receive Connectors (RC) that leverage ports 587, 465, and 2525 worked as expected. Technically the PowerShell commands work great as long as you are an Exchange Organization Administrator. I tested and validated that as Org Admin - zero issues in PS. When I removed Org Admin the 5.7.60 error comes up 100% of the time.
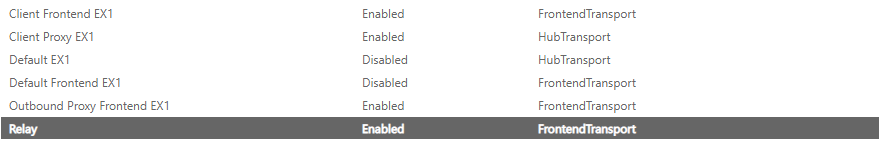
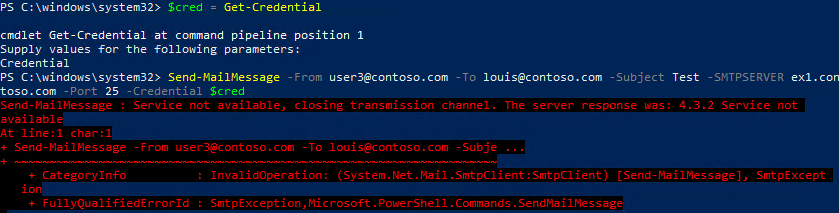
- The second test was done when we created the new Receive Connector (using the settings above) and chose port 25 (not default RCs configured for 587, 465,. & 2525) for the authenticated requests (provided we add the IP, Range, or Network). The results of this second test are the same as the first where we receive the 5.7.60 error.
Note: Both of the above tests were performed with PowerShell.
The main goal is to leverage a default connector that uses ports 465, 587, or 2525 OR the new Receive Connector configured with port 25 to allow an app/software to leverage authenticated mail relay for our Users. From within the app/software we plugged in the user credentials and did receive some additional errors (shown below).
Port 587 yielded the following error:
Source: Send SMTP Mail Message
Message: No compatible authentication mechanisms found
Exception Type: System.NotSupportedException
Thoughts: The Client Frontend SERVERNAME has TLS, Basic authentication (with offer basic only after starting TLS), and Integrated Windows. Is Enable domain security (mutual Auth TLS, Exchange Server authentication required?
Port 465 yielded the following error:
Message: An error occurred while attempting to establish an SSL or TLS connection
Several references to server is not trusted, local system missing root or intermediate cert, and expired/invalid cert
Thoughts:
The Exchange certificate we have for EWS services is trusted by the client (OWA validates that the certificate is good and that the client does trust it). This leaves the only other possibility as i see it meaning that the Exchange certificate is NOT associated to the Client Proxy SERVERNAME Receive Connector. To validate it is not I ran the following command.
Get-ReceiveConnector "SERVERNAME\Client Proxy SERVERNAME" | fl cert
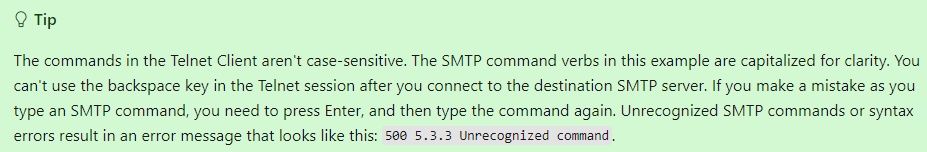
My preference would be to leverage one of the default Receive Connectors if possible, but would rather not modify them. If modifying them whether that be adding another authentication radio box or certificate to the connector then its preferred to use the new connector created specifically for authenticated relay, but the new connector using port 25 is not working. When I telnet using the following command I get the error below when I ehlo.
Command:
telnet mail.domain.com 25
Error:
500 5.3.3 Unrecognized command 'XXXX'
Which is what I am trying to figure out now. My IP has been added to the scope of this connector and all radio boxes are checked for authentication except for Exchange Servers and External.
Thanks,
CWT