
Hello @Roger Roger ,
Thank you for posting here.
Q: how can i know who has modified it and when was it modified.
A: If you enable audit policy before the account was changed, you can check security log on the DC.
Here is my test in my lab.
1.Enable audit account management policy, in my case, I edit the gpo settings in Default Domain Policy.
Computer Configuration\Windows settings\security settings\local policies\audit policy
Audit Account Management – Success and Failure
Or use advanced audit policies (advanced audit policies will overwrite all legacy audit policies by default):
Computer Configuration\Windows settings\security settings\Advanced Audit Policy Configuration
Account Management
Audit User Account Management – Success and Failure
Note:
If you have never configured any advanced audit policy before, then you can configure the legacy audit policy.
If you have configured any one advanced audit policy before, then you should configure the advanced audit policy.
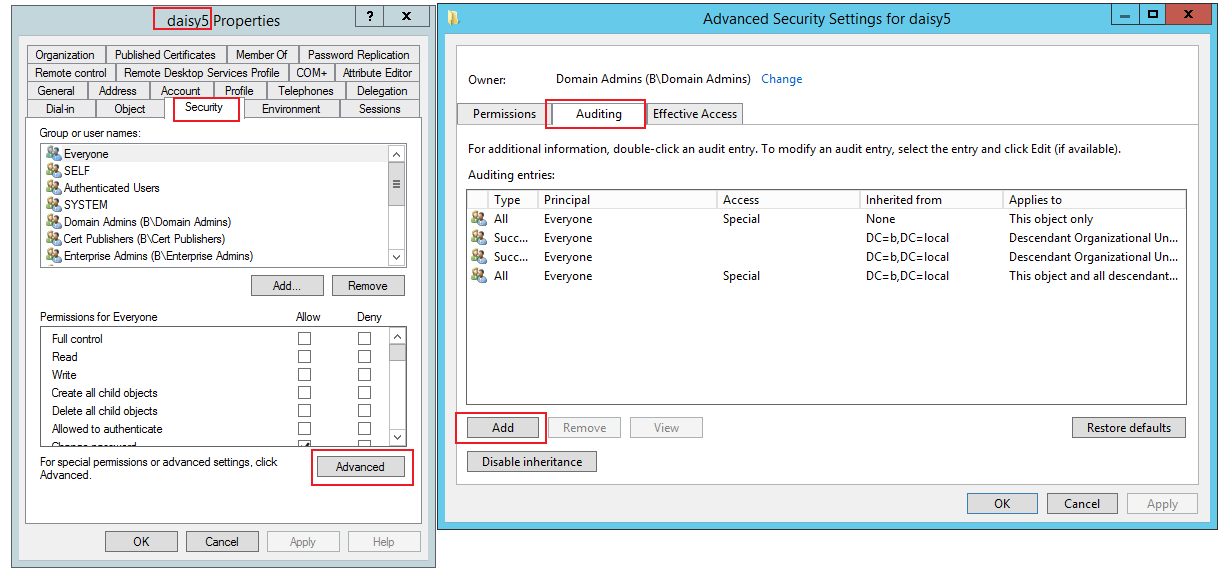
2.Enable auditing settings on one domain account or the parent container.
In my case, I enable auditing settings on one domain account (daisy5).
Principal: Everyone
Tyle: All
Applies to: This object only (Note: if you set it on an OU with many users, please select All descendant objects)
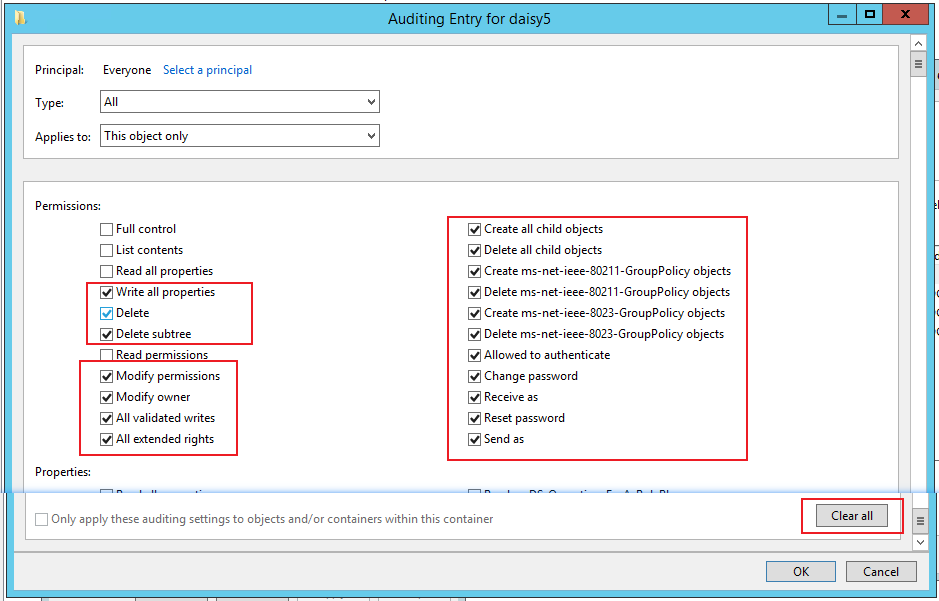
Click Clear all button and click all the following properties.
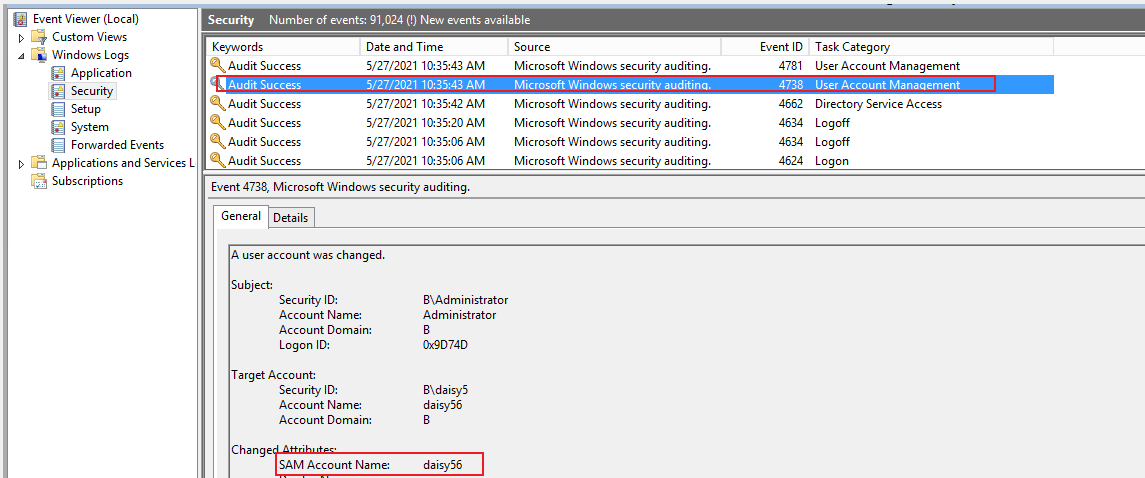
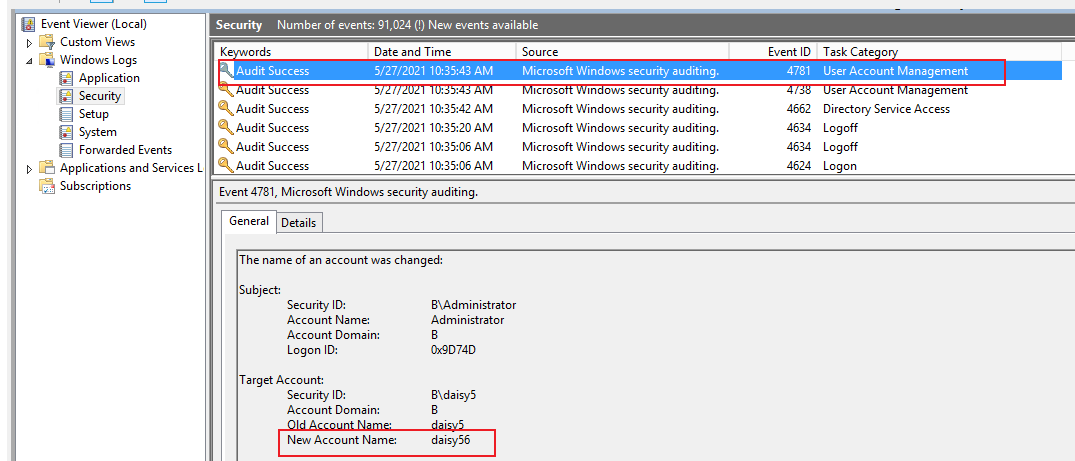
3.If I change samaccount name of daisy5 from daisy5 to daisy56, I can see event ID 4781 and 4738.
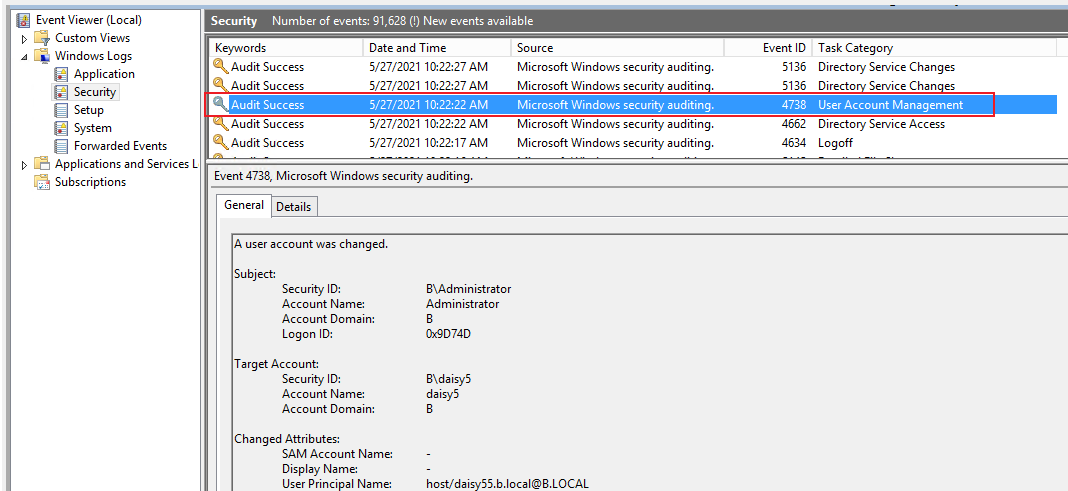
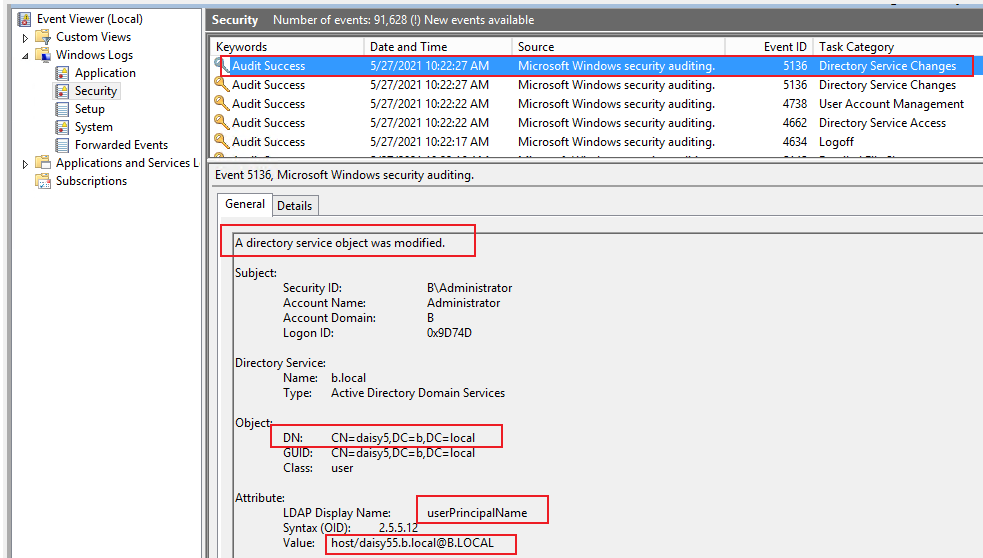
4.If I change UPN of daisy5 from host/daisy5.b.local@B.LOCAL to host/daisy55.b.local@B.LOCAL, I can see event ID 4738 and 5136.
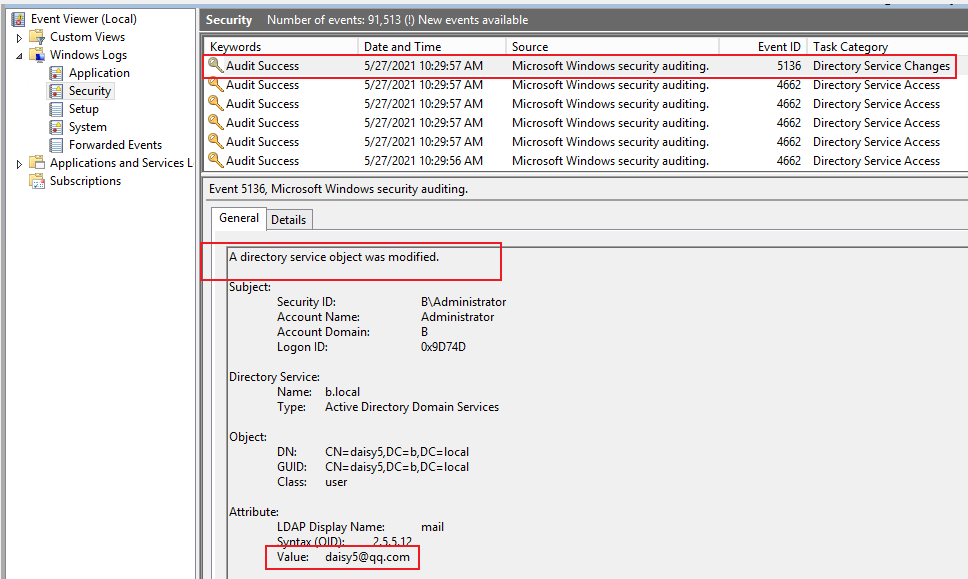
5.If I change email address of daisy5 from blank to ******@qq.com, I can see event ID 5136.
Hope the information above is helpful.
Should you have any question or concern, please feel free to let us know.
Best Regards,
Daisy Zhou
============================================
If the Answer is helpful, please click "Accept Answer" and upvote it.