Hello Randal,
The software which implements this platform seems to have many weaknesses; it seems that if you leave a message open too long in a browser window, a session times out and many buttons (Preview, Post, etc.) become ineffective - this may explain your difficulties (refreshing the page helps).
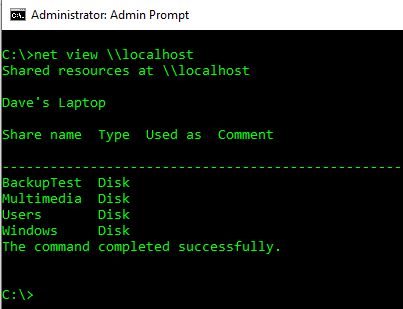
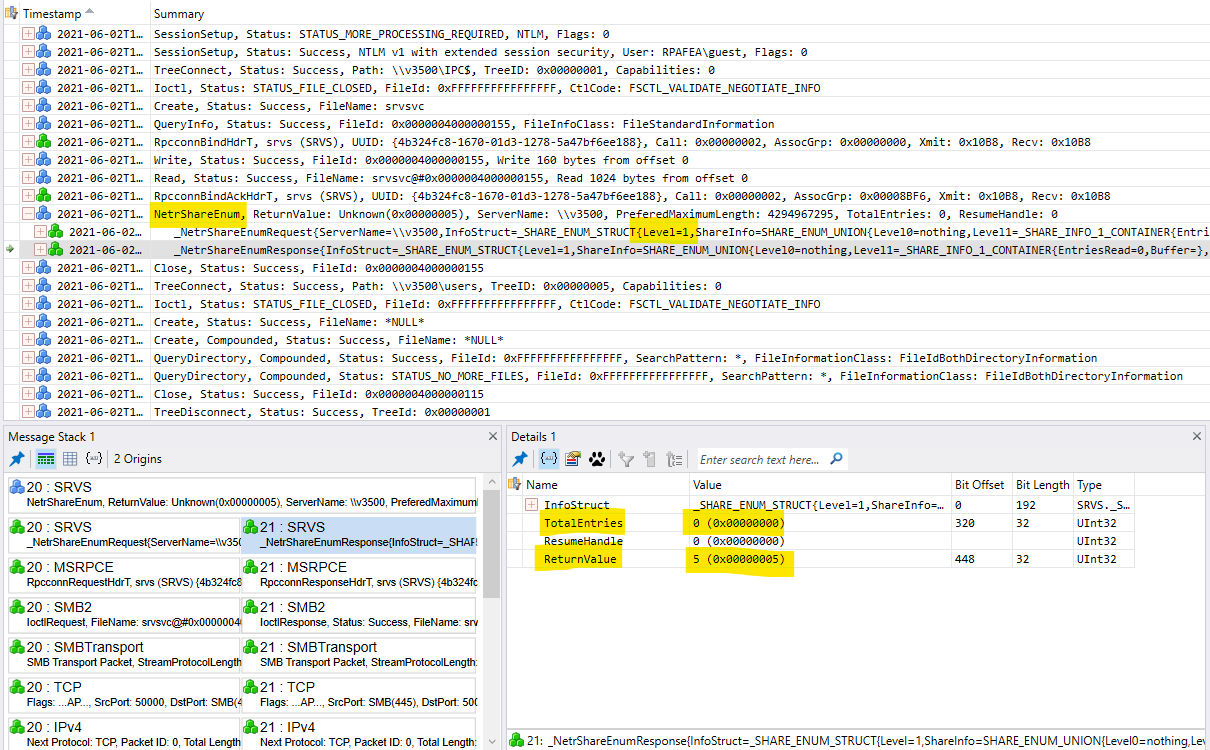
This problem is turning out to be a real mystery. To get a feel for how things should work, I traced what happens on my (Windows 10) "server" when responding to a "net view" (NetShareEnum) request. The best ETW trace that I got was:
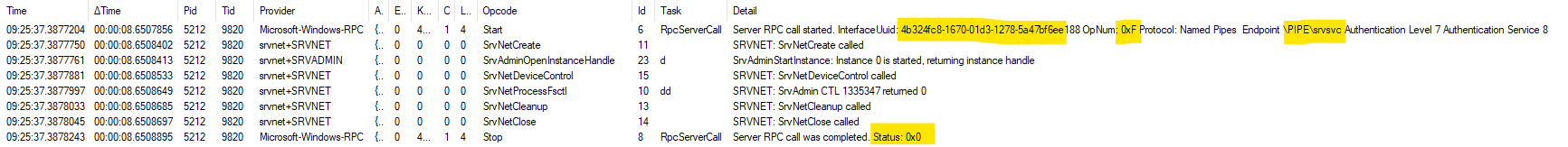
This shows the RPC for NetShareEnum (RPC OpNum = 15 (0xF)) to interface srvsvc (4B324FC8-1670-01D3-1278-5A47BF6EE188) arriving and some processing taking place in srvnet.sys.
I checked the srvnet.sys routines and there is no access checking there. The only access checking takes place in the LanmanServer service process, in routine srvsvc!NetrShareEnum. Based on the "level" of the NetShareEnum request, it checks the desired access against this ACL:
0:000> !acl poi(srvsvc!SsSharePrintSecurityObject+10)+14 1
ACL is:
ACL is: ->AclRevision: 0x2
ACL is: ->Sbz1 : 0x0
ACL is: ->AclSize : 0xe0
ACL is: ->AceCount : 0xa
ACL is: ->Sbz2 : 0x0
ACL is: ->Ace[0]: ->AceType: ACCESS_ALLOWED_ACE_TYPE
ACL is: ->Ace[0]: ->AceFlags: 0x0
ACL is: ->Ace[0]: ->AceSize: 0x18
ACL is: ->Ace[0]: ->Mask : 0x000f0013
ACL is: ->Ace[0]: ->SID: S-1-5-32-544 (Alias: BUILTIN\Administrators)
ACL is: ->Ace[1]: ->AceType: ACCESS_ALLOWED_ACE_TYPE
ACL is: ->Ace[1]: ->AceFlags: 0x0
ACL is: ->Ace[1]: ->AceSize: 0x18
ACL is: ->Ace[1]: ->Mask : 0x000f0013
ACL is: ->Ace[1]: ->SID: S-1-5-32-549 (no name mapped)
ACL is: ->Ace[2]: ->AceType: ACCESS_ALLOWED_ACE_TYPE
ACL is: ->Ace[2]: ->AceFlags: 0x0
ACL is: ->Ace[2]: ->AceSize: 0x18
ACL is: ->Ace[2]: ->Mask : 0x000f0013
ACL is: ->Ace[2]: ->SID: S-1-5-32-550 (no name mapped)
ACL is: ->Ace[3]: ->AceType: ACCESS_ALLOWED_ACE_TYPE
ACL is: ->Ace[3]: ->AceFlags: 0x0
ACL is: ->Ace[3]: ->AceSize: 0x18
ACL is: ->Ace[3]: ->Mask : 0x000f0013
ACL is: ->Ace[3]: ->SID: S-1-5-32-547 (Alias: BUILTIN\Power Users)
ACL is: ->Ace[4]: ->AceType: ACCESS_ALLOWED_ACE_TYPE
ACL is: ->Ace[4]: ->AceFlags: 0x0
ACL is: ->Ace[4]: ->AceSize: 0x14
ACL is: ->Ace[4]: ->Mask : 0x00000001
ACL is: ->Ace[4]: ->SID: S-1-1-0 (Well Known Group: localhost\Everyone)
ACL is: ->Ace[5]: ->AceType: ACCESS_ALLOWED_ACE_TYPE
ACL is: ->Ace[5]: ->AceFlags: 0x0
ACL is: ->Ace[5]: ->AceSize: 0x14
ACL is: ->Ace[5]: ->Mask : 0x00000001
ACL is: ->Ace[5]: ->SID: S-1-5-7 (Well Known Group: NT AUTHORITY\ANONYMOUS LOGON)
ACL is: ->Ace[6]: ->AceType: ACCESS_ALLOWED_ACE_TYPE
ACL is: ->Ace[6]: ->AceFlags: 0x0
ACL is: ->Ace[6]: ->AceSize: 0x14
ACL is: ->Ace[6]: ->Mask : 0x00000002
ACL is: ->Ace[6]: ->SID: S-1-5-20 (Well Known Group: NT AUTHORITY\NETWORK SERVICE)
ACL is: ->Ace[7]: ->AceType: ACCESS_ALLOWED_ACE_TYPE
ACL is: ->Ace[7]: ->AceFlags: 0x0
ACL is: ->Ace[7]: ->AceSize: 0x14
ACL is: ->Ace[7]: ->Mask : 0x00000002
ACL is: ->Ace[7]: ->SID: S-1-5-4 (Well Known Group: NT AUTHORITY\INTERACTIVE)
ACL is: ->Ace[8]: ->AceType: ACCESS_ALLOWED_ACE_TYPE
ACL is: ->Ace[8]: ->AceFlags: 0x0
ACL is: ->Ace[8]: ->AceSize: 0x14
ACL is: ->Ace[8]: ->Mask : 0x00000002
ACL is: ->Ace[8]: ->SID: S-1-5-6 (Well Known Group: NT AUTHORITY\SERVICE)
ACL is: ->Ace[9]: ->AceType: ACCESS_ALLOWED_ACE_TYPE
ACL is: ->Ace[9]: ->AceFlags: 0x0
ACL is: ->Ace[9]: ->AceSize: 0x14
ACL is: ->Ace[9]: ->Mask : 0x00000002
ACL is: ->Ace[9]: ->SID: S-1-5-3 (Well Known Group: NT AUTHORITY\BATCH)
In the case of a level 1 info request, the desired access is 1 - an access that is granted to "NT AUTHORITY\ANONYMOUS LOGON" among others.
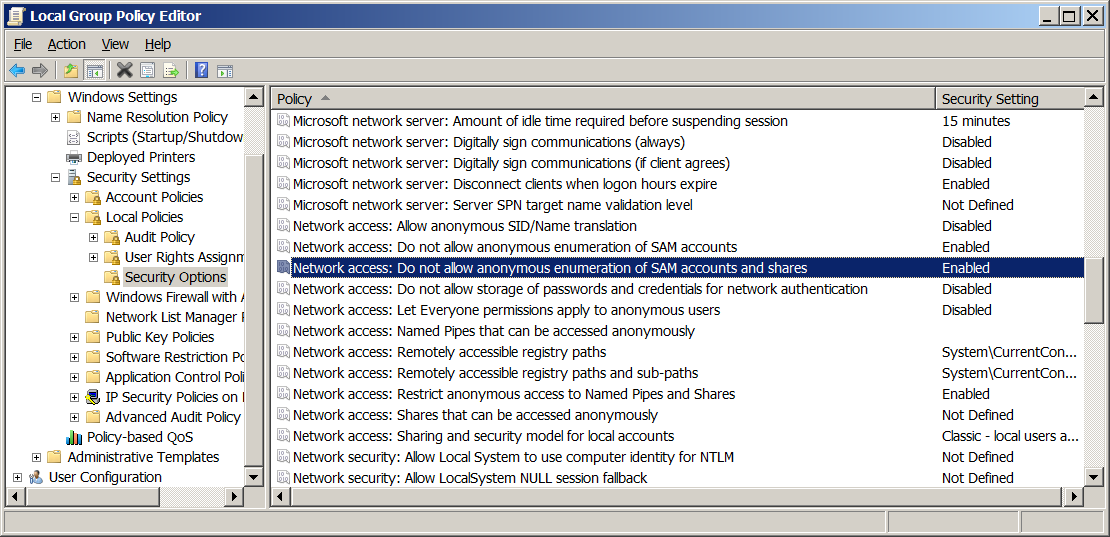
This ACL is created by code inside the LanmanServer and is not directly accessible to any tool. There may however by policies that influence the content of the ACL. Under Windows 10, at least, one such policy is:
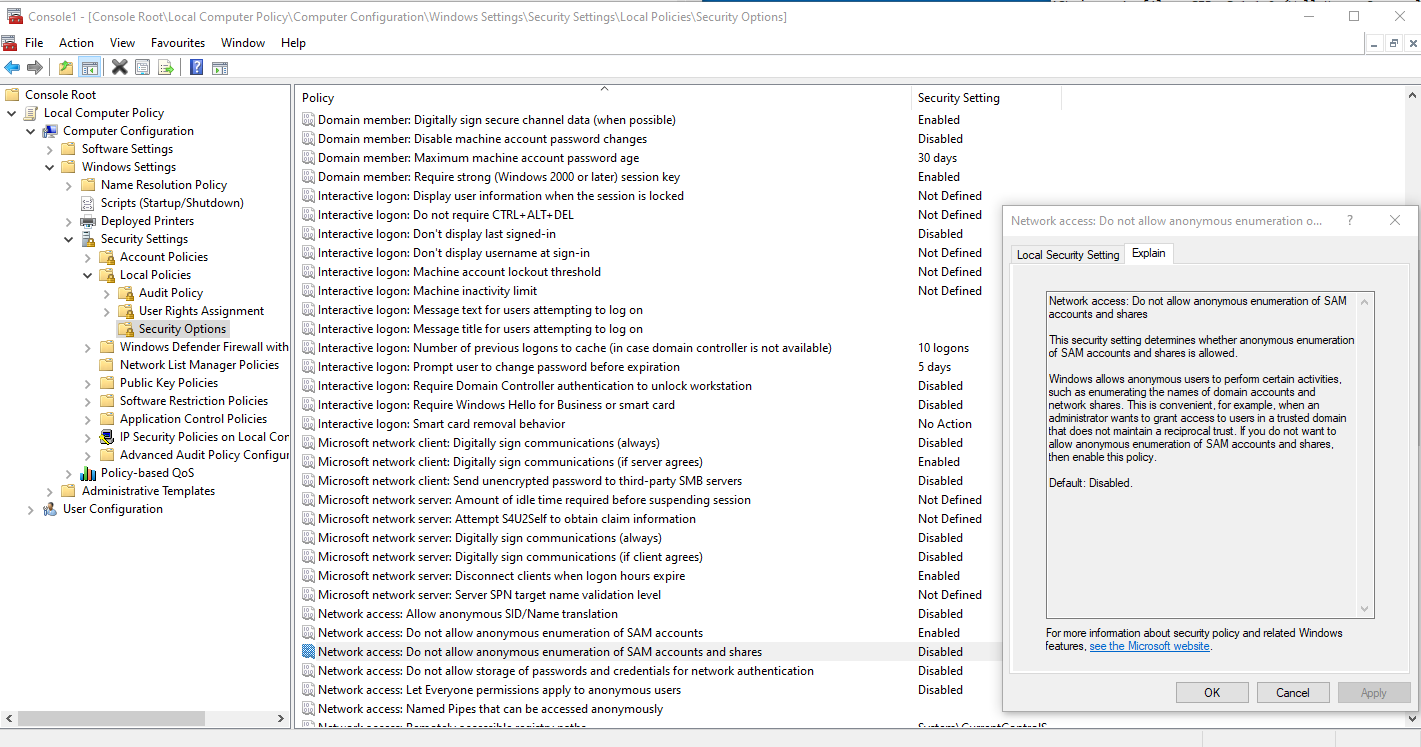
Can you check whether this policy exists in Windows 7 and, if it does exist, what its value is on B?
Gary